漏洞概要
关注数(24)
关注此漏洞
漏洞标题:ChinaCache 监控服务CACTI管理后台弱口令 (可ROOT服务器)
提交时间:2013-07-26 13:54
修复时间:2013-09-09 13:55
公开时间:2013-09-09 13:55
漏洞类型:服务弱口令
危害等级:高
自评Rank:20
漏洞状态:厂商已经确认
Tags标签:
无
漏洞详情
披露状态:
2013-07-26: 细节已通知厂商并且等待厂商处理中
2013-07-26: 厂商已经确认,细节仅向厂商公开
2013-08-05: 细节向核心白帽子及相关领域专家公开
2013-08-15: 细节向普通白帽子公开
2013-08-25: 细节向实习白帽子公开
2013-09-09: 细节向公众公开
简要描述:
该服务器所处机房很高端,网易、搜狐、新浪、360、百度等等大厂商都有服务器在。
如果被间接利用,危害是非常大的。
详细说明:
CACTI 地址:
http://220.181.47.151/
弱口令
admin:admin
guest:admin
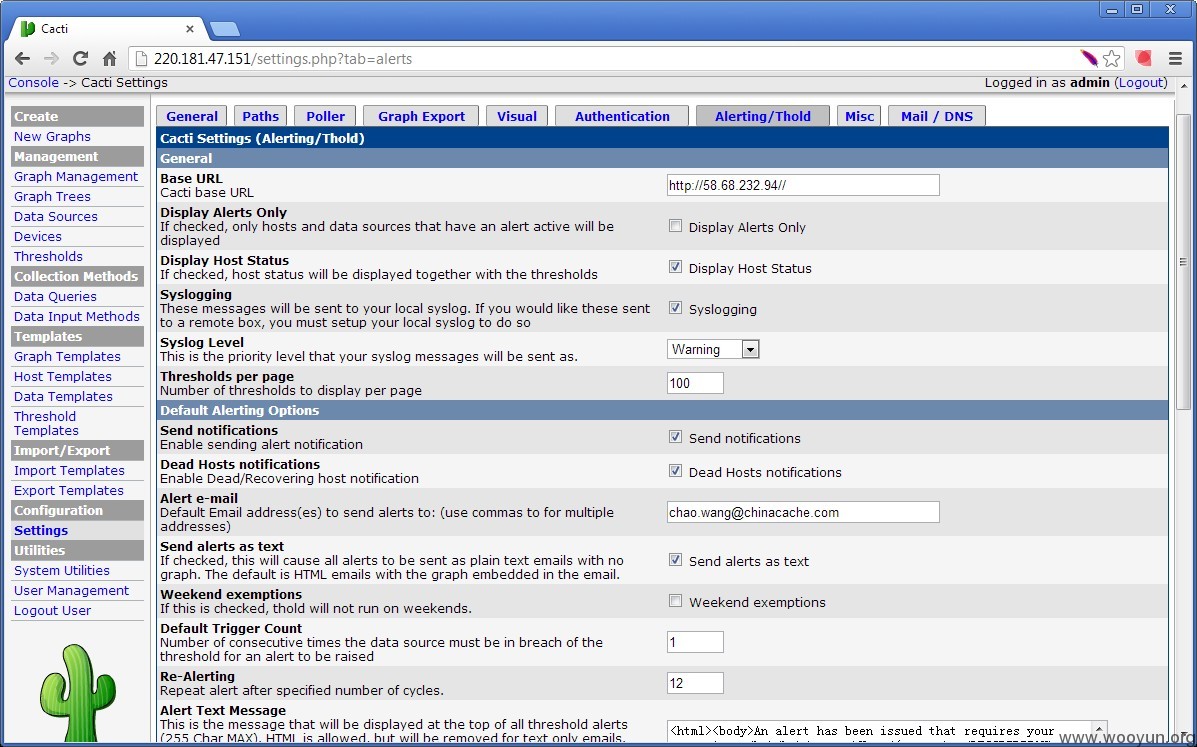
漏洞证明:
修复方案:
#1 CACTI 管理地址做严格的访问控制规则
#2 杜绝默认口令。
版权声明:转载请注明来源 猪猪侠@乌云
漏洞回应
厂商回应:
危害等级:低
漏洞Rank:5
确认时间:2013-07-26 17:18
厂商回复:
感谢 @猪猪侠 提报的安全漏洞。
由于该设备不属于重要系统,不会对蓝汛造成重大安全影响,因此根据乌云 Rand 评级制度给予“低”的评价,但给予“低”的最高分值 5 分表示感谢。
最新状态:
暂无



