漏洞概要 关注数(24) 关注此漏洞
缺陷编号:wooyun-2013-026787
漏洞标题:优酷某接口任意用户信息获取漏洞,可获取指定密码
相关厂商:优酷
漏洞作者: 猪猪侠
提交时间:2013-06-24 17:00
修复时间:2013-08-08 17:00
公开时间:2013-08-08 17:00
漏洞类型:敏感信息泄露
危害等级:高
自评Rank:20
漏洞状态:厂商已经确认
漏洞来源: http://www.wooyun.org,如有疑问或需要帮助请联系 [email protected]
Tags标签: 无
漏洞详情
披露状态:
2013-06-24: 细节已通知厂商并且等待厂商处理中
2013-06-24: 厂商已经确认,细节仅向厂商公开
2013-07-04: 细节向核心白帽子及相关领域专家公开
2013-07-14: 细节向普通白帽子公开
2013-07-24: 细节向实习白帽子公开
2013-08-08: 细节向公众公开
简要描述:
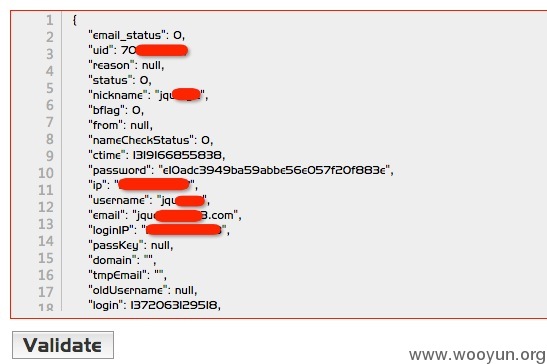
优酷系统的API,在输出用户信息时未进行严格的业务逻辑设计,直接输出了用户的邮箱、用户名、用户密码、用户登录IP、用户手机、QQ、MSN等敏感信息。
详细说明:
#1 访问老罗的个人主页
#2 个人主页页面会自动请求如下API,获取用户的个人主页访问量
id_425736_md5,id后的数字为用户的个人真实ID
# 构造请求获取用户数据
# 此处用测试帐号演示
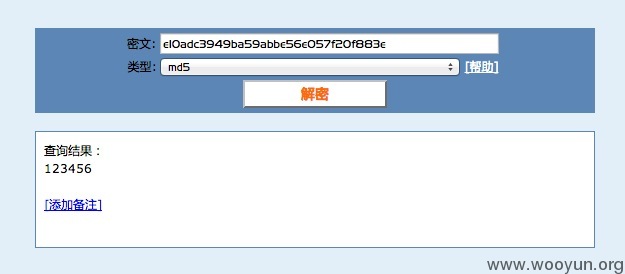
漏洞证明:
获得罗永浩的登录邮箱为:[email protected]
修复方案:
不该输出的信息还是尽量不要输出。
版权声明:转载请注明来源 猪猪侠@乌云
漏洞回应
厂商回应:
危害等级:高
漏洞Rank:20
确认时间:2013-06-24 17:09
厂商回复:
修复中
最新状态:
暂无