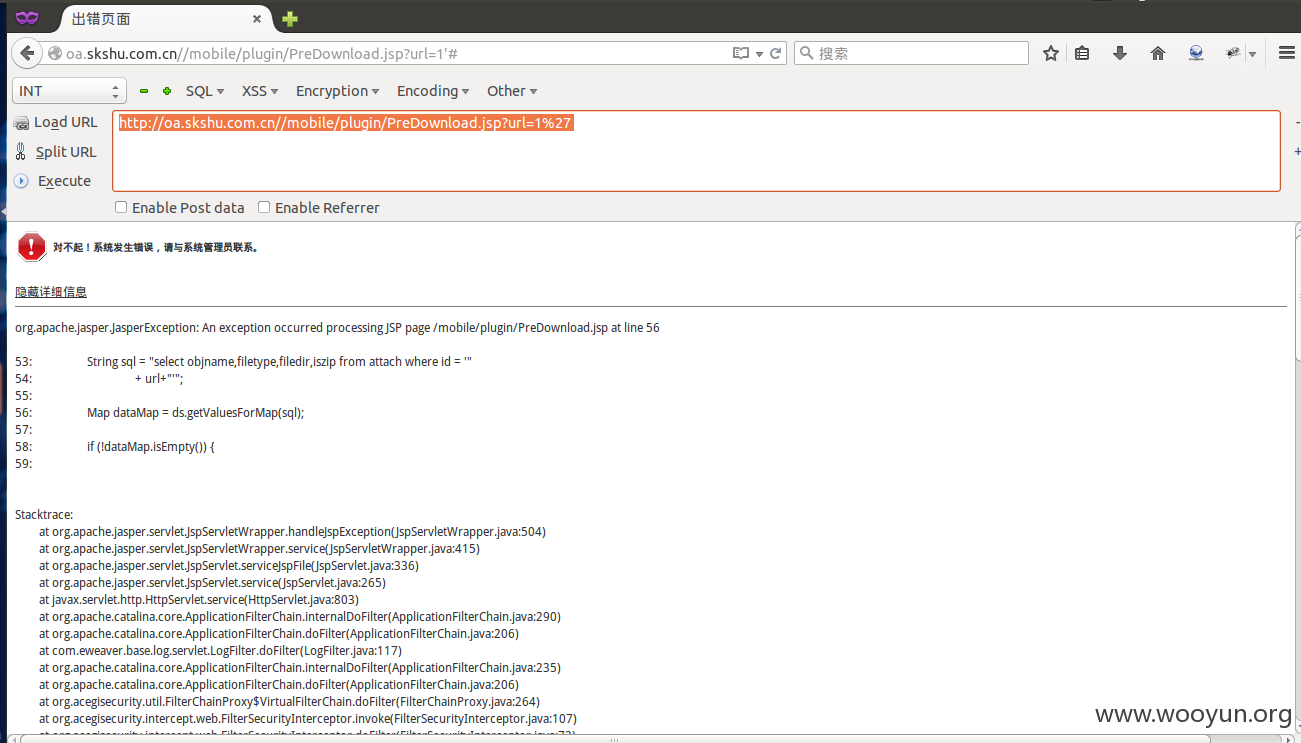
问题出在mobile\plugin中的PreDownload.jsp文件
其中
这里对url并没有过滤
可能导致sql注入
这里我们首先以官方为例
http://**.**.**.**:9085/mobile/plugin/PreDownload.jsp?url=1
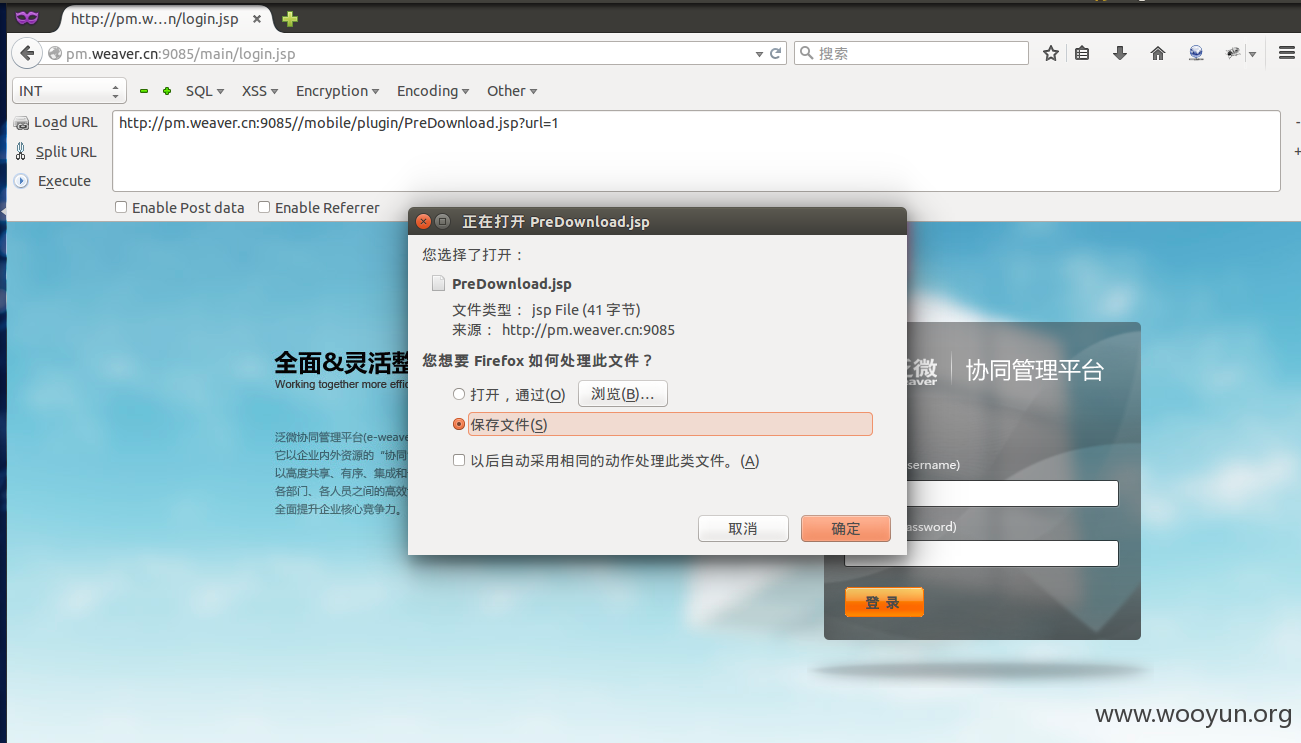
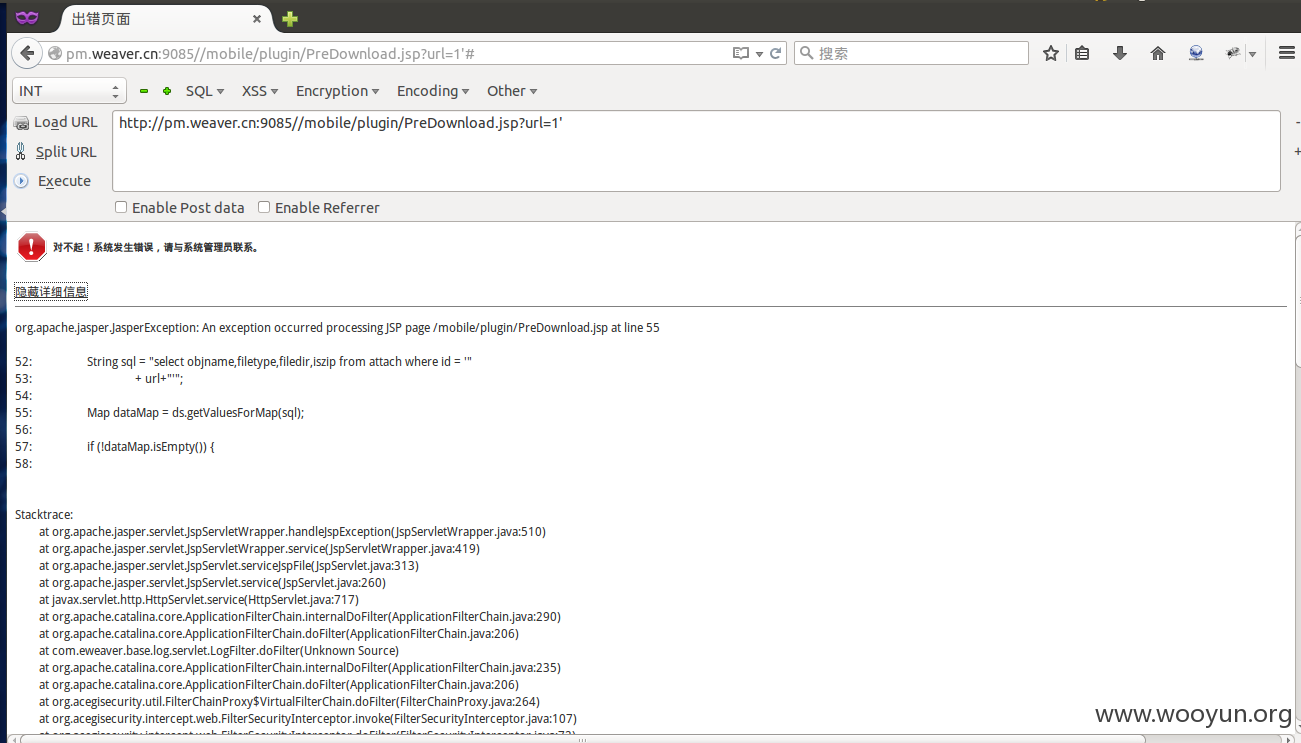
直接sqlmap
数据库
与http://**.**.**.**/bugs/wooyun-2015-0124589中的一致
再举几个案例
http://**.**.**.**/mobile/plugin/PreDownload.jsp?url=1
数据库
http://**.**.**.**//mobile/plugin/PreDownload.jsp?url=1
数据库
http://10.0.0.*/mobile/plugin/PreDownload.jsp?url=1
数据库
http://**.**.**.**/mobile/plugin/PreDownload.jsp?url=1
数据库
http://**.**.**.**//mobile/plugin/PreDownload.jsp?url=1%27