以收费电影《小时代4:灵魂尽头》为例,
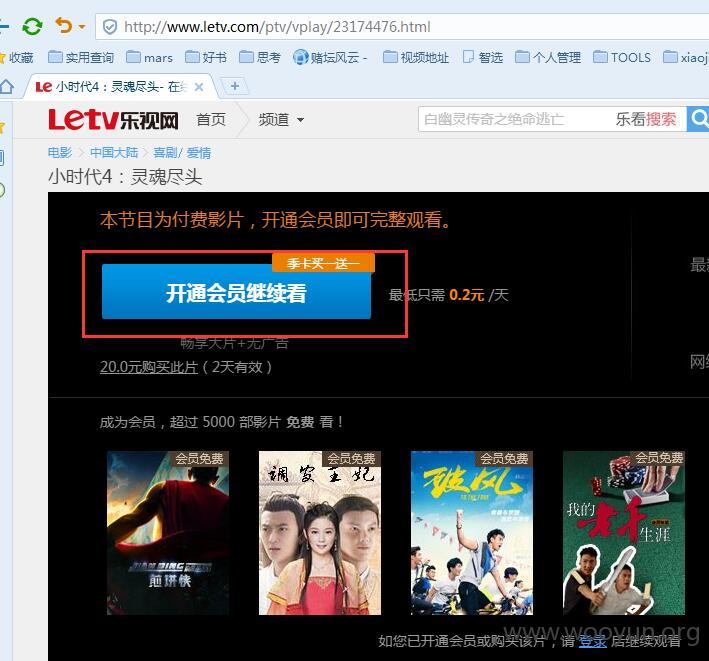
地址 http://www.letv.com/ptv/vplay/23174476.html 那么vid=23174476;
通过API接口 http://api.mob.app.letv.com/play?vid=23174476 可获取各个清晰度的解析地址,
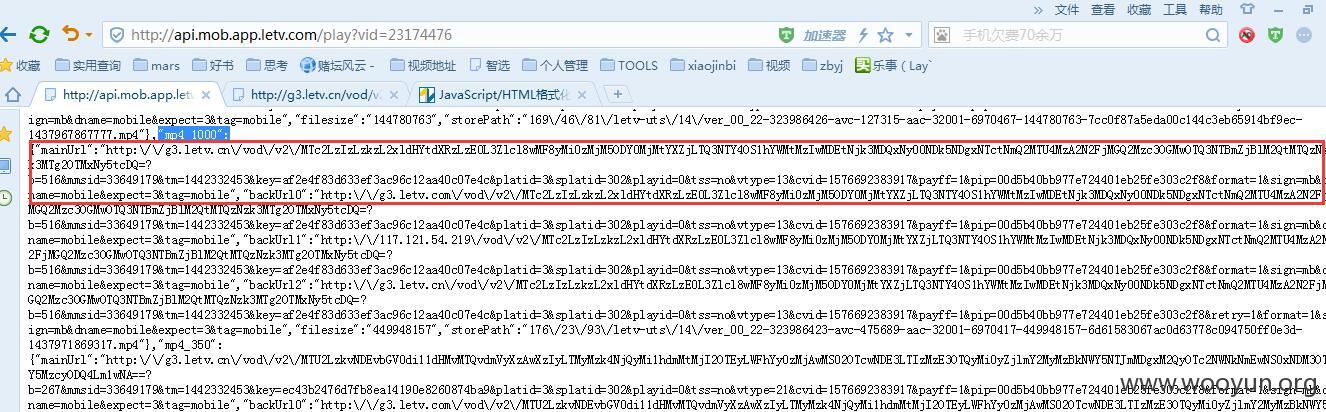
我们以MP4_180的mainurl为例:
,注意要把“\”符号清理掉,得到地址
找一个离自己近的地址,一定注意拷贝完整地址,结尾参数是cips,不明显的话可以放到JS格式化工具里面,访问将得到下载地址
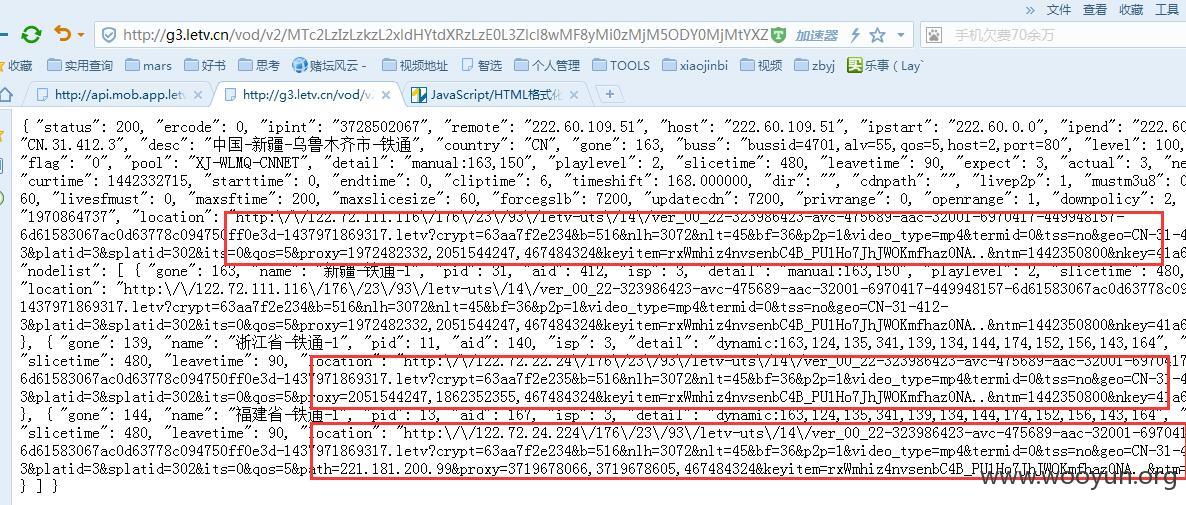
同样把“\”符号清理掉,得到地址
放到迅雷里面下载看看,速度是很快的,
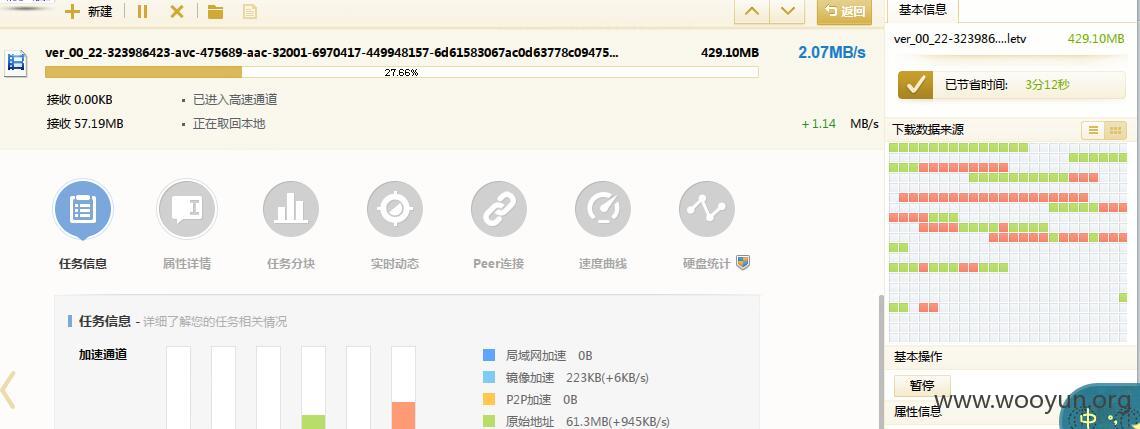
下载完播放看看,
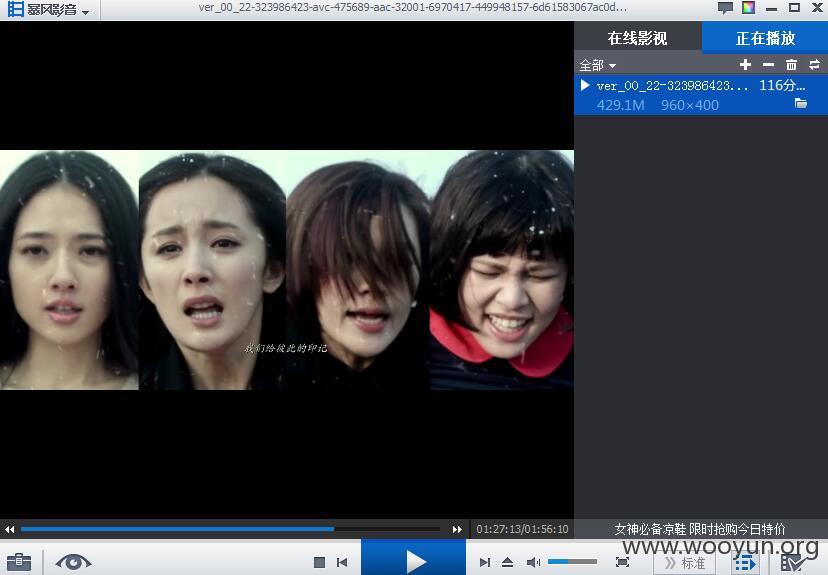
注意地址是时刻变化的,再现的时候需要按照当时的地址进行解析
以收费电影《小时代4:灵魂尽头》为例,
通过api得到地址
迅雷下载,

播放视频,








