目标:好贷网APP——信贷圈
注册信贷经理,登陆后,以下数据包可查看本人的信贷订单
本人账号无客户,故返回details为空[]:
其中,POST中的xid为被查询经理的id,此时只需枚举下xid,即可查看其它经理的订单信息。
根据这个原理,写了个Python批量操作~此处只查询id为(220821,221821)之间的~
结果输出:
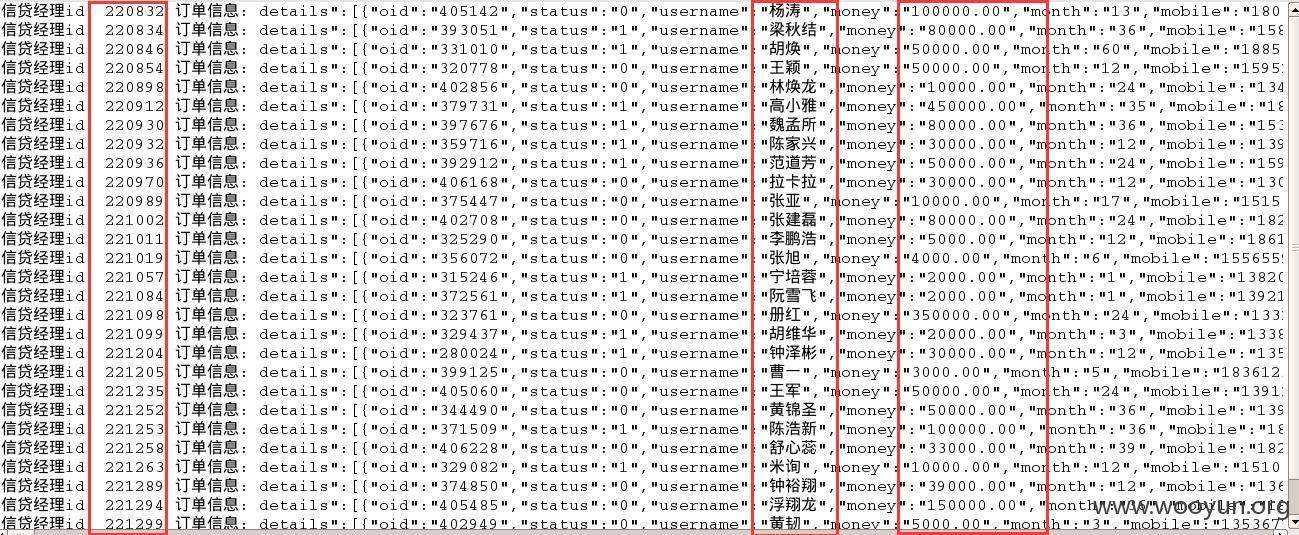
图中每行分别为一个信贷经理,第一个红框中的为每个信贷经理的ID,第二个红框中为各个经理的订单及借贷人信息,包括姓名、手机、借贷金额、房产等信息;由于每行后面数据太多,故截取了图中的第一个借贷经理(第一行,ID为220832)的信息展开,如下图:

篇幅关系,其他行的就不展开了~
同理:以下数据包为获取信贷经理的客户
同样修改xid可枚举所有信贷经理的所有客户信息,包括姓名、手机、借贷金额、房产等
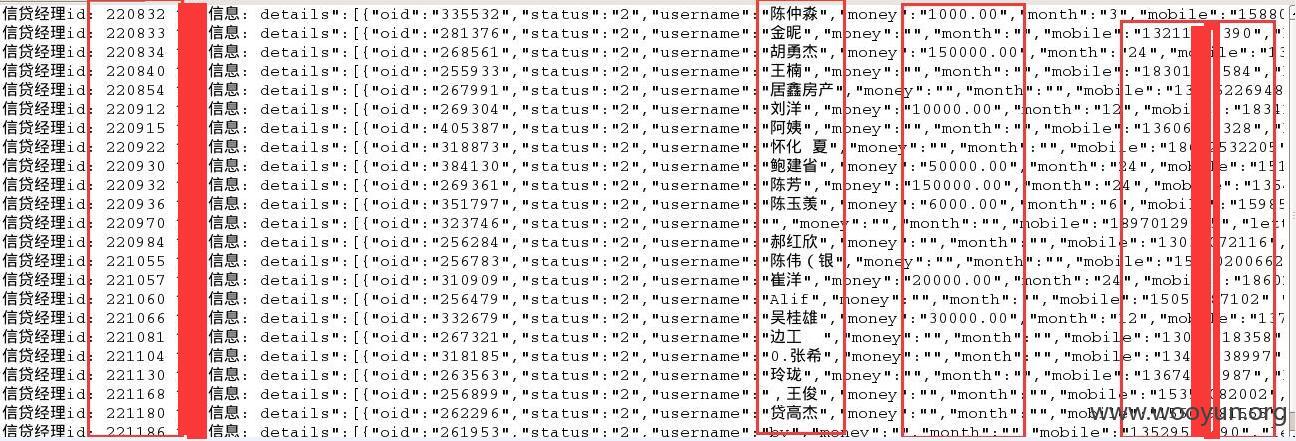
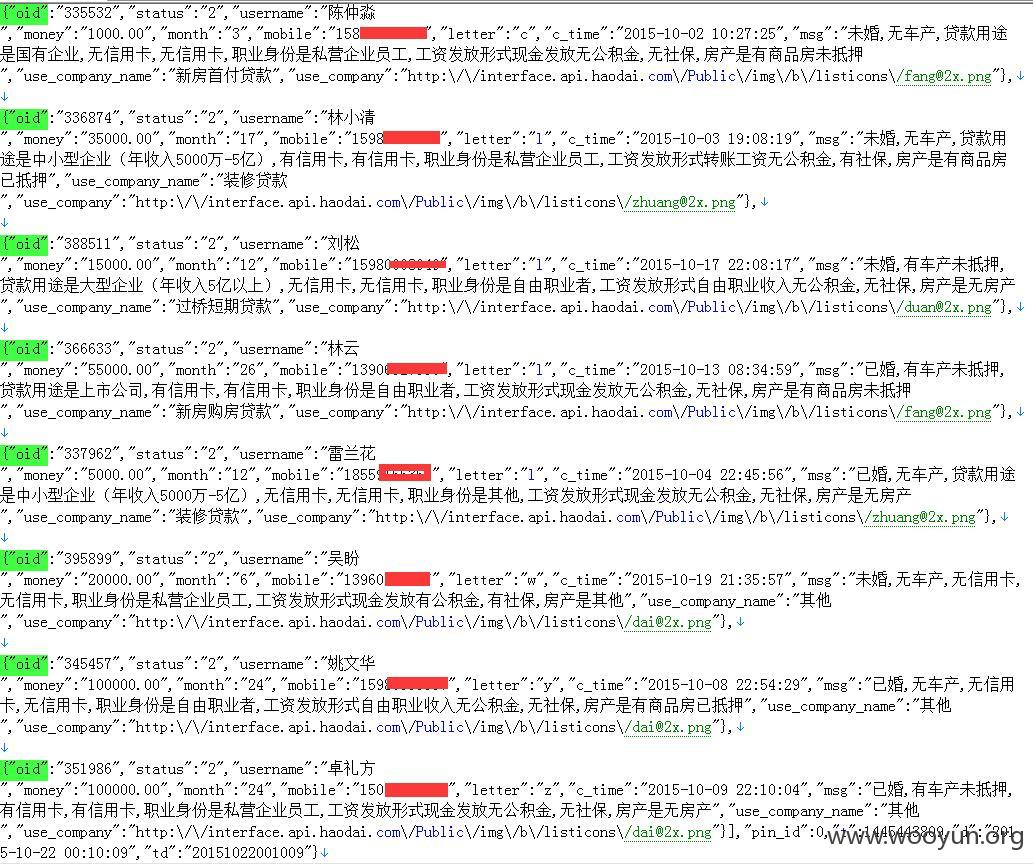
金融安全事关财产,其他数据就不挖了~






