#1 信息泄露源
由于唱吧主站服务器WEB服务端配置缺陷,以及开发人员代码上线安全意识不足,直接将版本控制软件SVN所残留的信息发布到了线上。
WooYun: Changba-inc唱吧svn敏感信息泄露
白帽子曾经报告过一个svn信息泄露威胁,但唱吧的修复方案只是简单的针对http://访问源进行了限制,而对https的配置并未生效,导致仍然存在缺陷。
https://changba.com/.svn/entries
#2 写个自动化工具扫描,并爬行泄露的源码
#3 获取了源码,即可针对代码进行代码审计或其它漏洞挖掘
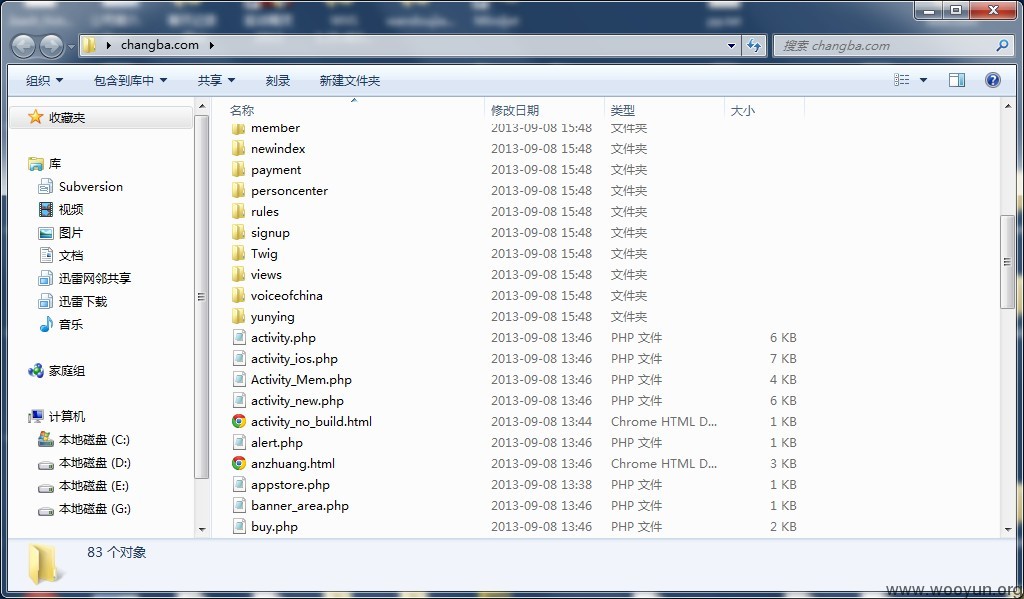
#4 针对源码挖掘,发现其中一个上传漏洞
\competition\common_functions.php 159行