漏洞概要 关注数(24) 关注此漏洞
缺陷编号:wooyun-2015-0155279
漏洞标题:同程旅游接入微信支付的火车票业务存在绑定12306账号密码泄漏
相关厂商:苏州同程旅游网络科技有限公司
漏洞作者: Ra8er
提交时间:2015-11-24 17:46
修复时间:2016-01-11 15:32
公开时间:2016-01-11 15:32
漏洞类型:文件包含
危害等级:低
自评Rank:4
漏洞状态:厂商已经确认
漏洞来源: http://www.wooyun.org,如有疑问或需要帮助请联系 [email protected]
Tags标签: 无
漏洞详情
披露状态:
2015-11-24: 细节已通知厂商并且等待厂商处理中
2015-11-24: 厂商已经确认,细节仅向厂商公开
2015-12-04: 细节向核心白帽子及相关领域专家公开
2015-12-14: 细节向普通白帽子公开
2015-12-24: 细节向实习白帽子公开
2016-01-11: 细节向公众公开
简要描述:
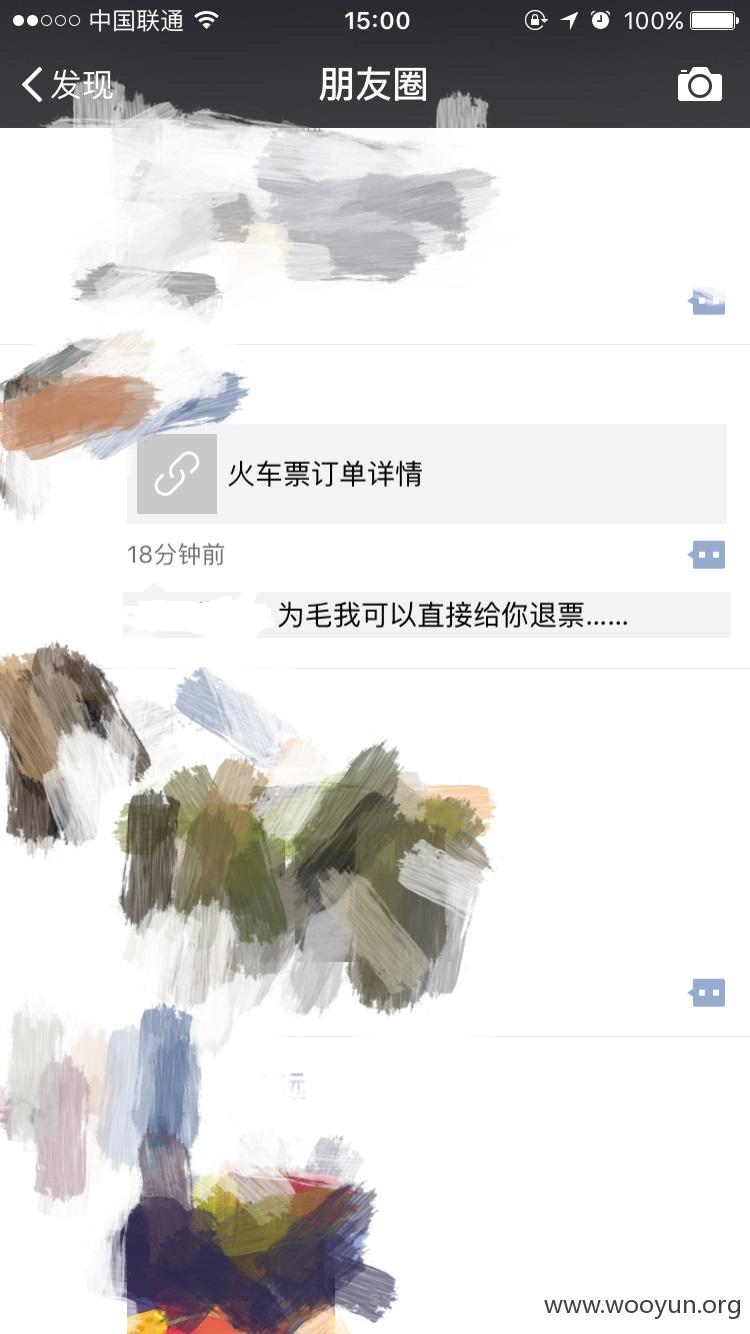
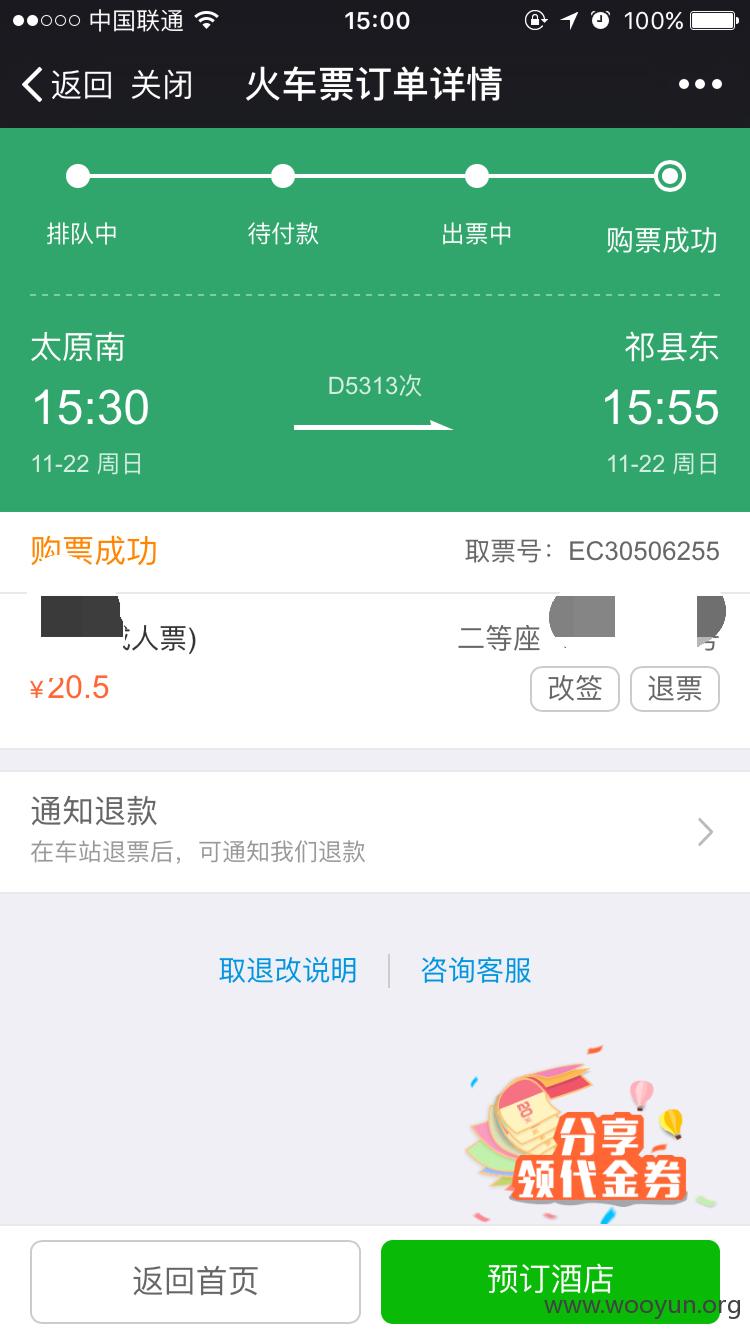
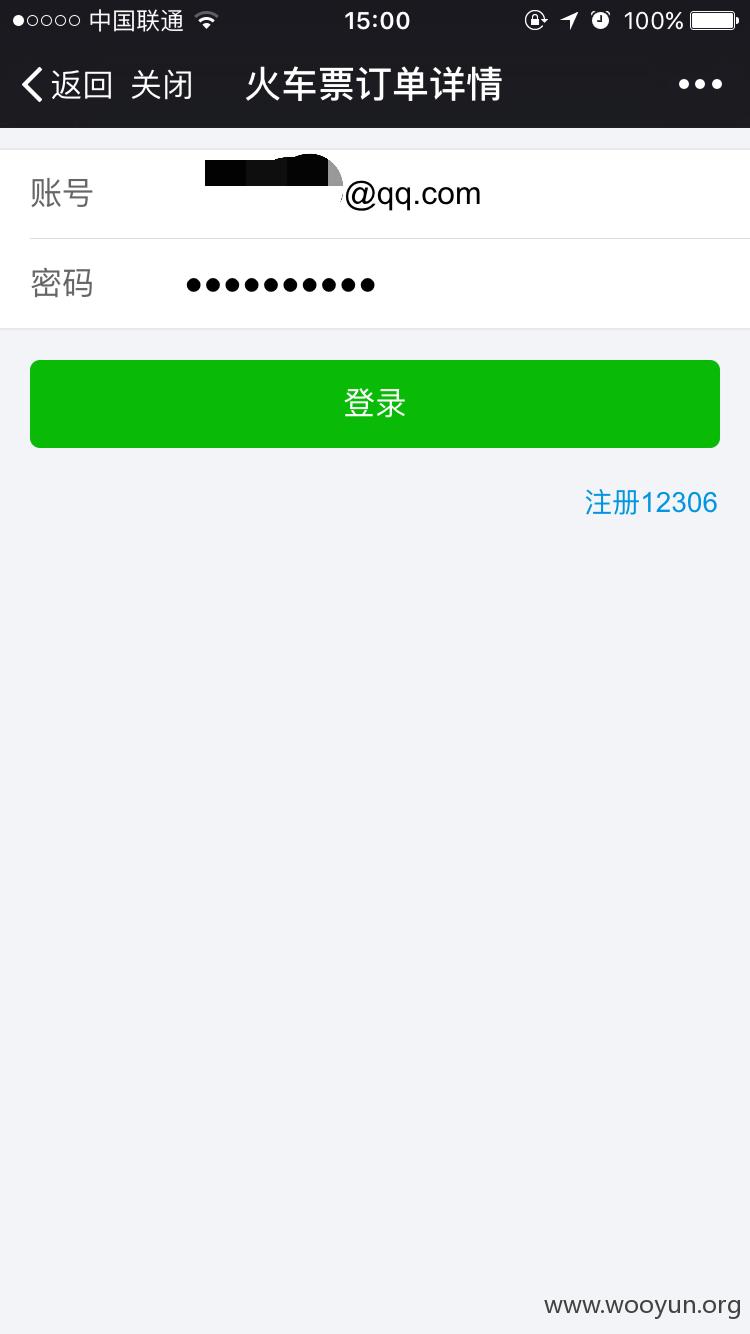
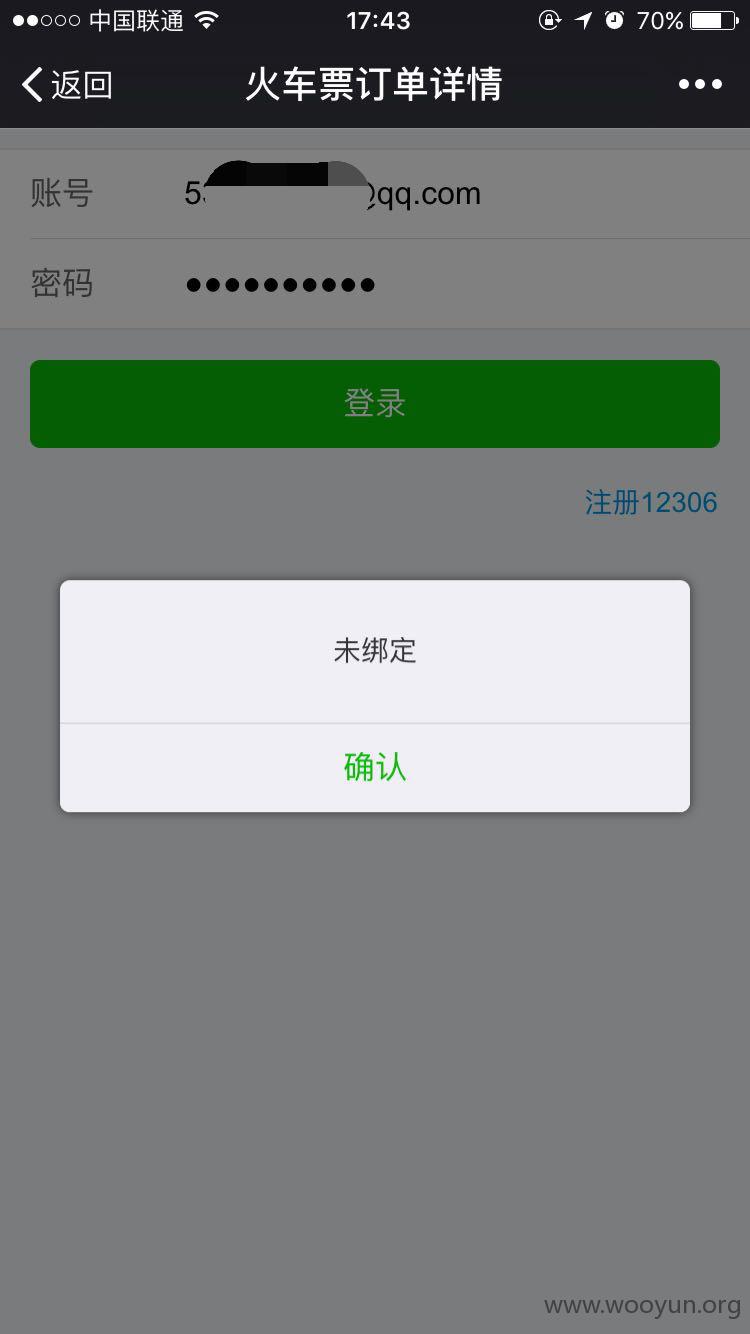
正在浏览朋友圈的看到朋友分享了一个火车票详情的页面,点进去一看,我的妈呀,竟然显示了朋友乘坐的车次以及具体座位信息,还有退票改签这些,手贱就点了退票。。然后我就醉了。。12306的账号密码竟然就是上面打印着
详细说明:
好久没提交漏洞,手抖没点匿名提交,求帮忙匿名,谢谢。
正在浏览朋友圈的看到朋友分享了一个火车票详情的页面,点进去一看,
我的妈呀,竟然显示了朋友乘坐的车次以及具体座位信息,还有退票改签这些
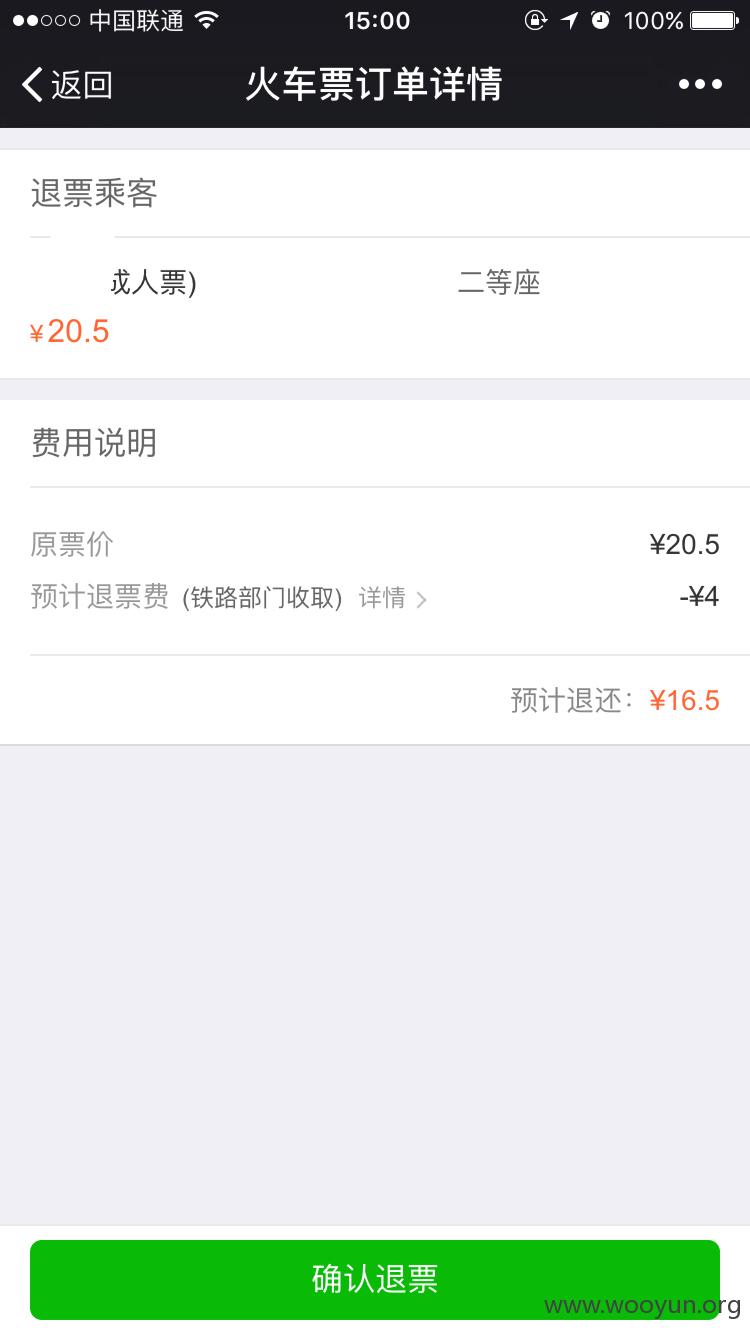
贱就点了退票。。然后又手贱的点了确认退票。。然后我就醉了。。12306的账号密码竟然就是上面打印着
然后就手贱的抓了个包。。。
虽然最后没登陆进去。。但是这个错误也太低级了。。。
这个在微信购买完本来有一个分享获取代金券的一个分享行为,他们预想的是这样的链接
https://open.weixin.qq.com/connect/oauth2/authorize?appid=wx3827070276e49e30&redirect_uri=http://wx.17u.cn/train/trainquery.html?showwxpaytitle=2&response_type=code&scope=snsapi_base&state=123#wechat_redirect
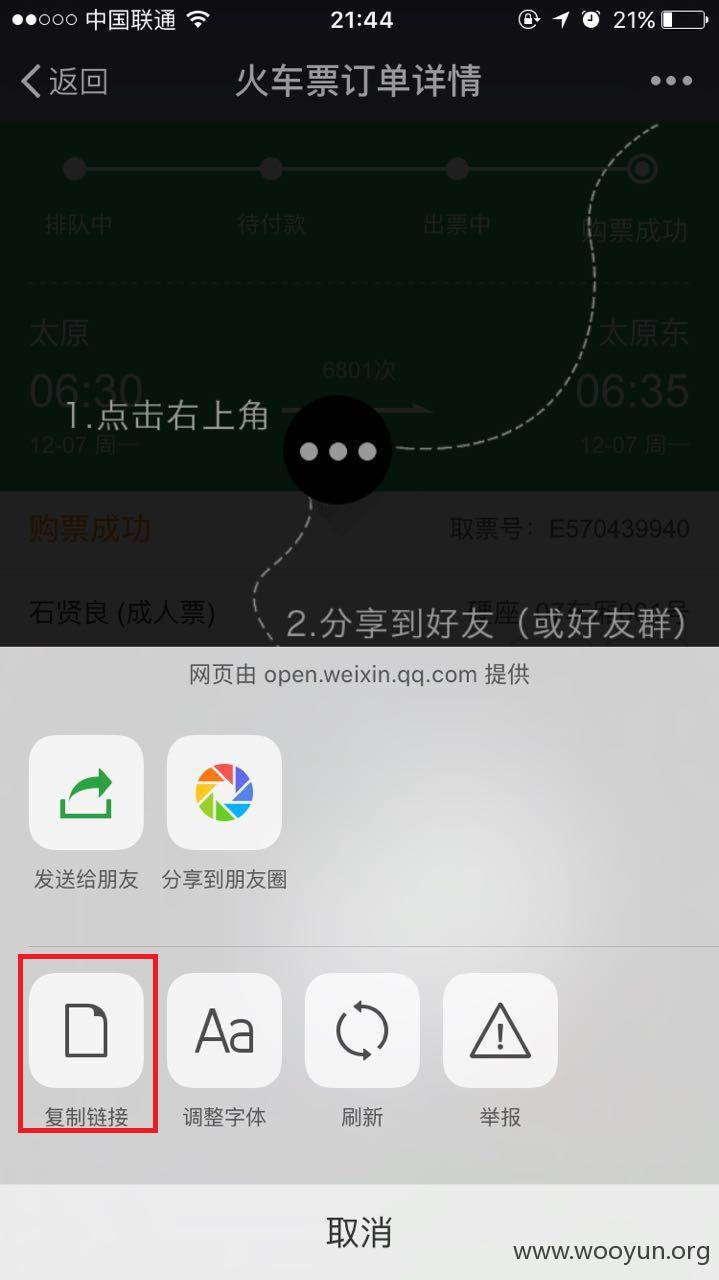
但是在分享的时候点击复制链接
复制出来的链接却是这个http://wx.17u.cn/train/TrainOrderDetail.html?orderId=Ya3vWuZreT3p0TWFGIBCig%3D%3D&bookerId=wa8q4T8svhf1R2CqZadpug%3D%3D
最后这个问题到底归同程旅游管还是腾讯微信管我就不知道了
漏洞证明:
补上复测地址,为了这个复测地址,我又去买了一张火车票。。。PS:这个地址一定要在微信客户端上打开。。http://wx.17u.cn/train/TrainOrderDetail.html?orderId=Ya3vWuZreT3p0TWFGIBCig%3D%3D&bookerId=wa8q4T8svhf1R2CqZadpug%3D%3D
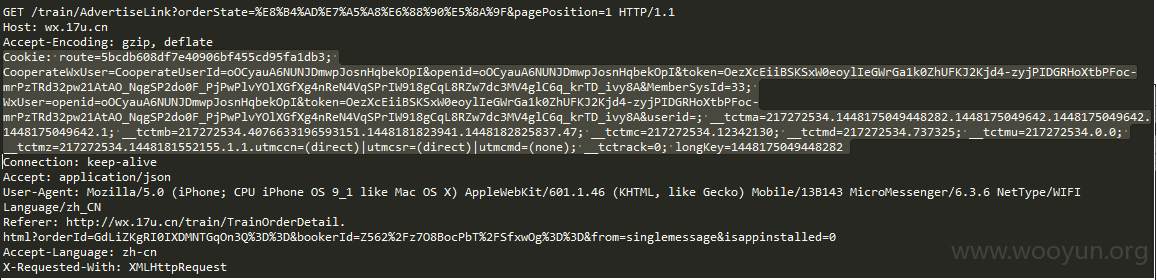
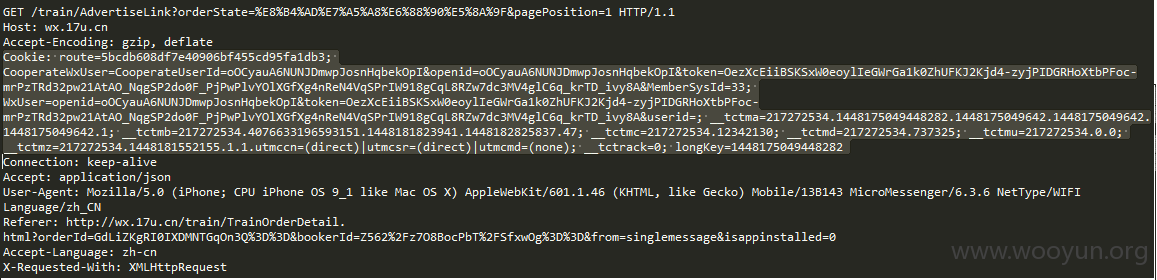
再附上抓包抓的SessionId
http://vstlog.17usoft.com/TrackEvent/TrackEvent.ashx?TrackEvent={"LoginKey":1448277521918614,"LoginCount":1,"SessionId":3282415257649152,"PageCount":2,"Category":"click","Action":"12306denglu","FromPage":"wx.17u.cn/train/TrainOrderDetail.html?orderId=Ya3vWuZreT3p0TWFGIBCig==&bookerId=wa8q4T8svhf1R2CqZadpug==","Label":"wxtrain","Value":""}&_v=1&dt=1448278011012
以及查看火车票订单的请求
GET /TrackEvent/TrackEvent.ashx?TrackEvent={%22LoginKey%22:1448277521918614,%22LoginCount%22:1,%22SessionId%22:3282415257649152,%22PageCount%22:2,%22Category%22:%22click%22,%22Action%22:%2212306denglu%22,%22FromPage%22:%22wx.17u.cn%2Ftrain%2FTrainOrderDetail.html%3ForderId%3DYa3vWuZreT3p0TWFGIBCig%253D%253D%26bookerId%3Dwa8q4T8svhf1R2CqZadpug%253D%253D%22,%22Label%22:%22wxtrain%22,%22Value%22:%22%22}&_v=1&dt=1448278011012 HTTP/1.1
Host: vstlog.17usoft.com
Connection: keep-alive
Proxy-Connection: keep-alive
Accept: */*
User-Agent: Mozilla/5.0 (iPhone; CPU iPhone OS 9_1 like Mac OS X) AppleWebKit/601.1.46 (KHTML, like Gecko) Mobile/13B143 MicroMessenger/6.3.6 NetType/WIFI Language/zh_CN
Accept-Language: zh-cn
Referer: http://wx.17u.cn/train/TrainOrderDetail.html?orderId=Ya3vWuZreT3p0TWFGIBCig%3D%3D&bookerId=wa8q4T8svhf1R2CqZadpug%3D%3D
Accept-Encoding: gzip, deflate
然后就是获取对方订单的请求
POST /train/getOrder HTTP/1.1
Host: wx.17u.cn
Accept: application/json
Proxy-Connection: keep-alive
X-Requested-With: XMLHttpRequest
Accept-Encoding: gzip, deflate
Accept-Language: zh-cn
Content-Type: application/x-www-form-urlencoded
Origin: http://wx.17u.cn
Content-Length: 78
Connection: keep-alive
User-Agent: Mozilla/5.0 (iPhone; CPU iPhone OS 9_1 like Mac OS X) AppleWebKit/601.1.46 (KHTML, like Gecko) Mobile/13B143 MicroMessenger/6.3.6 NetType/WIFI Language/zh_CN
Referer: http://wx.17u.cn/train/TrainOrderDetail.html?orderId=Ya3vWuZreT3p0TWFGIBCig%3D%3D&bookerId=wa8q4T8svhf1R2CqZadpug%3D%3D
Cookie: route=52df3a616d38b5cd0a7627a863931ae1; __tctma=217272534.1448277521918614.1448277521575.1448277521575.1448277521575.1; __tctmb=217272534.3282415257649152.1448277521575.1448277521575.1; __tctmc=217272534.155532413; __tctmd=217272534.737325; __tctmu=217272534.0.0; __tctmz=217272534.1448277521575.1.1.utmccn=(direct)|utmcsr=(direct)|utmcmd=(none); __tctrack=0; longKey=1448277521918614
orderId=Ya3vWuZreT3p0TWFGIBCig%3D%3D&memberId=wa8q4T8svhf1R2CqZadpug%253D%253D
最后贴图是抓到的cookies
修复方案:
版权声明:转载请注明来源 Ra8er@乌云
漏洞回应
厂商回应:
危害等级:中
漏洞Rank:8
确认时间:2015-11-24 17:55
厂商回复:
感谢Ra8er的提交,该漏洞在之前有外部人员私下报告过,并且也通知了项目组修复,只能说我们的监督还不到位,再次感谢,礼品卡送上!
最新状态:
暂无